General File Information
#1 File: card.exe
Size: 177152
MD5: A486EDD5D966FD167F9D8FA94087913E
SHA1 6cc60b1efb8d82b827634e7e42f2c3c981b1aff6
File Type: exe
Distribution: Link in email message - download in zip archive
from http://iphonedevelopersdk.com/wp-admin/includes/card.zip (still active as of Jan 2, 2011)
|
|
|
#2 File: card.exe
Size: 179712 bytes
MD5: D51F45E1985DC69CC6BC2B3AE1DA48F1
SHA1 b3b6e3cf9d9e268d2c5d3e692721ed0cdd9e323d
File Type: exe
Distribution: Link in email message - download in zip archive
from http://quimeras.com.mx/images/card.zip (not active) as seen at http://jsunpack.jeek.org/dec/go?report=908cfa23d23391577a6a5834bf6377d327c7053b
Read more
Post Updates
January 3, 2011 (11am) - Brian Krebs posted ‘White House’ eCard Dupes Dot-Gov Geeks" describing the sensitive documents from places like
-National Science Foundation’s Office of Cyber Infrastructure.
-Massachusetts State Police
-the Financial Action Task Force
-the Moroccan government’s Ministry of Industry, Commerce and New Technologies.
-Millennium Challenge Corporation
that were located on the repository server in Belarus (see description of the repository below). In addition, he interviews Alex Cox, principal research analyst with NetWitness who confirms a direct link to the Kneber botnet
" But it turns out that the more telling infrastructure point among the victims was this Perl2Exe component, which Cox says the company intentionally did not mention in its widely-quoted paper on the Kneber botnet." (- Brian Krebs)
January 3, 2011 (4:20pm) - Alex Cox from Netwitness posted Cyber-Crime or Cyber-Espionage? article, describing their analysis of this attack and the direct connection to the Kneber compromise they documented in February 2010. The attacks dated February 2010 used stat.exe, a perl2exe file very similar to pack.exe analyzed in this post. There are other similarities as well.
"It was poised to collect credentials from most major banks, but also includes site such as ebay, myspace, and microsoft, as well as online-payment processors, paypal and e-gold.
"When compared, these two files [stat.exe - Feb 2010 and pack.exe - Dec 2010 - Mila], separated by almost a year, are nearly identical in size. ..Furthermore when analyzed with HBGary’s “fingerprint” tool, which looks for code similarities and “toolmarks”, a 95.8% match is indicated, with the only differing factors being the CPUID of the machine on which the malware was compiled"
While these facts alone show similarities to infrastructure aspects of the “kneber” compromise that we documented back in February 2010, a very specific tie-in makes us believe that this attack was driven by operators that were also a part of the initial “kneber” compromise."
"This, because it is such a small and fairly unknown aspect of the kneber compromise, makes us think that this is indeed the same operator, who is again after documents pertaining to U.S. Government activities." (- Alex Cox)
Download
 Download the files listed below as a password protected archive (contact me if you need the password)
Download the files listed below as a password protected archive (contact me if you need the password)- ZeuS_config_a8a2e9dd2df1d85fa48956cf9c7fdd7f.bin
- pack.exe 00195DF48AD9FFD19CF87F5566DA4DB0
- card.exe A486EDD5D966FD167F9D8FA94087913E
- card.exe D51F45E1985DC69CC6BC2B3AE1DA48F1
Malware Information
This malware made rounds on December, 23, 2010 and was already mentioned in the ISC and TrendMicro blogs as another Zeus banking Trojan variant. Please see links for the posts below. However, there was no further analysis or more detailed description of this particular variant given, which appears to be designed for stealing documents as opposed to stealing passwords and banking information. This places this particular trojan in the category of malware designed for data theft and political/corporate espionage.
