Original
E42F8E662D39A31B596D86504B9DC287 RandInfo.pdf 104165 bytes
Embedded / Dropped Files
590a6e6c811e41505bebd4a976b9e7f3 msapt.exe 41472 bytes
590a6e6c811e41505bebd4a976b9e7f3 update.exe 41472 bytes 230040293ED381E32FAA081B76634FCB wshipa.dll 32768 bytes 74180904D2F9DF2553C478F7AC480527 tpdefense.dat 103 bytes E73C3121EE1ED30643E1D1982393F978 RANDInfo.pdf 37822 bytes
From: RAND Corporation [mailto:randinfodesk@gmail.com]
Sent: Monday, September 21, 2009 8:04 AM
Subject: 2009 Defense Seminar Invitation
RAND Defense Security Seminar
October 19-23, 2009
1200 South Hayes Street
Arlington, VA 22202-5050
RAND Coporation will hold 2009 Defense Seminar at RAND’s Washington office at Pentagon City, Arlington, VA. Sessions will be held from 9:00 to 5:00 with an hour lunch break on Monday through Thursday, October 19–22, and from 9:00 to 1:00 on Friday, October 23, 2009.
Topics covered will include the following:
- The evolution of alliance and coalition partnerships
- The major issues and challenges in East Asia
- Gaming techniques for strategists and planners
- Missile defense technology and policy
- Transforming intelligence agencies to be better prepared to deal with today's threats
For more information, you can see attached file.
______________________________
Contact:
RAND Corporation
1200 South Hayes Street
1200 South Hayes Street
Arlington, VA 22202
Phone: 703/412-1100 x5409
Fax: 703/413-8181
Attached file
File RANDInfo.pdf received on 2010.02.01 21:24:53 (UTC)
http://www.virustotal.com/analisis/8978a152ebf292dea755309fd179e0d68df4c7fbcca796cc51dbf63a7da3e430-1265059493
Result: 19/41 (46.34%)
Antiy-AVL 2.0.3.7 2010.02.01 Exploit/Win32.Pidief
Authentium 5.2.0.5 2010.01.31 PDF/Pidief.AB
Avast 4.8.1351.0 2010.02.01 JS:Pdfka-gen
AVG 9.0.0.730 2010.02.01 Script/Exploit
BitDefender 7.2 2010.02.01 Exploit.PDF-JS.Gen
eTrust-Vet 35.2.7274 2010.02.01 PDF/Pidief.LH
F-Secure 9.0.15370.0 2010.02.01 Trojan.Script.213454
GData 19 2010.02.01 Trojan.Script.213454
Kaspersky 7.0.0.125 2010.02.01 Exploit.Win32.Pidief.cln
McAfee 5879 2010.02.01 Exploit-PDF.w
McAfee+Artemis 5879 2010.02.01 Exploit-PDF.w
McAfee-GW-Edition 6.8.5 2010.02.01 Heuristic.BehavesLike.PDF.Suspicious.Z
Microsoft 1.5406 2010.02.01 Exploit:Win32/Pdfjsc.CA
NOD32 4824 2010.02.01 JS/Exploit.Pdfka.NNB
PCTools 7.0.3.5 2010.02.01 Trojan.Pidief
Rising 22.33.00.04 2010.02.01 Hack.Exploit.Win32.PDF.jxr
Sunbelt 3.2.1858.2 2010.01.31 Exploit.PDF.Pidief.am (v)
Symantec 20091.2.0.41 2010.02.01 Trojan.Pidief.G
File size: 104165 bytes
MD5 : e42f8e662d39a31b596d86504b9dc287
Result: 19/41 (46.34%)
Antiy-AVL 2.0.3.7 2010.02.01 Exploit/Win32.Pidief
Authentium 5.2.0.5 2010.01.31 PDF/Pidief.AB
Avast 4.8.1351.0 2010.02.01 JS:Pdfka-gen
AVG 9.0.0.730 2010.02.01 Script/Exploit
BitDefender 7.2 2010.02.01 Exploit.PDF-JS.Gen
eTrust-Vet 35.2.7274 2010.02.01 PDF/Pidief.LH
F-Secure 9.0.15370.0 2010.02.01 Trojan.Script.213454
GData 19 2010.02.01 Trojan.Script.213454
Kaspersky 7.0.0.125 2010.02.01 Exploit.Win32.Pidief.cln
McAfee 5879 2010.02.01 Exploit-PDF.w
McAfee+Artemis 5879 2010.02.01 Exploit-PDF.w
McAfee-GW-Edition 6.8.5 2010.02.01 Heuristic.BehavesLike.PDF.Suspicious.Z
