Update April 20, 2012 - I added 8 more samples (now there are 12 posted), did not look at all of them yet but I think you may find them useful for developing signatures, etc
Researchers based in Asia noticed these malicious documents in Japan and Taiwan before they started showing up/targeting USA companies. Three documents donated a few days ago by someone from Asia were crafted to run only on the Taiwanese version of Windows. The document I found today was uploaded to an online analysis service and it is for English Windows, it was named "inside information.doc" and drops a decoy document called 英文 , which means English. I could not get "Taiwanese" binaries run on English OS but this one executed successfully.
The vulnerability is due to an error in ActiveX control, in this case embedded in an RTF document. All documents I looked at are very similar, most likely there is a generator involved in making these. I have not seen any documents that would run without crashing the Word, so you need to carve out at least the first stage binary manually.
Many thanks to Brandon Dixon and Binjo for technical advice and inspiration :)
CVE information
CVE-2012-0158 The (1) ListView, (2) ListView2, (3) TreeView, and (4) TreeView2 ActiveX controls in MSCOMCTL.OCX in the Common Controls in Microsoft Office 2003 SP3, 2007 SP2 and SP3, and 2010 Gold and SP1; Office 2003 Web Components SP3; SQL Server 2000 SP4, 2005 SP4, and 2008 SP2, SP3, and R2; BizTalk Server 2002 SP1; Commerce Server 2002 SP4, 2007 SP2, and 2009 Gold and R2; Visual FoxPro 8.0 SP1 and 9.0 SP2; and Visual Basic 6.0 Runtime allow remote attackers to execute arbitrary code via a crafted (a) web site, (b) Office document, or (c) .rtf file that triggers "system state" corruption, as exploited in the wild in April 2012, aka "MSCOMCTL.OCX RCE Vulnerability."
File information
English
1.the payload exe drops a digitally signed binary zl5.exe and English 英文.doc
File: inside information.doc
Size: 126583
MD5: 2B36C2A000FF2C43B30748B0F1FA088A
Taiwanese
2. the payload exe drops a digitally signed binary dy.exe and kong.doc
Size: 113283
MD5: D05E8B7EA5C6EBD3B04CF7F06ABB5217
Taiwanese
3. the payload exe drops a binary spoolsv.exe and 薄熙來唱紅打黑,為什麼會身敗名裂?.doc (Literal translation: Bo made famous triads, why ruin? - About Bo Xilai's mysterious incident)
Size: 150175
MD5: 896862D988A11E660A12ACE9A655EF3D
Taiwanese
4 the payload exe drops a binary spoolsv.exe and 南海爭端不斷,中共領導人態度如何? (South China Sea disputes continue,what's the attitude of the Chinese Communist leaders?)
Size: 113283
MD5: 62938DD8EC0E41EC3017E8A7820368D7
Update April 20, 2012
Thupten.doc
MD5: 326E7F206CC334C977AECBCF98B3AFA4
Virustotal
Mission Command Outline.doc
MD5: 894B0088E0D05A9012775A0343C37578
Virustotal
子女教育補助費101新版.doc (Children's education subsidy 101 new version)
MD5: 5149356B16FC21154610EB888D657F25
Virustotal
a.doc
MD5: 23615073E04166027E64F03810FDEA3F
Virustotal
oracle readme.doc
MD5: B15F0CC600698F9EEC080443FCBA0011
Virustotal
民進黨二零一二年整體規劃.doc (Democratic Progressive Party in 2012 the overall planning)
MD5: B537DA43DD9C371FE0589948F36AB6E2
Virustotal
1010415違規停車單.doc (1010415 parking violation single)
MD5: B6123D8AB10D1C5E5C06B38FD357151B
Virustotal
立法院101年4月國防部備詢(有關後備司-紅字)及詳細條文.doc )Legislative Yuan 101 in April the Department of Defense to provide advice (Reserve Division - The Scarlet Letter) and the detailed provisions)
MD5: DF70CD47EF972B89A035A5BECB9EE9E0
Virustotal
Download
Download all files, payload, pcaps, documents, etc (email me if you need the password)
Download April 20, 8 additional samples listed above
Exploit Information
The vulnerability is due to an error in ActiveX control, in this case embedded in an RTF document.
Object creation in RTF is nomally done in a format similar to this: {\object\objocx\objsetsize\objw3240\objh570{\*\objclass MyControl.MControl}...
It is documented in Rich Text Format (RTF) Specification, version 1.6
You can see ActiveX object embedded in the malicious document below.
All the documents have identical header
Payload
- The TW documents will execute only on the TW version of Windows (If you use English language Windows, look for ce24fa7f in the document - TW code and try to replace it with 7c874413 En).
- The TW doc binaries do not seem to have such an obvious indicator but would run only on TW Windows (at least in my case)
- Even if everything lines up, the documents are likely to crash Word = no joy
- You can carve them out manually. Didier Steven's XORSearch and a hex editor should work.
If you run it again with the key 0x3B, you will get the second exe that is inside the main binary, and in case with the digitally signed binaries, there is also a dl inside the second exe.
1
English 2B36C2A000FF2C43B30748B0F1FA088A1.the payload exe drops a digitally signed binary zl5.exe and English 英文.doc
File: inside information.doc
Size: 126583
MD5: 2B36C2A000FF2C43B30748B0F1FA088A
1. embedded payload
Size: 99839
MD5: 20C764DFA4363C6941D8F30CFF20C86B
|
2.creates
英文.doc -page filled with $$$
Size: 16384
MD5: 0D6D94001483C7BC7650AB2A3E98427A