 |
|
|
- Old ZeuS Variant Returns for Christmas Trend Micro
- TSPY_ZBOT.XMAS - Trend Micro
- White house greeting cards - ISC Internet Storm Center
http://contagiodump.blogspot.com/2009/12/creative-nsa-spoof-attack-of-day.html
(Zeus in http://www.zeropaid.com/bbs/includes/CYBERCAFE.zip)
Aug 25 CVE-2010-1240 From Intelligence Fusion Centre with ZeuS trojan
(Zeus in http:// gnarus.mobi/media/EuropeanUnion_MilitaryOperations_EN. zip
http:// quimeras.com.mx/media/EuropeanUnion_MilitaryOperations_EN.zip)
In addtion, Nart Villeneuve published an excellent and very detail analysis of Zeus driven targeted attacks and espionage activities in his
The interest of this particular piece of malware lies not in the Zeus trojan itself but in the downloaded file, pack.exe, which is a perl script converted to exe by means of IndigoStar Perl2exe commercial application. Pack.exe is designed to search a computer drive for XLS, DOC, and PDF documents, gather them into a folder "c:\temp" and ftp them out to a repository in Belarus, together with such information as the pc user name and list of files on C:
As of Jan 2, 2011, pack.exe and the ftp file repository accepting victims' files are fully functional.
The Zeus bot component of this attack is not functioning today due to bot's dropzone being inactive, however future mailings can create new functioning bots that can be utilized over and over for more information, keylogging, and installing additional malware.
I would like to thank Andre M. DiMino of the Shadowserver Foundation and another researcher who wished to remain anonymous for offering the sample, advice and information about this type of malware.
Original Message
Message Headers
Received: from bondi.myownserver.net (bondi.myownserver.net [118.127.17.43])
(using TLSv1 with cipher DHE-RSA-AES256-SHA (256/256 bits))
(No client certificate requested)
by z.teksimple.com (Postfix) with ESMTP id 7B4E2578002
for XXXXXXXXXXX; Thu, 23 Dec 2010 20:06:41 +0000 (UTC)
Received: from taecnsw by bondi.myownserver.net with local (Exim 4.69)
(envelope-from
id 1PVrNa-00057R-Go
for XXXXXXXXXXXXXXXXX; Fri, 24 Dec 2010 07:03:14 +1100
Return-Path:
From:
To: "XXXXXXXXXXXXXXXXXXXXXXX"
Subject: Merry Christmas!
Date: Thu, 23 Dec 2010 10:03:14 -1000
Message-ID:
MIME-Version: 1.0
Content-Type: text/plain;
charset="iso-8859-1"
Content-Transfer-Encoding: 7bit
X-Mailer: Microsoft Outlook 14.0
thread-index: AQIGUvhtW6McP8BIIPWFeDGkYaOI5Q==
Sender IP/Domain
bondi.myownserver.net
Bondi.myownserver.net is a domain controlled by two name servers at myownserver.net. Both are on different IP networks. The primary name server is ns21.myownserver.net. Incoming mail for bondi.myownserver.net is handled by one mail server also at myownserver.net. bondi.myownserver.net has one IP number (118.127.17.43) , which also has a corresponding reverse pointer.
myownserver.net
Myownserver.net is a domain controlled by four name servers also at myownserver.net. Some of them are on the same IP network. The primary name server is ns1.myownserver.net. Incoming mail for myownserver.net is handled by two mail servers also at myownserver.net. Both are on different IP networks. myownserver.net has one IP number (67.228.216.64) , but the reverse is thebruce.myownserver.net.
More information
bondi.myownserver.net is hosted on a server in Australia.
It is blacklisted in one list. Search for myownserver.net.
