Posted on March 6, 2010
Here is a blast from the past. The message contains a zip file with a Poison Ivy executable - a fairly unsophisticated method of delivery, comparing to the methods we see these days. I found the fact that the message importance is set to low a bit unusual and amusing. Note the date of the attack - 2008.Link updated: Jan 18, 2023
http://contagio.deependresearch.org/APT/China/Poison+Ivy+EXE+105C80E404324938EAE633934EE44ED1+RSIS-exe.zip (email me if you need a password - address is in the profile)

-----Original Message-----
From: RSISPubllcation [mailto:RSISPubllcation@NTU.EDU.SG]
Sent: Tuesday, May 06, 2008 9:10 PM
To: XXXXXXXXXXXXX
Subject: RSIS Commentary 54/2009 Ending the LTTE
Importance: Low
Dear All,
1. We are pleased to attach for your reading pleasure the following RSIS Commentary by Arabinda Acharya entitled Ending the LTTE: Recipe for counter-terrorism?
2. Synopsis:
Despite the very high cost in terms of lives lost and internal displacements, the military victory against the LTTE is a lesson in warfare for countries fighting insurgency and terrorism.
Regards,
RSISPublication,
for Yang Razali Kassim
Senior Fellow &
Editor RSIS Commentaries
http://www.virustotal.com/analisis/b71040cfa7545804d02afb8bb39639cf9c5dfd7439b29b6d3cf7a1ea8b9a5efc-1267933534
Virustotal results - 40/42 (not sure why eSafe and eTrust-Vet don't detect it :)
a-squared 4.5.0.50 2010.03.06 Trojan.Win32.Agent!IK
AhnLab-V3 5.0.0.2 2010.03.06 Win-Trojan/Agent.45056.AJR
AntiVir 8.2.1.180 2010.03.05 TR/Agent.clsw
Antiy-AVL 2.0.3.7 2010.03.05 Trojan/Win32.Agent.gen
Authentium 5.2.0.5 2010.03.06 W32/Trojan2.HSKK
Avast 4.8.1351.0 2010.03.06 Win32:Trojan-gen
Avast5 5.0.332.0 2010.03.06 Win32:Trojan-gen
AVG 9.0.0.787 2010.03.06 Agent2.LBZ
BitDefender 7.2 2010.03.07 Trojan.Generic.2039983
CAT-QuickHeal 10.00 2010.03.06 Trojan.Agent.ckug
ClamAV 0.96.0.0-git 2010.03.06 Trojan.Agent-117052
Comodo 4091 2010.02.28 Heur.Suspicious
DrWeb 5.0.1.12222 2010.03.07 Trojan.Siggen.14707
F-Prot 4.5.1.85 2010.03.06 W32/Trojan2.HSKK
F-Secure 9.0.15370.0 2010.03.07 Trojan.Generic.2039983
Fortinet 4.0.14.0 2010.03.06 W32/Agent.CLSW!tr
GData 19 2010.03.07 Trojan.Generic.2039983
Ikarus T3.1.1.80.0 2010.03.06 Trojan.Win32.Agent
Jiangmin 13.0.900 2010.03.06 Trojan/Agent.cmzc
K7AntiVirus 7.10.990 2010.03.04 Trojan.Win32.Agent.clsw
Kaspersky 7.0.0.125 2010.03.07 Trojan.Win32.Agent.clsw
McAfee 5912 2010.03.06 Generic BackDoor.m
McAfee+Artemis 5912 2010.03.06 Generic BackDoor.m
McAfee-GW-Edition 6.8.5 2010.03.07 Trojan.Agent.clsw
Microsoft 1.5502 2010.03.06 Backdoor:Win32/Poisonivy.E
NOD32 4921 2010.03.06 probably a variant of Win32/Agent
Norman 6.04.08 2010.03.06 W32/Agent.SKBD
nProtect 2009.1.8.0 2010.03.06 Trojan/W32.Agent.45056.MQ
Panda 10.0.2.2 2010.03.06 Trj/Downloader.MDW
PCTools 7.0.3.5 2010.03.04 Backdoor.Trojan
Prevx 3.0 2010.03.07 High Risk System Back Door
Rising 22.37.06.01 2010.03.07 Trojan.DL.Win32.Undef.eyn
Sophos 4.51.0 2010.03.06 Mal/Generic-A
Sunbelt 5776 2010.03.07 Trojan.Win32.Generic!BT
