The message came from the American Chamber of Commerce in China. The interesting thing about this message is that the sender is not spoofed and the headers are real, which means that the message indeed came from the mailbox of the sender @amchamchina.org, who also happens to be a real person working at
amchamchina.org - can be easily found in Google searches.
The sender name and address do not match the message signature. I have removed part of the sender's name for privacy reasons.
In this case, there are three possible scenarios:
a) someone broke into that employee mailbox and sent the malicious message (in this case, I hope the IT staff at the American Chamber of Commerce in China see this post and fix the problem)
b) the sender sent a malicious attachment not realizing it is malicious (less likely, as the attached Word document does not display readable text),
c) the sender sent the malicious message on purpose (..)
We may never know how that happened but hope it is a case of a mailbox password compromise.
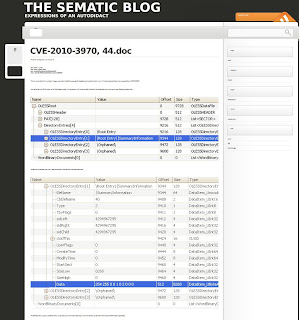
The files created by the malicious attachment generate traffic to a server in China.
Upon opening, the file will dispay garbage text if the attack fails (fully patched MS Office) and will just close without displaying any document if the exploit is successful.
The trojan that gets installed is designed for stealing information from the infected computer - files and passwords - see the detailed analysis below.