Automated Scans and analysis
Card.exe from http://iphonedevelopersdk.com/wp-admin/includes/card.zip
http://www.virustotal.com/file-scan/report.html?id=080064ebbec07cb8a173b99ac8a0392595548aad6bdcc8f6a8ff1bb4d91c2252-1293674106
Submission date:2010-12-30 01:55:06 (UTC)
Current status:finished
Result:27 /43 (62.8%)
Antivirus Version Last Update Result
AhnLab-V3 2010.12.30.00 2010.12.29 Win-Trojan/Zbot.177152.AC
AntiVir 7.11.0.220 2010.12.29 TR/Kazy.3994.5
Avast 4.8.1351.0 2010.12.29 Win32:Malware-gen
Avast5 5.0.677.0 2010.12.29 Win32:Malware-gen
AVG 9.0.0.851 2010.12.30 PSW.Generic8.APJK
BitDefender 7.2 2010.12.30 Gen:Variant.Kazy.3994
Command 5.2.11.5 2010.12.30 -
Comodo 7233 2010.12.30 TrojWare.Win32.TrojanSpy.Zbot.Gen
DrWeb 5.0.2.03300 2010.12.30 Trojan.PWS.Panda.171
Emsisoft 5.1.0.1 2010.12.29 Gen.Variant.Kazy!IK
eTrust-Vet 36.1.8070 2010.12.29 Win32/Spyeye.KP
F-Secure 9.0.16160.0 2010.12.30 Gen:Variant.Kazy.3994
GData 21 2010.12.30 Gen:Variant.Kazy.3994
Ikarus T3.1.1.90.0 2010.12.30 Gen.Variant.Kazy
Kaspersky 7.0.0.125 2010.12.30 Trojan-Spy.Win32.Zbot.awgt
McAfee 5.400.0.1158 2010.12.30 Artemis!A486EDD5D966
McAfee-GW-Edition 2010.1C 2010.12.29 Artemis!A486EDD5D966
Microsoft 1.6402 2010.12.29 PWS:Win32/Zbot
NOD32 5744 2010.12.29 Win32/Spy.Zbot.UN
nProtect 2010-12-29.01 2010.12.29 Trojan/W32.Agent.177152.CQ
Panda 10.0.2.7 2010.12.29 Trj/CI.A
PCTools 7.0.3.5 2010.12.30 Trojan.Gen
Rising 22.80.02.01 2010.12.29 Packer.Win32.Agent.bk
Sophos 4.60.0 2010.12.30 Mal/FakeAV-GQ
Symantec 20101.3.0.103 2010.12.30 Trojan.Gen.2
TrendMicro 9.120.0.1004 2010.12.29 TSPY_ZBOT.ANX
TrendMicro-HouseCall 9.120.0.1004 2010.12.30 TSPY_ZBOT.ANX
VIPRE 7878 2010.12.29 Trojan.Win32.Generic!BT
Additional information
Show all
MD5 : a486edd5d966fd167f9d8fa94087913e
SHA1 : 6cc60b1efb8d82b827634e7e42f2c3c981b1aff6
Card.exe from http://quimeras.com.mx/images/card.zip
http://www.virustotal.com/file-scan/report.html?id=3bf762adc152fccfadf78ad131588df8a3e740eed20e1712b86ca7d9da5f676b-1293885939
File name:zbot-xmas.ex1
Submission date:2011-01-01 12:45:39 (UTC)
Current status:finished
Result:33 /43 (76.7%)
AhnLab-V3 2011.01.01.00 2010.12.31 Win-Trojan/Zbot.179712.P
AntiVir 7.11.0.247 2010.12.31 TR/Kazy.3994.2
Antiy-AVL 2.0.3.7 2011.01.01 Trojan/Win32.Genome.gen
Avast 4.8.1351.0 2011.01.01 Win32:Malware-gen
Avast5 5.0.677.0 2011.01.01 Win32:Malware-gen
AVG 9.0.0.851 2011.01.01 PSW.Generic8.APBG
BitDefender 7.2 2011.01.01 Gen:Variant.Kazy.3994
ClamAV 0.96.4.0 2011.01.01 Trojan.Spy.Zbot-116
Comodo 7259 2011.01.01 TrojWare.Win32.TrojanSpy.Zbot.Gen
DrWeb 5.0.2.03300 2011.01.01 Trojan.PWS.Panda.171
Emsisoft 5.1.0.1 2011.01.01 Gen.Variant.Kazy!IK
F-Secure 9.0.16160.0 2011.01.01 Gen:Variant.Kazy.3994
Fortinet 4.2.254.0 2011.01.01 W32/Zbot.AHT!tr
GData 21 2011.01.01 Gen:Variant.Kazy.3994
Ikarus T3.1.1.90.0 2011.01.01 Gen.Variant.Kazy
K7AntiVirus 9.75.3406 2010.12.31 Trojan
Kaspersky 7.0.0.125 2011.01.01 Trojan.Win32.Genome.nbpk