Microsoft 1.5406 2010.02.01 Exploit:Win32/Pdfjsc.CA
NOD32 4824 2010.02.01 JS/Exploit.Pdfka.NNB
PCTools 7.0.3.5 2010.02.01 Trojan.Pidief
Rising 22.33.00.04 2010.02.01 Hack.Exploit.Win32.PDF.jxr
Sunbelt 3.2.1858.2 2010.01.31 Exploit.PDF.Pidief.am (v)
Symantec 20091.2.0.41 2010.02.01 Trojan.Pidief.G
File size: 104165 bytes
MD5 : e42f8e662d39a31b596d86504b9dc287
Vicheck.ca
Detected entities:
PDF Exploit suspicious use of Colors tag CVE-2009-3957
Javascript obfuscation using unescape
Key Length: 256 bytes
Key Location: @52222 bytes
File XOR Offset: @254 bytes
XOR Key Length: 256 bytes
XOR Key:
0x[9f9e9d9c9b9a999897969594939291908f8e8d8c8b8a898887868584838281807f7e7d7c7b7a797877767574737271706f6e6d6c6b6a696867666564636261605f5e5d5c5b5a595857565554535251504f4e4d4c4b4a494847464544434241403f3e3d3c3b3a393837363534333231302f2e2d2c2b2a292827262524232221201f1e1d1c1b1a191817161514131211100f0e0d0c0b0a09080706050403020100fffefdfcfbfaf9f8f7f6f5f4f3f2f1f0efeeedecebeae9e8e7e6e5e4e3e2e1e0dfdedddcdbdad9d8d7d6d5d4d3d2d1d0cfcecdcccbcac9c8c7c6c5c4c3c2c1c0bfbebdbcbbbab9b8b7b6b5b4b3b2b1b0afaeadacabaaa9a8a7a6a5a4a3a2a1a0]
PDF Exploit suspicious use of Colors tag CVE-2009-3957
Javascript obfuscation using unescape
Key Length: 256 bytes
Key Location: @52222 bytes
File XOR Offset: @254 bytes
XOR Key Length: 256 bytes
XOR Key:
0x[9f9e9d9c9b9a999897969594939291908f8e8d8c8b8a898887868584838281807f7e7d7c7b7a797877767574737271706f6e6d6c6b6a696867666564636261605f5e5d5c5b5a595857565554535251504f4e4d4c4b4a494847464544434241403f3e3d3c3b3a393837363534333231302f2e2d2c2b2a292827262524232221201f1e1d1c1b1a191817161514131211100f0e0d0c0b0a09080706050403020100fffefdfcfbfaf9f8f7f6f5f4f3f2f1f0efeeedecebeae9e8e7e6e5e4e3e2e1e0dfdedddcdbdad9d8d7d6d5d4d3d2d1d0cfcecdcccbcac9c8c7c6c5c4c3c2c1c0bfbebdbcbbbab9b8b7b6b5b4b3b2b1b0afaeadacabaaa9a8a7a6a5a4a3a2a1a0]
Files dropped in the user %TEMP% directory
590a6e6c811e41505bebd4a976b9e7f3 msapt.exe 41472 bytes
590a6e6c811e41505bebd4a976b9e7f3 update.exe 41472 bytes
230040293ED381E32FAA081B76634FCB wshipa.dll 32768 bytes
74180904D2F9DF2553C478F7AC480527 tpdefense.dat 103 bytes
E73C3121EE1ED30643E1D1982393F978 RANDInfo.pdf 37822 bytes
590a6e6c811e41505bebd4a976b9e7f3 update.exe 41472 bytes
230040293ED381E32FAA081B76634FCB wshipa.dll 32768 bytes
74180904D2F9DF2553C478F7AC480527 tpdefense.dat 103 bytes
E73C3121EE1ED30643E1D1982393F978 RANDInfo.pdf 37822 bytes
Registry change to start msapt.exe every time Windows starts
HKU\S-1-5-21-839522115-725345543-2147116355-500\Software\Microsoft\Windows\CurrentVersion\Run\msapt: "C:\Documents and Settings\Administrator\Local Settings\Temp\msapt.exe -installkys"
Virustotal Trojan.Win32.Scar
HKU\S-1-5-21-839522115-725345543-2147116355-500\Software\Microsoft\Windows\CurrentVersion\Run\msapt: "C:\Documents and Settings\Administrator\Local Settings\Temp\msapt.exe -installkys"
Virustotal Trojan.Win32.Scar
590a6e6c811e41505bebd4a976b9e7f3 msapt.exe 41472 bytes
590a6e6c811e41505bebd4a976b9e7f3 update.exe 41472 bytes
590a6e6c811e41505bebd4a976b9e7f3 update.exe 41472 bytes
other known names for that MD5 hash is serverw.exe
