Common Vulnerabilities and Exposures (CVE)number
CVE-2009-0556 Microsoft Office PowerPoint 2000 SP3, 2002 SP3, and 2003 SP3, and PowerPoint in Microsoft Office 2004 for Mac, allows remote attackers to execute arbitrary code via a PowerPoint file with an OutlineTextRefAtom containing an an invalid index value that triggers memory corruption, as exploited in the wild in April 2009 by Exploit:Win32/Apptom.gen, aka "Memory Corruption Vulnerability."
CVE-2010-2572 Buffer overflow in Microsoft PowerPoint 2002 SP3 and 2003 SP3 allows remote attackers to execute arbitrary code via a crafted PowerPoint 95 document, aka "PowerPoint Parsing Buffer Overflow Vulnerability."
I would like to have a more technical analysis and identification of CVE in addition to this preliminary testing, so if you do it, please send over, I will add :) thank youUpdate
Comments: Shih-hao Weng (thank you) noted that he thinks it is CVE-2009-0556. I tested, indeed - the patch for CVE-2009-0556 (MS09-017 KB957784 May 12 2009) fixes it.
The only patch from Microsoft Updates that is automatically available and fixes it these days is MS10-088, which is for CVE-2010-2572. However MS10-088 replaced earlier patches, including MS09-017 ( CVE-2009-0556 ). CVE-2009-0556 was used a in a lot in malicious attachments in the past
You cannot automatically install MS09-017 via Microsoft Updates - see below but if you find it and install manually (for Sp3 MS09-017 KB957784 May 12 2009) . MS10-004 KB976881 Feb 4, 2010 would also fix it.
Everything in the post stays the same - except the CVE number changes to CVE-2009-0556 and the patches that will keep you safe are
For Office 2003 SP3
MS10-088, which is for CVE-2010-2572 OR MS09-017 KB957784 OR MS10-004 KB976881 Feb 4, 2010

General File Information
File Christmas Messages.pps
MD5 51d3e2bd306495de50bfd0f2f4e19ae9
SHA1 7edd6beff619f86fae7f94a60ac4bcdb04473dfb
Size : 838144 bytes
Type: PPS
Distribution: Email attachment
Download
Original Message
----From: Nicholas Bennett [mailto:nicholas.bennett53@hotmail.com]
Sent: Tuesday, December 21, 2010 3:55 AM
To: XXXXXXXXXXXXXXX
Subject: Merry Christmas
Message Headers
Received: (qmail 24066 invoked from network); 21 Dec 2010 08:54:35 -0000Received: from bay0-omc1-s18.bay0.hotmail.com (HELO bay0-omc1-s18.bay0.hotmail.com) (65.54.190.29)
by XXXXXXXXXXXXX; 21 Dec 2010 08:54:35 -0000
Received: from BAY151-W29 ([65.54.190.61]) by bay0-omc1-s18.bay0.hotmail.com with Microsoft SMTPSVC(6.0.3790.4675);
Tue, 21 Dec 2010 00:54:34 -0800
Message-ID:
Return-Path: nicholas.bennett53@hotmail.com
Content-Type: multipart/mixed;
boundary="_7d9b2e1f-3824-4d24-b8c6-8bc05c44f45b_"
X-Originating-IP: [203.241.121.122]
From: Nicholas Bennett
To: XXXXXXXXXXXXXXXX
Subject: Merry Christmas
Date: Tue, 21 Dec 2010 08:54:35 +0000
Importance: Normal
MIME-Version: 1.0
X-OriginalArrivalTime: 21 Dec 2010 08:54:34.0902 (UTC) FILETIME=[B0CB2360:01CBA0EC]
Sender
203.241.121.122Hostname: 203.241.121.122
ISP: KRNIC
Organization: KRNIC
Geolocation Information
Country: Korea, Republic of
City: Seoul
Automated Scans
File name:Christmas Messages.ppshttp://www.virustotal.com/file-scan/report.html?id=c73f01790f1b4353a1df823c50ce23233e54fc3535ce921587d194d02bc778c9-1293035579
Submission date:2010-12-22 16:32:59 (UTC)
Result:8/ 43 (18.6%)
BitDefender 7.2 2010.12.22 Exploit.PPT.Gen
F-Secure 9.0.16160.0 2010.12.22 Exploit.PPT.Gen
GData 21 2010.12.22 Exploit.PPT.Gen
McAfee-GW-Edition 2010.1C 2010.12.22 Heuristic.BehavesLike.Exploit.P97.CodeExec.PGPG
Norman 6.06.12 2010.12.22 ShellCode.D
nProtect 2010-12-22.01 2010.12.22 Exploit.PPT.Gen
Sophos 4.60.0 2010.12.22 Troj/ExpPPT-A
TrendMicro-HouseCall 9.120.0.1004 2010.12.22 HEUR_OLEXP.B
MD5 : 51d3e2bd306495de50bfd0f2f4e19ae9
SHA1 : 7edd6beff619f86fae7f94a60ac4bcdb04473dfb
Technical details / CVE ID/ Patch
Microsoft PowerPoint 'PP7X32.DLL' (CVE-2010-2572) Remote Heap-Based Buffer Overflow Vulnerability
Check your powerpoint.exe version. If it is below 11.0.8324.0 (Office 2003 SP3), it is vulnerable to this exploit. MS Office 2003 SP2 is vulnerable too.
