Exploit Information
More about RTLO is here Right to Left Override unicode can be used for multiple spoofing cases by Jordi Chancel:
"RTLO is a technique exploiting the RIGHT TO LEFT OVERRIDE unicode and than it will always cause the directional reverse reading order of others characters followed it including the extension-type of malicious file! This UNICODE of which we will simplify name by [RTLO] doesnt can see owing to the fact that its characters and its place are invisible. Use RTLO for reverse the direction of reading of the file names including the extension of concerned file while keeping same the types of execution.
Example: To use a syntax like “SexyPictureGirlAl[RTLO]gpj.exe” be read “SexyPictureGirlAlexe.jpg”
"RTLO is a technique exploiting the RIGHT TO LEFT OVERRIDE unicode and than it will always cause the directional reverse reading order of others characters followed it including the extension-type of malicious file! This UNICODE of which we will simplify name by [RTLO] doesnt can see owing to the fact that its characters and its place are invisible. Use RTLO for reverse the direction of reading of the file names including the extension of concerned file while keeping same the types of execution.
Example: To use a syntax like “SexyPictureGirlAl[RTLO]gpj.exe” be read “SexyPictureGirlAlexe.jpg”
General File Information
MD5:1c33fd879fa9690490f07c26d92724e3
File Type: scr
MD5 of archive 40A0EDE3656CD6E4D77B05175A8978FE
Malware: Taidoor / Rubinurd
Right to Left override in action
1) unzipped attachment on Windows with "Hide extensions for known file types" option UNCHECKED 2) unzipped attachment on Windows with "Hide extensions for known file types" option CHECKED (more common user option)
Download
Original Message
 From: theresa@iseas.edu.sg [mailto:theresa@iseas.edu.sg]
From: theresa@iseas.edu.sg [mailto:theresa@iseas.edu.sg]Sent: Friday, June 17, 2011 8:28 AM
Subject: South China Sea Territorial Disputes Study Update
Message Headers
Received: (qmail 15729 invoked from network); 17 Jun 2011 00:16:48 -0000Received: from msr15.hinet.net (HELO msr15.hinet.net) (168.95.4.115)
by xxxxxxxxxxxx with SMTP; 17 Jun 2011 00:16:48 -0000
Received: from appserver1 (210-242-240-217.HINET-IP.hinet.net [210.242.240.217] (may be forged))
(authenticated bits=0)
by msr15.hinet.net (8.14.2/8.14.2) with ESMTP id p5H0GjUp020385
for xxxxxxxxxx; Fri, 17 Jun 2011 08:16:47 +0800 (CST)
Message-ID: <201106170016.p5H0GjUp020385@msr15.hinet.net>
Subject: South China Sea Territorial Disputes Study Update
Date: Fri, 17 Jun 2011 08:28:02 -0400
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----=_NextPart_000_0008_01CC2C4B.E1FEE710"
X-Priority: 3
X-MSMail-Priority: Normal
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2800.2001
From: "theresa@iseas.edu.sg"
X-Mailer: JetMail 1.00
Sender
MSG SENDER HOST IP -(originating IP / sending server IP)
210-242-240-217.hinet-ip.hinet.net
Host reachable, 267 ms. average
Automated Scans
South China Sea Territorial Disputes_txt.scr
http://www.virustotal.com/file-scan/report.html?id=f1ce3364f61fa174f1f7fe887754e465939724e19cab205fefe56f490db7604f-1308884038
Submission date: 2011-06-24 02:53:58 (UTC)
Result: 20 /42 (47.6%)
AntiVir 7.11.10.83 2011.06.24 TR/Spy.88093.1
Antiy-AVL 2.0.3.7 2011.06.23 Trojan/Win32.Sasfis.gen
AVG 10.0.0.1190 2011.06.23 Generic22.CBLL