|
2.creates in %Temp%
File: zl5.exe - digitally signed, WoSign certificate below
Size: 46040
MD5: D7549732C7E9446BDEB7CF93A08B0EEB
|
3. creates in Windows - the backdoor DLL
C:\WINDOWS\fxsst.dll - digitally signed, same signature
File: fxsst.dll
Size: 11176
MD5: C9D22E2EA93248097F88346C6CD31A32
 |
| Digital certificate WoSign |
Taiwanese D05E8B7EA5C6EBD3B04CF7F06ABB5217
2. the payload exe drops a digitally signed binary dy.exe and kong.doc
Size: 113283
1. embedded payload
File: taskmg.exe
Size: 309455
MD5: 36C480E5AA554197912D23D195D63503
|

2. creates in %Temp%
File: kong.doc - empty page
Size: 329036
MD5: D05E8B7EA5C6EBD3B04CF7F06ABB5217
|
2. creates in %Temp%
File: dy.exe - digitally signed with Verisign certificate. It gets renamed to a random ~4char such as ~11EEB
Size: 262824
MD5: 6905013AB9EFD159D942350A0E016D79
|
3. creates in Windows
c:\windows\eminfo.dl 273351ab967b5b475e70670eb55acac
 |
| Verisign Certificate |
Taiwanese
3. the payload exe drops a binary spoolsv.exe and 薄熙來唱紅打黑,為什麼會身敗名裂?.doc (Literal translation: Bo made famous triads, why ruin? - About Bo Xilai's mysterious incident) - in %Temp%
Size: 150175
MD5: 896862D988A11E660A12ACE9A655EF3D
|
2. creates in %temp%
File: spoolsv.exe
Size: 61440
MD5: 3B7CFF35DAB7A8C03478EA2069ED2060
Adds an autostart registry setting
|
2 creates in %temp%
薄熙來唱紅打黑,為什麼會身敗名裂?.doc
File: spoolsv.exe
Size: 61440
MD5: 3B7CFF35DAB7A8C03478EA2069ED2060
Registry
HKU\S-1-5-21-3907012051-1860774492-1815990957-1001\Software\Microsoft\Windows\CurrentVersion\Run\RUN: "C:\Users\[user]\AppData\Local\Temp\spoolsv.exe"
Taiwanese
4 the payload exe drops a binary spoolsv.exe and 南海爭端不斷,中共領導人態度如何? (South China Sea disputes continue,what's the attitude of the Chinese Communist leaders?) in %Temp%
Size: 113283
MD5: 62938DD8EC0E41EC3017E8A7820368D7
|
2 creates
File: spoolsv.exe
Size: 61440
MD5: 3B7CFF35DAB7A8C03478EA2069ED2060
|
2. creates
南海爭端不斷,中共領導人態度如何?.doc
Size: 20480
MD5: C265E2E8CE41B8C402778BA31DD0EBE4
Traffic information
to be continued ..
All pcaps are here
1






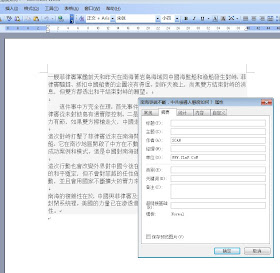



That is the document described here http://labs.alienvault.com/labs/index.php/2012/cve-2012-0158-tibet-targeted-attacks-and-so-on/ by Alienvault
ReplyDeleteyes, looks like a different MD5.
ReplyDeletethe same files from http://scan.xecure-lab.com/
ReplyDeleteDownload of additional file gives an error Mila.
ReplyDelete<a href="http://photographerinperth.jimdo.com/2012/03/28/guidelines-in-choosing-a-wedding-photographer-in-perth/>Wedding Photography Perth </a>
ReplyDeleteHi Mila. South China is by far the nearest and largest ocean that I have ever known. Thanks for this file.
Hi Mila. South China is by far the nearest and largest ocean that I have ever known. Thanks for this file.
ReplyDeletefitness centers minnesota
ReplyDeleteHello. There's an ongoing controversy about China owning something that they don't own. I hope they will realize that it's not theirs.