Patch to install
Microsoft Security Bulletin MS10-088 - Important Vulnerabilities in Microsoft PowerPoint Could Allow Remote Code Execution (2293386) Published: November 09, 2010 | Updated: November 17, 2010
Update
Comments: Shih-hao Weng (thank you) noted that he thinks it is CVE-2009-0556. I tested, indeed - the patch for CVE-2009-0556 (MS09-017 KB957784 May 12 2009) fixes it.
The only patch from Microsoft Updates that is automatically available and fixes it these days is MS10-088, which is for CVE-2010-2572. However MS10-088 replaced earlier patches, including MS09-017 ( CVE-2009-0556 ). CVE-2009-0556 was used a in a lot in malicious attachments in the past
You cannot automatically install MS09-017 via Microsoft Updates - see below but if you find it and install manually (for Sp3 MS09-017 KB957784 May 12 2009) . MS10-004 KB976881 Feb 4, 2010 would also fix it.
Everything in the post stays the same - except the CVE number changes to CVE-2009-0556 and the patches that will keep you safe are
For Office 2003 SP3
MS10-088, which is for CVE-2010-2572 OR MS09-017 KB957784 OR MS10-004 KB976881 Feb 4, 2010
If your PowerPoint is patched, you will see the screen with characters and gibberish like below and no files will be created on the system.
----------------------------
If your PowerPoint is NOT patched with MS10-0188, you will see a lame postcard like this, which is the decoy created files called Greeting Cards.pps (File: Greeting Cards.pps Size: 73216 MD5: DB8461E9FB762339ECECFCD39B747070)
All Office updates installed except one
Files Created
%userprofile%\Local Settings\
File.exe
0/43
http://www.virustotal.com/file-scan/report.html?id=90ab35c72748b39fb60b9652b7aaca89248b48f7e88707334e104fdb146bb978-1293036836
Threatexpert report
http://www.threatexpert.com/report.aspx?md5=b6428851df75dc91bb46583b97d9a566
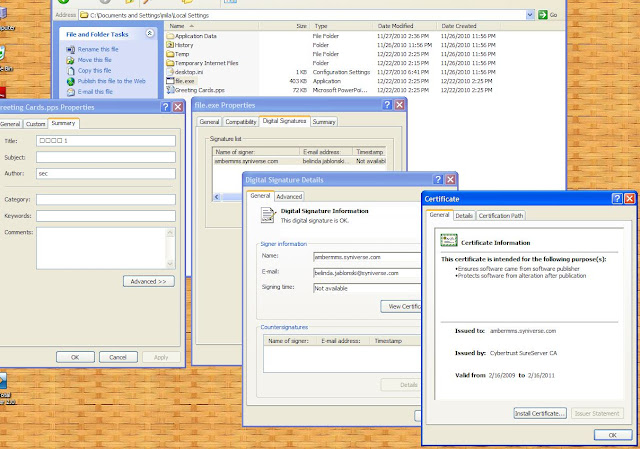
The file file.exe has a valid digital signature
- The following files were created in the system:
# Filename(s) File Size File Hash Alias 1 %AppData%\Microsoft\Windows\system32\winnet32.exe 16,384 bytes MD5: 0x428EB3305D4D4C9A8831E1D54160ED65
SHA-1: 0xA034527C2BEE5ED485F42F2965471CE0EB8BCCE9TrojanDownloader:Win32/Garveep.A [Microsoft]
Trojan-Downloader.Win32.Garveep [Ikarus]2 %System%\Greeting Cards.pps 73,216 bytes MD5: 0x0003AB50A5ADD661BEA69E97190D6143
SHA-1: 0x09C94C39B38FB03AB70012ED2A8B179FB685CC7E(not available) 3 [file and pathname of the sample #1] 411,944 bytes MD5: 0xB6428851DF75DC91BB46583B97D9A566
SHA-1: 0xD589836634848E97D3BF62EC77E3FC8B3E685B31(not available)
- The following Registry Key was created:
- HKEY_CURRENT_USER\Software\WinRAR SFX
- The newly created Registry Values are:
- [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
- winnet32.exe = "%AppData%\microsoft\windows\system32\winnet32.exe"
so that winnet32.exe runs every time Windows starts
- [HKEY_CURRENT_USER\Software\WinRAR SFX]
- C%%Documents and Settings%%UserName%%Application Data%Microsoft%Windows%system32 = "%AppData%\Microsoft\Windows\system32"
- Analysis of the file resources indicate the following possible country of origin:
Republic of Korea
ambermms.syniverse.com
belinda.jablonski@syniverse.com
Issuer
CN = Cybertrust SureServer CA
O = GlobalSign Inc
O = GlobalSign Inc
Valid from Monday, February 16, 2009 1:44:52 PM
Valid to Wednesday, February 16, 2011 1:44:52 PM
@MichaelFelch (thank you) noted that the stolen certificate belongs to a company with Taiwan headquarters located not too far from Hsinchu Science Park, Taiwan