Symantec 20091.2.0.41 2010.03.07 Backdoor.Trojan
TheHacker 6.5.1.9.223 2010.03.07 Trojan/Agent.clsw
TrendMicro 9.120.0.1004 2010.03.07 BKDR_POISON.UG
VBA32 3.12.12.2 2010.03.05 Trojan.Win32.Agent.ckun
ViRobot 2010.3.5.2214 2010.03.05 Trojan.Win32.Agent.45056.GJ
VirusBuster 5.0.27.0 2010.03.06 Trojan.Agent.LZDM
Additional information
File size: 45056 bytes
MD5...: 105c80e404324938eae633934ee44ed1
Threatexpert Report
http://www.threatexpert.com/report.aspx?md5=105c80e404324938eae633934ee44ed1
* The following Alternate Data Stream was created in the system:
# ADS name(s) ADS Size ADS Hash Alias
1 %Windir%\system32:msxmltwo.exe 45,056 bytes
MD5: 0x105C80E404324938EAE633934EE44ED1
SHA-1: 0x8D599ED218C08603C1C86CA315959286FA553C56
Backdoor.Trojan [PCTools]
Registry Modifications
* The following Registry Keys were created:
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{E09850B8-3A60-D081-6B9B-960D43D3510C}
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\PsThems
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\PsThems\Settings
* The newly created Registry Value is:
o [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{E09850B8-3A60-D081-6B9B-960D43D3510C}]
+ StubPath = "%Windir%\system32:msxmltwo.exe"
Anubis Report
http://anubis.iseclab.org/?action=result&task_id=17dcf8eaeeed8708481ff44961985d488
o RSIS.exe
+ C:\RSIS.exe
+ Started by RSIS.exe
+ Explorer.EXE
# C:\WINDOWS\Explorer.EXE
# RSIS.exe wrote to the virtual memory of this process
# IEXPLORE.EXE
* IEXPLORE.EXE
* Started by Explorer.EXE
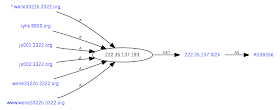
Hostname: 222.35.137.193
ISP: CHINA RAILWAY TELECOMMUNICATIONS CENTER
Organization: CHINA RAILWAY TELECOMMUNICATIONS CENTER
Country: China
State/Region: Beijing
Information from Robtex.com

-----Original Message-----
From: RSISPubllcation [mailto:RSISPubllcation@NTU.EDU.SG]
Sent: Tuesday, May 06, 2008 9:10 PM
To: XXXXXXXXXXXXX
Subject: RSIS Commentary 54/2009 Ending the LTTE
Importance: Low
Dear All,
1. We are pleased to attach for your reading pleasure the following RSIS Commentary by Arabinda Acharya entitled Ending the LTTE: Recipe for counter-terrorism?
2. Synopsis:
Despite the very high cost in terms of lives lost and internal displacements, the military victory against the LTTE is a lesson in warfare for countries fighting insurgency and terrorism.
Regards,
RSISPublication,
for Yang Razali Kassim
Senior Fellow &
Editor RSIS Commentaries
http://www.virustotal.com/analisis/b71040cfa7545804d02afb8bb39639cf9c5dfd7439b29b6d3cf7a1ea8b9a5efc-1267933534
Virustotal results - 40/42 (not sure why eSafe and eTrust-Vet don't detect it :)
a-squared 4.5.0.50 2010.03.06 Trojan.Win32.Agent!IK
AhnLab-V3 5.0.0.2 2010.03.06 Win-Trojan/Agent.45056.AJR
AntiVir 8.2.1.180 2010.03.05 TR/Agent.clsw
Antiy-AVL 2.0.3.7 2010.03.05 Trojan/Win32.Agent.gen
Authentium 5.2.0.5 2010.03.06 W32/Trojan2.HSKK
Avast 4.8.1351.0 2010.03.06 Win32:Trojan-gen
Avast5 5.0.332.0 2010.03.06 Win32:Trojan-gen
AVG 9.0.0.787 2010.03.06 Agent2.LBZ
BitDefender 7.2 2010.03.07 Trojan.Generic.2039983