File update.exe received on 2010.03.06 18:54:16 (UTC)
Result: 31/40 (77.50%)
a-squared 4.5.0.50 2010.03.06 Trojan.Win32.Scar!IK
AntiVir 8.2.1.180 2010.03.05 TR/Dropper.Gen
Authentium 5.2.0.5 2010.03.06 W32/Sisron.A!Generic
Avast 4.8.1351.0 2010.03.06 Win32:Malware-gen
Avast5 5.0.332.0 2010.03.06 Win32:Malware-gen
AVG 9.0.0.787 2010.03.06 Generic14.NGD
BitDefender 7.2 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
CAT-QuickHeal 10.00 2010.03.06 Trojan.Scar.yia
ClamAV 0.96.0.0-git 2010.03.06 Trojan.Agent-126367
Comodo 4091 2010.02.28 TrojWare.Win32.Scar.yia
DrWeb 5.0.1.12222 2010.03.06 BACKDOOR.Trojan
F-Prot 4.5.1.85 2010.03.06 W32/Sisron.A!Generic
F-Secure 9.0.15370.0 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
Fortinet 4.0.14.0 2010.03.06 W32/Dropper.P!tr
GData 19 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
Ikarus T3.1.1.80.0 2010.03.06 Trojan.Win32.Scar
Jiangmin 13.0.900 2010.03.06 Trojan/Scar.bbv
K7AntiVirus 7.10.990 2010.03.04 Trojan.Win32.Malware.1
Kaspersky 7.0.0.125 2010.03.06 Trojan.Win32.Scar.yia
McAfee 5912 2010.03.06 Generic.dx!fmd
McAfee+Artemis 5912 2010.03.06 Generic.dx!fmd
Microsoft 1.5502 2010.03.06 Trojan:Win32/Orsam!rts
NOD32 4921 2010.03.06 probably unknown NewHeur_PE
nProtect 2009.1.8.0 2010.03.06 Trojan/W32.Scar.41472.B
Panda 10.0.2.2 2010.03.06 Generic Trojan
PCTools 7.0.3.5 2010.03.04 Trojan.Generic
Sophos 4.51.0 2010.03.06 Mal/Dropper-P
Sunbelt 5771 2010.03.06 BehavesLike.Win32.Malware (v)
Symantec 20091.2.0.41 2010.03.06 Trojan Horse
TheHacker 6.5.1.9.222 2010.03.06 Trojan/Scar.yia
VBA32 3.12.12.2 2010.03.05 Trojan.Win32.Inject.2
Additional information
File size: 41472 bytes
MD5 : 590a6e6c811e41505bebd4a976b9e7f3
Threatexpert report on 590a6e6c811e41505bebd4a976b9e7f3
Result: 31/40 (77.50%)
a-squared 4.5.0.50 2010.03.06 Trojan.Win32.Scar!IK
AntiVir 8.2.1.180 2010.03.05 TR/Dropper.Gen
Authentium 5.2.0.5 2010.03.06 W32/Sisron.A!Generic
Avast 4.8.1351.0 2010.03.06 Win32:Malware-gen
Avast5 5.0.332.0 2010.03.06 Win32:Malware-gen
AVG 9.0.0.787 2010.03.06 Generic14.NGD
BitDefender 7.2 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
CAT-QuickHeal 10.00 2010.03.06 Trojan.Scar.yia
ClamAV 0.96.0.0-git 2010.03.06 Trojan.Agent-126367
Comodo 4091 2010.02.28 TrojWare.Win32.Scar.yia
DrWeb 5.0.1.12222 2010.03.06 BACKDOOR.Trojan
F-Prot 4.5.1.85 2010.03.06 W32/Sisron.A!Generic
F-Secure 9.0.15370.0 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
Fortinet 4.0.14.0 2010.03.06 W32/Dropper.P!tr
GData 19 2010.03.06 Gen:Trojan.Heur.PT.cqW@a0Tsc7nb
Ikarus T3.1.1.80.0 2010.03.06 Trojan.Win32.Scar
Jiangmin 13.0.900 2010.03.06 Trojan/Scar.bbv
K7AntiVirus 7.10.990 2010.03.04 Trojan.Win32.Malware.1
Kaspersky 7.0.0.125 2010.03.06 Trojan.Win32.Scar.yia
McAfee 5912 2010.03.06 Generic.dx!fmd
McAfee+Artemis 5912 2010.03.06 Generic.dx!fmd
Microsoft 1.5502 2010.03.06 Trojan:Win32/Orsam!rts
NOD32 4921 2010.03.06 probably unknown NewHeur_PE
nProtect 2009.1.8.0 2010.03.06 Trojan/W32.Scar.41472.B
Panda 10.0.2.2 2010.03.06 Generic Trojan
PCTools 7.0.3.5 2010.03.04 Trojan.Generic
Sophos 4.51.0 2010.03.06 Mal/Dropper-P
