Common Vulnerabilities and Exposures (CVE)number
CVE-2011-0611 -- Adobe Flash Player 10.2.153.1 and earlier for Windows, Macintosh, Linux, and Solaris; 10.2.154.25 and earlier for Chrome; and 10.2.156.12 and earlier for Android; Adobe AIR 2.6.19120 and earlier; and Authplay.dll (aka AuthPlayLib.bundle) in Adobe Reader and Acrobat 9.x through 9.4.3 and 10.x through 10.0.2 on Windows and Mac OS X, allows remote attackers to execute arbitrary code or cause a denial of service (application crash) via crafted Flash content, related to a size inconsistency in a "group of included constants," object type confusion, and Date objects, as demonstrated by a .swf file embedded in a Microsoft Word document, and as exploited in the wild in April 2011.
General File Information
File Marshall Plan for the North Africa.pdf
MD5: 6d5fb801b890bfa7cc737c018e87e456
SHA1: 441cfe9d31d271262ff693e83daa1b4fefa0e2c4
SHA256: afe8d2abf6807bb1b83affc20b8fcb424d75cb7ce340c900b59daeb9b3edc628
File size: 464485 bytes
Type: PDF
Distribution: Email attachment
Read more...
Download
Post Updates
May 4, 2011 Please see an excellent analysis for this file here How to Extract Flash Objects from Malicious PDF Files by Lenny Zeltser
The message was sent by the same actors and has the same payload as in this post http://contagiodump.blogspot.com/2011/04/apr-20-cve-2011-0611-pdf-swf-chinas.html
Here is an excellent analysis of the payload by Hermes Bojaxhi from CyberESI http://www.cyberesi.com/2011/04/25/chinas-charm-diplomacy-in-brics-summit-pdf-cve-2011-0611/
Original Message
From: Christy Serrato [mailto:serrato.christy@gmail.com]Sent: Friday, April 22, 2011 10:32 AM
To: XXXXXXXX
Subject: Marshall Plan for the North Africa
I reach out to you for advice about an initiative we are considering launching for North Africa.The Nicole Berggruen Institute is an action oriented think tank that seeks implement effective systems of governance through projects at various levels across the globe. One such project is the development of a Marshall Plan for the North Africa.
How I am hoping you can help is to provide insight and advice on what is currently happening within the region.
Thank you in advance for anytime you can give me. I look forward to your reply soon.
Serrato Christy
Senior Program Manager
Middle East and North Africa
NICOLAS BERGGRUEN INSTITUTE
Message Headers
Gmail :(
Received: by wwb39 with SMTP id 39so636530wwb.6 for ;
Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=gamma;
h=domainkey-signature:mime-version:date:message-id:subject:from:to
:content-type;
bh=4CUY8j8jGJeAnrD/Qo6HSZGR94sdW5P0d67wOrEK55A=;
b=YADFFJft8LGJmZQoFG+R7nLFlREhueyUJDUULLTy5rbU5ahHOmH/B3VDiHLKxJRDWa
MFT0VjRiQenP/RjOBKG6uxZPRAkwztUUKD1mPmN7RMOO1lmOuQS2CTtFwGvtxuSPZsG1
LE0nZf4nZi3CkI7LUx9Ficawc/KRajrJ1StdQ=
DomainKey-Signature: a=rsa-sha1; c=nofws;
d=gmail.com; s=gamma;