CAT-QuickHeal 10.00 2010.03.06 Trojan.Agent.ckug
ClamAV 0.96.0.0-git 2010.03.06 Trojan.Agent-117052
Comodo 4091 2010.02.28 Heur.Suspicious
DrWeb 5.0.1.12222 2010.03.07 Trojan.Siggen.14707
F-Prot 4.5.1.85 2010.03.06 W32/Trojan2.HSKK
F-Secure 9.0.15370.0 2010.03.07 Trojan.Generic.2039983
Fortinet 4.0.14.0 2010.03.06 W32/Agent.CLSW!tr
GData 19 2010.03.07 Trojan.Generic.2039983
Ikarus T3.1.1.80.0 2010.03.06 Trojan.Win32.Agent
Jiangmin 13.0.900 2010.03.06 Trojan/Agent.cmzc
K7AntiVirus 7.10.990 2010.03.04 Trojan.Win32.Agent.clsw
Kaspersky 7.0.0.125 2010.03.07 Trojan.Win32.Agent.clsw
McAfee 5912 2010.03.06 Generic BackDoor.m
McAfee+Artemis 5912 2010.03.06 Generic BackDoor.m
McAfee-GW-Edition 6.8.5 2010.03.07 Trojan.Agent.clsw
Microsoft 1.5502 2010.03.06 Backdoor:Win32/Poisonivy.E
NOD32 4921 2010.03.06 probably a variant of Win32/Agent
Norman 6.04.08 2010.03.06 W32/Agent.SKBD
nProtect 2009.1.8.0 2010.03.06 Trojan/W32.Agent.45056.MQ
Panda 10.0.2.2 2010.03.06 Trj/Downloader.MDW
PCTools 7.0.3.5 2010.03.04 Backdoor.Trojan
Prevx 3.0 2010.03.07 High Risk System Back Door
Rising 22.37.06.01 2010.03.07 Trojan.DL.Win32.Undef.eyn
Sophos 4.51.0 2010.03.06 Mal/Generic-A
Sunbelt 5776 2010.03.07 Trojan.Win32.Generic!BT
Symantec 20091.2.0.41 2010.03.07 Backdoor.Trojan
TheHacker 6.5.1.9.223 2010.03.07 Trojan/Agent.clsw
TrendMicro 9.120.0.1004 2010.03.07 BKDR_POISON.UG
VBA32 3.12.12.2 2010.03.05 Trojan.Win32.Agent.ckun
ViRobot 2010.3.5.2214 2010.03.05 Trojan.Win32.Agent.45056.GJ
VirusBuster 5.0.27.0 2010.03.06 Trojan.Agent.LZDM
Additional information
File size: 45056 bytes
MD5...: 105c80e404324938eae633934ee44ed1
Threatexpert Report
http://www.threatexpert.com/report.aspx?md5=105c80e404324938eae633934ee44ed1
* The following Alternate Data Stream was created in the system:
# ADS name(s) ADS Size ADS Hash Alias
1 %Windir%\system32:msxmltwo.exe 45,056 bytes
MD5: 0x105C80E404324938EAE633934EE44ED1
SHA-1: 0x8D599ED218C08603C1C86CA315959286FA553C56
Backdoor.Trojan [PCTools]
Registry Modifications
* The following Registry Keys were created:
o HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{E09850B8-3A60-D081-6B9B-960D43D3510C}
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\PsThems
o HKEY_CURRENT_USER\Software\Local AppWizard-Generated Applications\PsThems\Settings
* The newly created Registry Value is:
o [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{E09850B8-3A60-D081-6B9B-960D43D3510C}]
+ StubPath = "%Windir%\system32:msxmltwo.exe"
Anubis Report
http://anubis.iseclab.org/?action=result&task_id=17dcf8eaeeed8708481ff44961985d488
o RSIS.exe
+ C:\RSIS.exe
+ Started by RSIS.exe
+ Explorer.EXE
# C:\WINDOWS\Explorer.EXE
# RSIS.exe wrote to the virtual memory of this process
# IEXPLORE.EXE
* IEXPLORE.EXE
* Started by Explorer.EXE
DNS Queries:
Name: [ js001.3322.org ]
TCP Connection Attempts
to 222.35.137.193:220
Hostname: 222.35.137.193
ISP: CHINA RAILWAY TELECOMMUNICATIONS CENTER
Organization: CHINA RAILWAY TELECOMMUNICATIONS CENTER
Country: China
State/Region: Beijing
Information from Robtex.com