Update May 13 - added Rasauto32.dll
rasauto16.dll
Download
rasauto16.dll 15138604260b1d27f92bf1ec6468b326 +
rasauto16.dll 80ca8b948409138be40ffbc5d6d95ef1
Also, rasauto32.dll 995b44ef8460836d9091a8b361fde489
ac as a password protected archives (please contact me for the password if you need it)
Variant 1
File rasauto16.dll received on 2010.05.10 17:00:18 (UTC)
http://www.virustotal.com/analisis/bb1116f23874a36b0de47af8441c55687ccdcb0bad11384ab3718053f8eb7574-1273510818
Current status: finished
Result: 3/41 (7.32%)
Result: 3/41 (7.32%)
DrWeb 5.0.2.03300 2010.05.10 BACKDOOR.Trojan - yes, it is a backdoor and was used as such
McAfee-GW-Edition 2010.1 2010.05.10 Heuristic.BehavesLike.Win32.Backdoor.H
PCTools 7.0.3.5 2010.05.10 Trojan.Conficker.c.gen --I don't think so.
Additional information
File size: 107008 bytes
MD5 : 15138604260b1d27f92bf1ec6468b326
SHA1 : 7cd0faddaf926573be91f725b07865c14dd44254
SHA256: bb1116f23874a36b0de47af8441c55687ccdcb0bad11384ab3718053f8eb7574
PEInfo: PE Structure information
entrypointaddress.: 0x12B83
timedatestamp.....: 0x4B566B52 (Wed Jan 20 03:32:50 2010)
file dated just like other files on the system
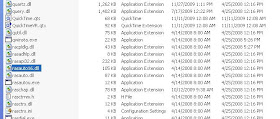 rasauto16.dll replaces legitimate rasauto.dll
rasauto16.dll replaces legitimate rasauto.dllRasauto
Service description:
Remote Access Auto Connection Manager
Creates a connection to a remote network whenever a program references a remote DNS or NetBIOS name or address.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasAuto\Parameters
ServiceDll %SystemRoot%\System32\rasauto16.dll
TCP traffic
202.175.83.10:443
z83l10.static.ctm.net
ISP:CTM Internet Services
Organization:CTM Internet Services
Country:Macau
City:Macau
address: Rua da Lagos, Telecentro
address: P.O. Box 868, Taipa
address: Macau
country: MO
Variant 2
http://www.virustotal.com/analisis/0de9fe6378a4c024f6f2c81b300897b8978d036caafbae9902850870d8f4dc04-1273511085
File rasauto16.dll received on 2010.05.10 17:04:45 (UTC)
Result: 4/41 (9.76%)
AntiVir 8.2.1.236 2010.05.10 TR/Spy.Gen
Comodo 4816 2010.05.10 ApplicUnwnt.Win32.AdWare.EZula.~GGC
McAfee-GW-Edition 2010.1 2010.05.10 Heuristic.BehavesLike.Win32.Backdoor.H
Sophos 4.53.0 2010.05.10 Mal/Emogen-Y
Additional information
File size: 669696 bytes
MD5...: 80ca8b948409138be40ffbc5d6d95ef1
SHA1..: f54b24660ec8664280e999e44148457e15f5489a
SHA256: 0de9fe6378a4c024f6f2c81b300897b8978d036caafbae9902850870d8f4dc04
ssdeep: 12288:CqjmOwFjklKkoTDLa77d46+HkQIwAy0WTuzjOFE:XjNwVxkofLFTjIyXTu
3O
entrypointaddress.: 0x22b03
timedatestamp.....: 0x4b679e56 (Tue Feb 02 03:39:02 2010)
machinetype.......: 0x14c (I386)
Creation and modified dates - 8/4/2004 8:00 am
rasauto16.dll replaces legitimate rasauto.dll
Rasauto
Service description:
Remote
Access Auto Connection Manager
Creates a connection to a remote network whenever a program
references a remote DNS or NetBIOSHKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasAuto\Parameters
ServiceDll %SystemRoot%\System32\rasauto16.dll
Variant 3
Rasauto32.dll
File rasauto32.dll received on 2010.05.13 16:19:29 (UTC)
http://www.virustotal.com/analisis/4da40b63c4027db5fb02e37db78da7333144809d1ddf0c86442e12d28cd7c47c-1273767569
Result: 12/41 (29.27%)
AntiVir 8.2.1.242 2010.05.13 TR/Spy.Gen
Antiy-AVL 2.0.3.7 2010.05.13 Trojan/Win32.Agent.gen
Avast 4.8.1351.0 2010.05.13 Win32:Malware-gen
Avast5 5.0.332.0 2010.05.13 Win32:Malware-gen
AVG 9.0.0.787 2010.05.13 Agent2.AMWN
GData 21 2010.05.13 Win32:Malware-gen
Jiangmin 13.0.900 2010.05.13 Trojan/Agent.drkq
Kaspersky 7.0.0.125 2010.05.13 Trojan.Win32.Agent.dnwh
Panda 10.0.2.7 2010.05.12 Suspicious file
Sophos 4.53.0 2010.05.13 Troj/RasSpy-Gen
TheHacker 6.5.2.0.280 2010.05.13 Trojan/Agent.dnwh
VBA32 3.12.12.4 2010.05.13 Trojan.Win32.Agent.dnwh
Additional information
File size: 647168 bytes
MD5...: 995b44ef8460836d9091a8b361fde489
TCP traffic
202.153.103.83:443
Hostname:beta.nethost.hkISP:TaiKoo Place, Quarry Bay
Organization: TaiKoo Place, Quarry Bay
Country:Hong Kong
City:Central District


No comments:
Post a Comment