Thursday, October 28, 2010
Sunday, October 24, 2010
Oct 24 CVE-2010-2883 PDF Vision Poll Center from ynnchang@gmail.com
CVE-2010-2883 Stack-based buffer overflow in CoolType.dll in Adobe Reader and
Acrobat 9.3.4 and earlier allows remote attackers to execute arbitrary
code or cause a denial of service (application crash) via a PDF
document with a long field in a Smart INdependent Glyphlets (SING)
table in a TTF font, as exploited in the wild in September 2010.
NOTE: some of these details are obtained from third party information
 Download 20101024S01AL01PR1R.pdf as a password protected archive (contact me if you need the password)
Download 20101024S01AL01PR1R.pdf as a password protected archive (contact me if you need the password) From: 遠見民調中心 張雅琳 [mailto:ynnchang@gmail.com]
From: 遠見民調中心 張雅琳 [mailto:ynnchang@gmail.com] Sent: Sunday, October 24, 2010 11:51 PM
To: ynnchang@gmail.com
Subject: 遠見民調中心_台灣民心指數調查結果
遠見民調中心 設計與執行
台灣民心指數( Taiwan Public Mood Index, TPMI )
2010年10月調查結果
--------------------------------------------------------
遠見民調中心 張雅琳
Global Views Survey Research Center
104 台北市松江路93巷1號
行動:0916-828-482
電話:02-2517-3688分機638
專線:02-2517-8537
傳真:02-2517-6275
Chinese to English translation
From: Vision polling centers Zhang Yalin [mailto: ynnchang@gmail.com]Sent: Sunday, October 24, 2010 11:51 PMTo: ynnchang@gmail.comSubject: Vision polling center _ the findings of the Taiwan people index
Survey Center design and implementation of the vision
Taiwan Public Mood Index (Taiwan Public Mood Index, TPMI)
October 2010 survey results
-------------------------------------------------- ------
Vision polls Center Zhang Yalin
Global Views Survey Research Center
Lane 93, Sung Chiang Road, Taipei 104, No. 1
Action :0916 -828-482
Tel :02 -2517-3688 ext 638
Line :02 -2517-8537
Fax :02 -2517-6275
Survey Center design and implementation of the vision
Taiwan Public Mood Index (Taiwan Public Mood Index, TPMI)
October 2010 survey results
-------------------------------------------------- ------
Vision polls Center Zhang Yalin
Global Views Survey Research Center
Lane 93, Sung Chiang Road, Taipei 104, No. 1
Action :0916 -828-482
Tel :02 -2517-3688 ext 638
Line :02 -2517-8537
Fax :02 -2517-6275
File name:20101024S01AL01PR1R.pdf
http://www.virustotal.com/file-scan/report.html?id=0a45313368c6437fa419d034e0bdb6ca5eb6ca4359c607d90d1027ec7a6bfda8-1288175111
Submission date:2010-10-27 10:25:11 (UTC)
15/ 41 (36.6%)
AntiVir 7.10.13.47 2010.10.27 HTML/Malicious.PDF.Gen
Avast 4.8.1351.0 2010.10.27 PDF:CVE-2010-2883
Avast5 5.0.594.0 2010.10.27 PDF:CVE-2010-2883
AVG 9.0.0.851 2010.10.27 Exploit_c.KGX
BitDefender 7.2 2010.10.27 Exploit.PDF-TTF.Gen
Comodo 6526 2010.10.27 UnclassifiedMalware
DrWeb 5.0.2.03300 2010.10.27 Exploit.PDF.1641
F-Secure 9.0.16160.0 2010.10.27 Exploit.PDF-TTF.Gen
Fortinet 4.2.249.0 2010.10.27 PDF/CoolType!exploit.CVE20102883
GData 21 2010.10.27 Exploit.PDF-TTF.Gen
Ikarus T3.1.1.90.0 2010.10.27 Exploit.Win32.CVE-2010-2883
Microsoft 1.6301 2010.10.27 Exploit:Win32/CVE-2010-2883.A
PCTools 7.0.3.5 2010.10.27 HeurEngine.MaliciousExploit
Sophos 4.58.0 2010.10.27 Troj/PDFJs-NA
Symantec 20101.2.0.161 2010.10.27 Bloodhound.Exploit.357
Additional information
Show all
MD5 : 1618d09ff580014b251794222bb0f0f9
Saturday, October 16, 2010
Thursday, October 14, 2010
Oct 08 CVE-2010-2883 PDF Nuclear Challenges and Responses in the Century from JUN.Bong-Geun@ifans.go.kr
CVE-2010-2883 Stack-based buffer overflow in CoolType.dll in Adobe Reader and
Acrobat 9.3.4 and earlier allows remote attackers to execute arbitrary
code or cause a denial of service (application crash) via a PDF
document with a long field in a Smart INdependent Glyphlets (SING)
table in a TTF font, as exploited in the wild in September 2010.
NOTE: some of these details are obtained from third party information.
 Download Conference Information_2010 IFANS Conference on Global Affairs (1001) as a password protected archive (contact me if you need the password)
Download Conference Information_2010 IFANS Conference on Global Affairs (1001) as a password protected archive (contact me if you need the password)From: JUN.Bong-Geun@ifans.go.kr [mailto:JUN.Bong-Geun@ifans.go.kr]
Sent: Friday, October 08, 2010 1:43 PM
Subject: Nuclear Challenges and Responses in the Century
Dear all
We inform you of an event and expect your kindly opinions.
