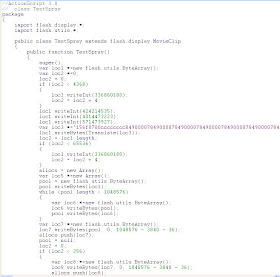
According to Cédric Gilbert (SkyRecon R&D), the shellcode’s last command include a “taskkill /im hwp.exe”. This hwp.exe file could be related to a South-Korean Word Processor Software :
“Hangul Word Processor or HWP”. According to Wikipedia :
“Hangul Word Processor or HWP”. According to Wikipedia :
“It is used extensively in South Korea, especially by the government.“
According to Hangul’s website, this word processor handle Microsoft .DOC & .DOCX documents.
So the questions are
- Is the infected doc with zero-day also ‘compatible’ with it ?
- Was it used on targets in Korea or targets who use this processor?
- Was it made in Korea?
Your comments and thoughts are welcome.
thanks,
Mila
P.S. Korea came up before in this http://bugix-security.
P.S. Korea came up before in this http://bugix-security.