McAfee 5.400.0.1158 2011.01.01 PWS-Zbot.gen.ad
McAfee-GW-Edition 2010.1C 2011.01.01 PWS-Zbot.gen.ad
Microsoft 1.6402 2011.01.01 PWS:Win32/Zbot
nProtect 2011-01-01.01 2011.01.01 Trojan-Spy/W32.Kazy.179712
Panda 10.0.2.7 2010.12.31 Generic Trojan
PCTools 7.0.3.5 2011.01.01 Trojan.Zbot
Rising 22.80.04.04 2010.12.31 Packer.Win32.Agent.bk
Sophos 4.60.0 2011.01.01 Troj/Zbot-AHT
Symantec 20101.3.0.103 2011.01.01 Trojan.Zbot
TheHacker 6.7.0.1.109 2010.12.30 Trojan/Genome.nbpk
TrendMicro 9.120.0.1004 2011.01.01 TSPY_ZBOT.XMAS
TrendMicro-HouseCall 9.120.0.1004 2011.01.01 TSPY_ZBOT.XMAS
VBA32 3.12.14.2 2010.12.30 Trojan.Carder.xa
VIPRE 7908 2011.01.01 Trojan.Win32.Generic!BT
ViRobot 2010.12.31.4232 2011.01.01 Trojan.Win32.Zbot.179712.B
VirusBuster 13.6.121.0 2010.12.30 Trojan.Kazy!BYT8I1/eVOs
Additional information
Show all
MD5 : d51f45e1985dc69cc6bc2b3ae1da48f1
Pack.exe
File name:pack.exe-jeskzohttp://www.virustotal.com/file-scan/report.html?id=77b4c6dad160cff51bd5fa2eaaa8c2899a51057a75618a8f4ab877aca052d9df-1293714293
Submission date:2010-12-30 13:04:53 (UTC)
Current status:Result:16 /42 (38.1%)
AhnLab-V3 2010.12.30.02 2010.12.30 Win-Trojan/Agent.900769
AntiVir 7.11.0.224 2010.12.30 DR/Spy.Perl.Agent.C
DrWeb 5.0.2.03300 2010.12.30 Trojan.Uploader.24588
Emsisoft 5.1.0.1 2010.12.30 Trojan-Spy.Perl.Agent!IK
Fortinet 4.2.254.0 2010.12.30 Perl/Agent.C!tr
Ikarus T3.1.1.90.0 2010.12.30 Trojan-Spy.Perl.Agent
K7AntiVirus 9.75.3383 2010.12.29 Trojan
Kaspersky 7.0.0.125 2010.12.30 Trojan-Spy.Perl.Agent.c
McAfee 5.400.0.1158 2010.12.30 Generic PWS.y!cvp
McAfee-GW-Edition 2010.1C 2010.12.30 Generic PWS.y!cvp
nProtect 2010-12-30.01 2010.12.30 Trojan-Spy/W32.Agent.900769
Panda 10.0.2.7 2010.12.29 Trj/CI.A
PCTools 7.0.3.5 2010.12.30 Trojan-PSW.Generic
Prevx 3.0 2010.12.30 High Risk Cloaked Malware
Symantec 20101.3.0.103 2010.12.30 Infostealer
VIPRE 7881 2010.12.30 -
ViRobot 2010.12.30.4229 2010.12.30 Spyware.Agent.900769
VirusBuster 13.6.120.0 2010.12.30 -
Additional information
Show all
MD5 : 00195df48ad9ffd19cf87f5566da4db0
Threatexpert report for
Card,exe from http://iphonedevelopersdk.com/wp-admin/includes/card.zip http://www.threatexpert.com/report.aspx?md5=a486edd5d966fd167f9d8fa94087913e
The following files were created in the system:
1
[file and pathname of the sample #1]
%System%\sdra64.exe
177,152 bytes
MD5: 0xA486EDD5D966FD167F9D8FA94087913E
SHA-1: 0x6CC60B1EFB8D82B827634E7E42F2C3C981B1AFF6
2
%Windir%\Temp\1.tmp
900,769 bytes
MD5: 0x00195DF48AD9FFD19CF87F5566DA4DB0
SHA-1: 0x59528E3AC99C92C11721E9C1F8047B16FB0038BF
--------------------
The following hidden files were created in the system:
1 %System%\lowsec\local.ds
41,526 bytes
MD5: 0xE7C44CB61827BFC25354C33A94B3103C
SHA-1: 0xB181EAC3007AB754006C305C4D205D1A7C334F19
2 %System%\lowsec\user.ds
0 bytes
MD5: 0xD41D8CD98F00B204E9800998ECF8427E
SHA-1: 0xDA39A3EE5E6B4B0D3255BFEF95601890AFD80709
--------------------------------------------------