BitDefender 7.2 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
Commtouch 5.3.2.6 2011.06.24 W32/Trojan-Gypikon-based.BA!Maximus
eTrust-Vet 36.1.8403 2011.06.23 Win32/Fakedoc_i
F-Prot 4.6.2.117 2011.06.23 W32/Trojan-Gypikon-based.BA!Maximus
F-Secure 9.0.16440.0 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
GData 22 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
Jiangmin 13.0.900 2011.06.23 Trojan/Sasfis.qki
K7AntiVirus 9.106.4837 2011.06.23 Trojan
McAfee-GW-Edition 2010.1D 2011.06.24 Heuristic.LooksLike.Win32.Suspicious.J
Microsoft 1.7000 2011.06.23 VirTool:Win32/Injector.gen!BJ
NOD32 6234 2011.06.24 probably a variant of Win32/TrojanDropper.Agent.NM
PCTools 8.0.0.5 2011.06.23 Trojan.Gen
Sophos 4.66.0 2011.06.24 Troj/Mdrop-DMI
Symantec 20111.1.0.186 2011.06.24 Trojan.Gen
TheHacker 6.7.0.1.239 2011.06.23 Trojan/Sasfis.bkwo
VBA32 3.12.16.2 2011.06.23 Trojan.Sasfis.blce
VirusBuster 14.0.92.1 2011.06.23 Trojan.Agent!07xHu47lXUs
Additional informationShow all
MD5 : 1c33fd879fa9690490f07c26d92724e3
Submission date: 2011-06-24 02:53:58 (UTC)
Result: 20 /42 (47.6%)
AntiVir 7.11.10.83 2011.06.24 TR/Spy.88093.1
Antiy-AVL 2.0.3.7 2011.06.23 Trojan/Win32.Sasfis.gen
AVG 10.0.0.1190 2011.06.23 Generic22.CBLL
BitDefender 7.2 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
Commtouch 5.3.2.6 2011.06.24 W32/Trojan-Gypikon-based.BA!Maximus
eTrust-Vet 36.1.8403 2011.06.23 Win32/Fakedoc_i
F-Prot 4.6.2.117 2011.06.23 W32/Trojan-Gypikon-based.BA!Maximus
F-Secure 9.0.16440.0 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
GData 22 2011.06.24 Gen:Trojan.Heur.eqY@yvLalFaOf
Jiangmin 13.0.900 2011.06.23 Trojan/Sasfis.qki
K7AntiVirus 9.106.4837 2011.06.23 Trojan
McAfee-GW-Edition 2010.1D 2011.06.24 Heuristic.LooksLike.Win32.Suspicious.J
Microsoft 1.7000 2011.06.23 VirTool:Win32/Injector.gen!BJ
NOD32 6234 2011.06.24 probably a variant of Win32/TrojanDropper.Agent.NM
PCTools 8.0.0.5 2011.06.23 Trojan.Gen
Sophos 4.66.0 2011.06.24 Troj/Mdrop-DMI
Symantec 20111.1.0.186 2011.06.24 Trojan.Gen
TheHacker 6.7.0.1.239 2011.06.23 Trojan/Sasfis.bkwo
VBA32 3.12.16.2 2011.06.23 Trojan.Sasfis.blce
VirusBuster 14.0.92.1 2011.06.23 Trojan.Agent!07xHu47lXUs
Additional informationShow all
MD5 : 1c33fd879fa9690490f07c26d92724e3
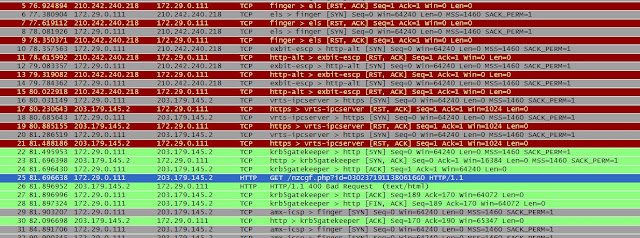
Traffic
GET /nzcgf.php?id=0302371911380616G0
HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Host: 203.179.145.2
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Host: 203.179.145.2
This is actually a name server and it is known to be spread malware Microsoft TrojanDownloader:Win32/Buzus.C
203.179.145.2
203.179.144.0 - 203.179.147.255
CNET Communications
Japan
C-NET
Updated: 16-Jul-2008
Source: whois.apnic.net
Server returns "Bad Request"
Ns2.cnet.ne.jp and ns.cnet.ne.jp point to 203.179.145.2. Sf-boon.jp, cnet.jp, atlansia.jp, shocker.jp, aohp.jp and at least seven other hosts use this as a name server
These are hosts using it as a name server
aohp.jp
atlansia.jp
azumino.matsumoto.nagano.jp
bonnou108.jp
cnet.jp
cnet.ne.jp
edeai-net.jp
gang.gr.jp
hrsw.co.jp
i-mode.gr.jp
oh-parts.co.jp
post.gr.jp
sf-boon.jp
shocker.jp
spire.co.jp
system.co.jp
system.jp
taira-f.co.jp
203.179.145.2
203.179.144.0 - 203.179.147.255
CNET Communications
Japan
C-NET
Updated: 16-Jul-2008
Source: whois.apnic.net
Server returns "Bad Request"







No comments:
Post a Comment