On July 17th, ESET identified a new malicious file related to the Win32/Stuxnet worm. This new driver is a significant discovery because the file was signed with a certificate from a company called "JMicron Technology Corp". This is different from the previous drivers which were signed with the certificate from Realtek Semiconductor Corp. It is interesting to note that both companies whose code signing certificates were used have offices in Hsinchu Science Park, Taiwan.syniverse.com
http://www.syniverse.com/asia-pacific
Phone: (886) 2 27782977
Fax: (886) 2 27783690
Rm. 708, 7F
No.205, Sec. 1, Dunhua S. Rd.
Da’an Dist., Taipei City 106
Taiwan (R.O.C.)
Maybe Synverse have an office in the Hsinchu Science Park or maybe it is not related and just a coincidence, let me know if you find it out.
About Syniverse ( sounds like files signed by their certificates would be whitelisted in 6 out of 10 US banks and many other companies )
(thanks to @dkulshitsky for the link)
MES Spotlight: Financial Services
- 6 of the top 10 U.S. banks rely on Syniverse to enable comprehensive mobile banking SMS services including account balance, transaction history, overdraft, and bill payment alerts.
- 3 of the top 5 credit card issuers entrust Syniverse to provide account balance, last five transactions, fraud and overdraft alerts to mobile users.
- PayPal and top banks in the U.S. and India use Syniverse one-time-password (OTP) SMS services to protect mobile customers and prevent fraud.
- A leader in online payment solutions enables their customers, via two-way SMS messaging to a dedicated short code, to check balances, send and request money and text to buy.
- A leader in money transfer• services leverages the Syniverse messaging solution to deliver bill and payment due alert notifications and initiate payments via SMS.
- 3 major banks in Asia rely on Syniverse to power their mobile banking and alerting services in over 129 countries globally.
Certificate belongs to
http://www.linkedin.com/pub/dir/Belinda/Jablonski
IS Compliance Manager at Syniverse Technologies Inc.
winnet32.exe (saved in %AppData%\Microsoft\Windows\system32\)
Downloaded file (by file.exe)
from hXXp://88dafa.biz/main/winnet32.exe
File name:winnet32.exe
http://www.virustotal.com/file-scan/report.html?id=3449b1d75b5cba3cc941a2cbaaf6d0e37d22f36a7f947721767e87c16f889e02-1293043526
Submission date:2010-12-22 18:45:26 (UTC)
Result:4/ 43 (9.3%)
Emsisoft 5.1.0.1 2010.12.22 Trojan-Downloader.Win32.Garveep!IK
Ikarus T3.1.1.90.0 2010.12.22 Trojan-Downloader.Win32.Garveep
Microsoft 1.6402 2010.12.22 TrojanDownloader:Win32/Garveep.A
NOD32 5725 2010.12.22 probably a variant of Win32/TrojanDownloader.Small.OZT
MD5 : 428eb3305d4d4c9a8831e1d54160ed65
http://www.virustotal.com/file-scan/report.html?id=3449b1d75b5cba3cc941a2cbaaf6d0e37d22f36a7f947721767e87c16f889e02-1293043526
Network activity
- There were registered attempts to establish connection with the remote hosts. The connection details are:
| Remote Host | Port Number |
| 124.217.255.232 | 80 |
| 174.120.232.252 | 80 |
- The data identified by the following URLs was then requested from the remote web server:
- http://88dafa.biz/main/winnet32.exe
- http://checkingvirusscan.com/Base/chkver.php
- http://checkingvirusscan.com/Base/chkpage.php?un=Q29tcHV0ZQ==
124.217.255.232
Hostname: penguin1.ip-asia.comISP: PIRADIUS NET
Organization: PIRADIUS NET
Assignment: Static IP
Country: Malaysia
State/Region: Johor
City: Johor Bahru













Thank you Mila. And merry christmas!
ReplyDeleteThanks !
ReplyDelete