*There were registered attempts to establish connection with the remote hosts. The connection details are:
209.172.60.242 80 -- http://209.172.60.242/~newdowni/stat/gate_in.php -- Zeus Drop zone (inactive)
72.34.32.138 80 -- http://vivario.no/language/pack.exe (active)
81.27.32.130 80 -- http://ingunnanvik.no/templates/system/sysny.bin --- Zeus config file (inactive)
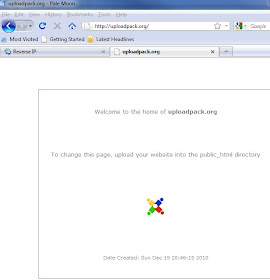
93.84.112.155 21 - uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM (active)
outbound traffic through ports to 93.84.112.155 server in Belarus, Minsk Republican Association BELTELECOM
93.84.112.155 61368 This is the name of the directory on the FTP server
93.84.112.155 62426 This is the user name being transferrd
93.84.112.155 62426 This is the list of files on C: being transferred
Update Jan 2, 2010 As a variant, these links in email might be used (update January 3, 2010) - with the same redirect
http://galaxy-displays.com/
http://www.leigh-n.com/card/

http://xtremedefenceforce.com/card/ (still active Jan 2, 2011)
http://elvis.com.au/card/ (still active Jan 2, 2011)

http://www.virustotal.com/file-scan/report.html?id=77b4c6dad160cff51bd5fa2eaaa8c2899a51057a75618a8f4ab877aca052d9df-1293714293
Pack.exe gathers XLS, DOC, and PDF documents and uploads them via FTP to
93.84.112.155 21 - uploadpack.org
For some reason, the file does not gather XLSX, PPTX, and DOCX files for new Office 2007 and 2010 and the credentials for the ftp are being transferred in clear text.
FTP login to the 93.84.112.155 confirms that the server is functioning and receives files from the victims. The random name directories contain the documents gathered.
The web/ftp server on uploadpack.org 93.84.112.155 was created quite recently - on December 19, 2011
pack.exe can be decompiled - here is how:
Perl2Exe EXEs Can Be Decompiled
http://www.perlmonks.org/?
209.172.60.242 80 -- http://209.172.60.242/~newdowni/stat/gate_in.php -- Zeus Drop zone (inactive)
72.34.32.138 80 -- http://vivario.no/language/pack.exe (active)
81.27.32.130 80 -- http://ingunnanvik.no/templates/system/sysny.bin --- Zeus config file (inactive)
93.84.112.155 21 - uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM (active)
93.84.112.155 61368 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM
93.84.112.155 62426 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM
93.84.112.155 63339 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM
<><>
Data theft via FTP process
http://elvis.com.au/card/ (still active Jan 2, 2011)

Files Created
Pack.exehttp://www.virustotal.com/file-scan/report.html?id=77b4c6dad160cff51bd5fa2eaaa8c2899a51057a75618a8f4ab877aca052d9df-1293714293
Pack.exe gathers XLS, DOC, and PDF documents and uploads them via FTP to
93.84.112.155 21 - uploadpack.org
For some reason, the file does not gather XLSX, PPTX, and DOCX files for new Office 2007 and 2010 and the credentials for the ftp are being transferred in clear text.