Sunbelt 5771 2010.03.06 BehavesLike.Win32.Malware (v)
Symantec 20091.2.0.41 2010.03.06 Trojan Horse
TheHacker 6.5.1.9.222 2010.03.06 Trojan/Scar.yia
VBA32 3.12.12.2 2010.03.05 Trojan.Win32.Inject.2
Additional information
File size: 41472 bytes
MD5 : 590a6e6c811e41505bebd4a976b9e7f3
Threatexpert report on 590a6e6c811e41505bebd4a976b9e7f3
http://www.threatexpert.com/report.aspx?md5=590a6e6c811e41505bebd4a976b9e7f3
Analysis of the file resources indicate the following possible
country of origin:
| China |
Anubis report of 590a6e6c811e41505bebd4a976b9e7f3
C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wshipa.dll
Virustotal wshipa.dll
http://www.virustotal.com/analisis/5d6ebaee77424e035d1d34473818d00bf4760ad2cdd38195b0ce865c2897977c-1267901791
File wshipa.dll received on 2010.03.06 18:56:31 (UTC)
Result: 3/42 (7.14%)
Antivirus Version Last Update Result
Prevx 3.0 2010.03.06 Medium Risk Malware
Symantec 20091.2.0.41 2010.03.06 Suspicious.Insight
VBA32 3.12.12.2 2010.03.05 suspected of Win32.Trojan-Downloader
File size: 32768 bytes
MD5 : 230040293ed381e32faa081b76634fcb
Randinfo.pdf e73c3121ee1ed30643e1d1982393f978- as expected, this embedded PDF is clean
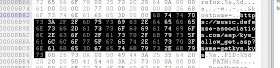
The trojan contains reference to
hxxps://music.defense-association.com/asp/kys_allow_get.asp?name=getkys.kys, which is not reachable at the time of this writing
Robtex information for music.defense-association.com
Sorry, we have no information about music.defense-association.com
defense-association.com
is a domain controlled by two nameservers having a total of four IP
numbers. All of them are on different IP networks. ctt.hk,
8jy.cn, ghcn.cn, 33cc.cn, jhcp.cn and at least
56 other hosts share nameservers with this domain. Reputation is not yet known.It is not listed in any blacklists.
Domain Name: DEFENSE-ASSOCIATION.COM
Registrar: BIZCN.COM, INC.
Whois Server: whois.bizcn.com
Referral URL: http://www.bizcn.com
Name Server: NS1.ORAY.NET
Name Server: NS2.ORAY.NET
Status: clientDeleteProhibited
Status: clientTransferProhibited
Updated Date: 25-oct-2009
Creation Date: 21-dec-2007
Expiration Date: 21-dec-2010
Registrar: BIZCN.COM, INC.
Whois Server: whois.bizcn.com
Referral URL: http://www.bizcn.com
Name Server: NS1.ORAY.NET
Name Server: NS2.ORAY.NET
Status: clientDeleteProhibited
Status: clientTransferProhibited
Updated Date: 25-oct-2009
Creation Date: 21-dec-2007
Expiration Date: 21-dec-2010
Registrant Contact:
jieqing
iang li lavinmondo@yahoo.com
0371-52140322 fax: 0371-25104796
jinshui,zhengzhou,henan
washingtondc washingtondc 450000
us
Administrative Contact:
qi zhang lavinmondo@yahoo.com
0371-45210368 fax: 0371-45210398
jinshui,zhengzhou,henan
washingtondc washingtondc 450000
us
Technical Contact:
iang li lavinmondo@yahoo.com
0371-52140322 fax: 0371-25104796
jinshui,zhengzhou,henan
washingtondc washingtondc 450000
us
Billing Contact:
iang li lavinmondo@yahoo.com
0371-52140322 fax: 0371-25104796
jinshui,zhengzhou,henan
washingtondc washingtondc 450000
us
DNS:
ns1.oray.net
ns2.oray.net







Check this blog, there are some exploit files information
ReplyDeletehttp://rootkit.tw/blog/?p=49