On October 4th-5th 2010, the IFANS Conference on Global Affairs in 2010, "Nuclear Challenges and Responses in the Century" is hosted by the Institute of Foreign Affairs and National Security (IFANS) and the Presidential Council for Future and Vision (PCFV), and is organized by the Institute of Foreign Affairs and National Security (IFANS),ROK.
At the conference,in-depth discussion is expected among international and Korean experts and turn-out policy recommendations in terms of three subjects.
The sessions and programs were attached to a file "Conference Information.pdf".
Headers
Received: (qmail 13720 invoked from network); 8 Oct 2010 01:43:34 -0000Received: from mail.tekkan.com (HELO mail.tekkan.com) (164.46.125.50)
by XXXXXXXXXXXXXXXXX; 8 Oct 2010 01:43:34 -0000
Received: from mofat-p6463dmel ([221.9.247.17])
by mail.tekkan.com (8.12.11.20060829/8.11.3) with SMTP id o981guo7022508;
Fri, 8 Oct 2010 10:42:59 +0900
Message-ID: <201010080142.o981guo7022508@mail.tekkan.com>
From: JUN.Bong-Geun@ifans.go.kr
To:
Subject: Nuclear Challenges and Responses in the Century
Date: Fri, 8 Oct 2010 10:43:08 -0700
X-Mailer: CSMTPConnection v2.17
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="ad7e60eb-fca5-415b-9c56-9d74439519e2"
Content-Transfer-Encoding: quoted-printable
Hostname: 221.9.247.17
ISP: China Unicom Jilin province network
Organization: China Unicom Jilin province network
Assignment: Static IP
Country: China
State/Region: Jilin
City: Changchun
Virustotal
http://www.virustotal.com/file-scan/report.html?id=0c8f17b2130addebcb2ca75bd7a982e37ddcc49d49e79fe60e3fda767f2ec972-1287057726
File name:Conference Information_2010 IFANS Conference on Global Af[...].pdf
Submission date:2010-10-14 12:02:06 (UTC)
Current status:
14/ 43 (32.6%)
Avast 4.8.1351.0 2010.10.14 PDF:CVE-2010-2883
Avast5 5.0.594.0 2010.10.14 PDF:CVE-2010-2883
AVG 9.0.0.851 2010.10.14 Exploit_c.LMW
BitDefender 7.2 2010.10.14 Exploit.PDF-TTF.Gen
Comodo 6388 2010.10.14 UnclassifiedMalware
F-Secure 9.0.16160.0 2010.10.14 Exploit.PDF-TTF.Gen
GData 21 2010.10.14 Exploit.PDF-TTF.Gen
Kaspersky 7.0.0.125 2010.10.14 Exploit.Win32.CVE-2010-2883.a
NOD32 5530 2010.10.14 JS/Exploit.Shellcode.A.gen
Norman 6.06.07 2010.10.14 HTML/Shellcode.Q
nProtect 2010-10-14.01 2010.10.14 Exploit.PDF-JS.Gen
PCTools 7.0.3.5 2010.10.14 Trojan.Pidief
Sophos 4.58.0 2010.10.14 Mal/JSShell-B
Symantec 20101.2.0.161 2010.10.14 Trojan.Pidief
Additional information
Show all
MD5 : 3abfe5fd78ffddebf23bd46edf4e4eb7
Created files
C:\windows\system32\syschk.ocx
File name: syschk.ocx
MD5 : 16ba21c1eac48eb20c04ac91ef9c2bd1
Submission date: 2010-10-16 04:33:16 (UTC)
Result: 0/ 43 (0.0%)
Strings (yes, C:\Documents and Settings\Mila\Desktop\Conference Information_2010 IFANS Conference on Global Affairs (1001).pdf" is not a accidental paste, it is in the file = inserted path from the original location of the pdf.
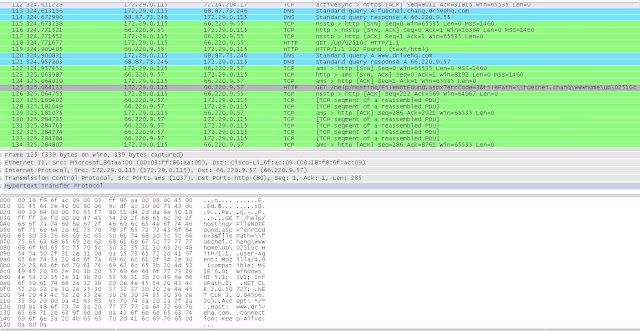
C:\windows\system32\form.ocx = same string as it tried to download = see the pcap screenshot below
File: form.ocx
MD5: 279b3b44fa1ac9e72d030ff42b1b77c6
Size: 15
Ascii Strings:
---------------------------------------------------------------------------
02510c
Unicode Strings:
---------------------------------------------------------------------------
MD5: 279b3b44fa1ac9e72d030ff42b1b77c6
Size: 15
Ascii Strings:
---------------------------------------------------------------------------
02510c
Unicode Strings:
---------------------------------------------------------------------------
66.220.9.57
Hostname: www.mbizgroup.bizISP: Hurricane Electric
Organization: LaFrance Internet Services
Proxy: None detected
Type: Corporate
Assignment: Static IP
Country: United States
State/Region: California
City: Fremont
Subscribe to:
Posts (Atom)