FTP login to the 93.84.112.155 confirms that the server is functioning and receives files from the victims. The random name directories contain the documents gathered.
_users.dll - user name
All Users
Default User
LocalService
mila
NetworkService
_hslib.dll - directory name
s96X1tuXPilBSkdt
_C.dll - C drive list of files
AUTOEXEC.BAT
boot.ini
CONFIG.SYS
Documents and Settings
IO.SYS
MSDOS.SYS
MSOCache
NTDETECT.COM
ntldr
pack.exe
pagefile.sys
Program Files
reader and Flash.txt
RECYCLER
regshot
System Volume Information
temp
WINDOWS
wp_marble_009.jpg
|
|
|
uploadpack.org
Domain ID:D160999701-LROR
Domain Name:UPLOADPACK.ORG
Created On:20-Dec-2010 12:49:25 UTC
Last Updated On:20-Dec-2010 12:49:26 UTC
Expiration Date:20-Dec-2011 12:49:25 UTC
Sponsoring Registrar:Directi Internet Solutions Pvt. Ltd. d/b/a PublicDomainRegistry.com (R27-LROR)
Status:CLIENT TRANSFER PROHIBITED
Status:TRANSFER PROHIBITED
Registrant ID:DI_13466487
Registrant Name:Pavel Zeminov
Registrant Organization:None
Registrant Street1:Mira 24-28
Registrant Street2:
Registrant Street3:
Registrant City:Vinnica
Registrant State/Province:VinnicaNa
Registrant Postal Code:21000
Registrant Country:UA
Registrant Phone:+380.380682454687
93.84.112.155inetnum: 93.84.112.0 - 93.84.119.255
netname: BELTELECOM-DATACENTER
descr: MCC & REGIONAL DCs
country: BY
admin-c: DK2210-RIPE
tech-c: IS2093-RIPE
status: ASSIGNED PA
mnt-by: AS6697-MNT
remarks: INFRA-AW
source: RIPE # Filtered
person: Dmitry Komarov
address: 220088, Minsk
address: 55, Zaharova str.,
address: RUE Beltelecom
phone: +375 17 2171799
fax-no: +375 17 2100259
e-mail:
nic-hdl: DK2210-RIPE
mnt-by: AS6697-MNT
source: RIPE # Filtered
person: Ivan Semernik
address: 220088, Minsk
address: 55, Zaharova str.,
address: RUE Beltelecom
phone: +375 17 2171799
fax-no: +375 17 2100259
e-mail:
nic-hdl: IS2093-RIPE
mnt-by: AS6697-MNT
source: RIPE # Filtered
route: 93.84.0.0/15
descr: DELEGATED FROM BELPAK
origin: AS6697
mnt-by: AS6697-MNT
source: RIPE # Filtered
pack.exe can be decompiled - here is how:
Perl2Exe EXEs Can Be Decompiled
http://www.perlmonks.org/?
Network activity
here were registered attempts to establish connection with the remote hosts. The connection details are:209.172.60.242 80 -- http://209.172.60.242/~newdowni/stat/gate_in.php -- Zeus Drop zone (inactive)
72.34.32.138 80 -- http://vivario.no/language/pack.exe (active)
81.27.32.130 80 -- http://ingunnanvik.no/templates/system/sysny.bin --- Zeus config file (inactive)
93.84.112.155 21 - uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM (active)
93.84.112.155 61368 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM
93.84.112.155 62426 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM
93.84.112.155 63339 uploadpack.org - server in Belarus, Minsk Republican Association BELTELECOM











Nice work, Mila. Anyone been able to decompile pack.exe, yet?
ReplyDeleteNice work)
ReplyDeleteAUTOEXEC.BAT
boot.ini
Config.Msi
CONFIG.SYS
Documents and Settings
Flash Version.txt
IO.SYS
MSDOS.SYS
MSOCache
NTDETECT.COM
ntldr
pagefile.sys
Program Files
Reader.txt
RECYCLER
regshot
System Volume Information
temp
WINDOWS
wp_weave_038.gif