h=mime-version:date:message-id:subject:from:to:content-type;
b=Om90qyH/txeauhB/b9dr5k/r+FrEABSYzih46JA2QyeA9RDErNdPZnbJpeA4jWMgg0
/JongciwiC7zE+TVEZDQorGv9qNswKt2dVO7lBgYBkC5ohabgwHqBlK/uBGuSBikkMF0
8ikYcIMZ33QM7846FCG1HH4k07OWOKz8MGqRo=
MIME-Version: 1.0
Received: by 10.227.165.194 with SMTP id j2mr1203487wby.178.1303482722563;
Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
Received: by 10.227.157.66 with HTTP; Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
Date: Fri, 22 Apr 2011 22:32:02 +0800
Message-ID: BANLkTikPU6AS48Gyr9BhwKQvN1jmkZ70Sw@mail.gmail.com
Subject: Marshall Plan for the North Africa
From: Christy Serrato
To: XXXXXXXXXXX
Content-Type: multipart/mixed; boundary="90e6ba4768d9a63a6a04a182b841"
Return-Path: serrato.christy@gmail.com
Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=gmail.com; s=gamma;
h=domainkey-signature:mime-version:date:message-id:subject:from:to
:content-type;
bh=4CUY8j8jGJeAnrD/Qo6HSZGR94sdW5P0d67wOrEK55A=;
b=YADFFJft8LGJmZQoFG+R7nLFlREhueyUJDUULLTy5rbU5ahHOmH/B3VDiHLKxJRDWa
MFT0VjRiQenP/RjOBKG6uxZPRAkwztUUKD1mPmN7RMOO1lmOuQS2CTtFwGvtxuSPZsG1
LE0nZf4nZi3CkI7LUx9Ficawc/KRajrJ1StdQ=
DomainKey-Signature: a=rsa-sha1; c=nofws;
d=gmail.com; s=gamma;
h=mime-version:date:message-id:subject:from:to:content-type;
b=Om90qyH/txeauhB/b9dr5k/r+FrEABSYzih46JA2QyeA9RDErNdPZnbJpeA4jWMgg0
/JongciwiC7zE+TVEZDQorGv9qNswKt2dVO7lBgYBkC5ohabgwHqBlK/uBGuSBikkMF0
8ikYcIMZ33QM7846FCG1HH4k07OWOKz8MGqRo=
MIME-Version: 1.0
Received: by 10.227.165.194 with SMTP id j2mr1203487wby.178.1303482722563;
Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
Received: by 10.227.157.66 with HTTP; Fri, 22 Apr 2011 07:32:02 -0700 (PDT)
Date: Fri, 22 Apr 2011 22:32:02 +0800
Message-ID: BANLkTikPU6AS48Gyr9BhwKQvN1jmkZ70Sw@mail.gmail.com
Subject: Marshall Plan for the North Africa
From: Christy Serrato
To: XXXXXXXXXXX
Content-Type: multipart/mixed; boundary="90e6ba4768d9a63a6a04a182b841"
Return-Path: serrato.christy@gmail.com
Automated Scans
Marshall Plan for the North Africa.pdf
| Antivirus | Version | Last update | Result |
|---|---|---|---|
| Avast5 | 5.0.677.0 | 2011.04.25 | SWF:Agent-K |
| Commtouch | 5.3.2.6 | 2011.04.25 | JS/Pdfka.V |
| DrWeb | 5.0.2.03300 | 2011.04.25 | Exploit.PDF.2177 |
| eTrust-Vet | 36.1.8289 | 2011.04.25 | PDF/CVE-2010-1297.B!exploit |
| Microsoft | 1.6802 | 2011.04.25 | Exploit:SWF/CVE-2011-0611.I |
| TrendMicro | 9.200.0.1012 | 2011.04.25 | TROJ_PIDIEF.SMDX |
| TrendMicro-HouseCall | 9.200.0.1012 | 2011.04.25 | TROJ_PIDIEF.SMDX |
| MD5: 6d5fb801b890bfa7cc737c018e87e456 |
| SHA1: 441cfe9d31d271262ff693e83daa1b4fefa0e2c4 |
| SHA256: afe8d2abf6807bb1b83affc20b8fcb424d75cb7ce340c900b59daeb9b3edc628 |
| File size: 464485 bytes |
| Scan date: 2011-04-25 15:29:18 (UTC) |
Analysis Details
-Flash embedded in the fileExtracted flash
| Antivirus | Version | Last update | Result |
|---|---|---|---|
| Avast | 4.8.1351.0 | 2011.04.25 | SWF:Agent-K |
| Avast5 | 5.0.677.0 | 2011.04.25 | SWF:Agent-K |
| GData | 22 | 2011.04.25 | SWF:Agent-K |
| Symantec | 20101.3.2.89 | 2011.04.25 | Trojan.Dropper |
| MD5: c56dd87772312ba032fc6ac8928d480f | |
| SHA1: 1fe3478d65ba9508b1fdc31d6b3e67b336b06b95 | |
| SHA256: fff09d52d2fedc1a85fa04f75fe9a8295a57ddc39d4888ce65662e7a7b9671c0 | |
| File size: 7461 bytes | |
| Scan date: 2011-04-25 17:32:54 (UTC) |
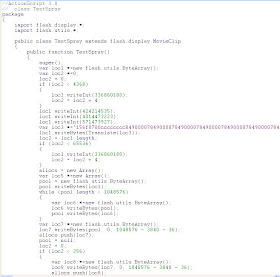
Action script
Files Created
%TEMP%Marshall Plan for the North Africa.pdf - clean dropped file
MD5: 93b600d4d641321dae860d179d8a35cf
AcroRd32.exe
The file runs as an exe and can be seen in the Windows Task Manager. It installs a link to itself in the Windows Startup folder %Programs%\Startup\Adobe Reader Speed Launcher.lnk
MD5: 39822adc9bc7747dadd212e0338948cb
http://www.virustotal.com/file-scan/report.html?id=b32482d120f24d88f06edb974e92b301e4bd9be99e5ee7f10e9e6dce1a557192-1303748025#
| Antivirus | Version | Last update | Result |
|---|---|---|---|
| NOD32 | 6069 | 2011.04.25 | a variant of Win32/Ixeshe.E |
| Panda | 10.0.3.5 | 2011.04.25 | Suspicious file |
| MD5: 39822adc9bc7747dadd212e0338948cb |
| SHA1: 00d9650584489914016941fbe28cd1c02306a34b |
| SHA256: b32482d120f24d88f06edb974e92b301e4bd9be99e5ee7f10e9e6dce1a557192 |
| File size: 430080 bytes |
| Scan date: 2011-04-25 16:13:45 (UTC) |
From ThreatExpert
| Filename(s) | File Size | File Hash | |
| 1 | %Programs%\Startup\Adobe Reader Speed Launcher.lnk | 1,464 bytes | MD5: 0x6A4CD2DA75F64AF7C402BE5BFBC516BD SHA-1: 0x6F02199A721848449AB4992307220D1F732DA24C |
| 2 | [file and pathname of the sample #1] | 430,080 bytes | MD5: 0x39822ADC9BC7747DADD212E0338948CB SHA-1: 0x00D9650584489914016941FBE28CD1C02306A34B |
Network activity
----
- There was registered attempt to establish connection with the remote host. The connection details are:
| Remote Host | Port Number |
| 68.16.99.165 | 443 |
- The following GET request was made:
- /AWS7446.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
- The data identified by the following URLs was then requested from the remote web server:
- http://68.16.99.165/AWS7394.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
- http://68.16.99.165/AWS7414.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
- http://68.16.99.165/AWS7437.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
- http://68.16.99.165/AWS7463.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
- http://68.16.99.165/AWS7473.jsp?2rlfgi5C/Sn0TRDqQj5c/Sn0TRDqQvDwTsnJgrl8UaZSxRVYPsUcGjF2GjZoPr/qgspwPrVFPaZN/SnrxRpqGjZFTrK7=MH32b5wPI27=hTL=aYdQ4vV=M9Bph7k=h29Qhvo0aLKQjpJPbYA
adsl-068-016-099-165.sip.asm.bellsouth.net
mail.the-joy-of-travel.com
the-joy-of-travel.com
www.the-joy-of-travel.com
| China |











No comments:
Post a Comment