Common Vulnerabilities and Exposures (CVE)number
CVE-2010-3970 Stack-based buffer overflow in the CreateSizedDIBSECTION function in shimgvw.dll in the Microsoft Graphics Rendering Engine in Windows XP SP3, Server 2003 SP2, Vista SP1 and SP2, and Server 2008 SP2 allows remote attackers to execute arbitrary code via a crafted .MIC or unsplecified Office document containing a thumbnail bitmap with a negative biClrUsed value, as reported by Moti and Xu Hao.
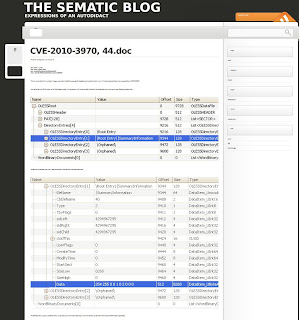
General File Information
File 44.doc (part of ATT63777.7z archive)MD5 f51d3fb324d8f11b734ca63dbccbdc32SHA1 b3c4c84c98c6befaf6a480ae145cdcebb5929a82File size : 10240 bytesType: DOC
Distribution: Email attachment
Post Update - Vulnerability Analysis
Feb 23 Sematic blog posted an excellent analysis of the exploit
Ultimately it plans to fetch and execute the file located at:
hxxp://stonebreaker.154.99lm.info/NOTEPAD.EXE
This file would be stored under %SYSTEM32% as 'a.exe'.
Download
Malware Information
The malicious word document was sent inside a 7zip archive folder with 43 non-malicious image files. Due to this, a recipient is likely to switch to the 'thumbnails' or filmstrip view, which triggers the exploit. It crashed explorer.exe but nothing else during all the tests.
This vulnerability was disclosed by Moti and Xu Hao during POC 2010 - international security & hacking conference in Korea, which took place on December 14-15, 2010. You can view their slides here http://www.exploit-db.com/author/?a=3094.
Metasploit added this exploit (by jduck) on January 4, 2011. http://downloads.securityfocus.com/vulnerabilities/exploits/45662.rb
This particular file appears to be metasploit generated (thanks to Steven Adair for checking this) but it does not work. I am posting it anyway because it is is a very notable attempt to use a new unpatched (except for the manual Fix-it) vulnerability in a targeted attack.
This vulnerability affects Windows 2000, XP, and Server 2003. It was tested on XP SP2 and XP3 without any patches with DEP on and DEP off without any success. If you make it work, let me know.
The message sent in Chinese, from a Korean hosting company IP address, using a Yahoo Taiwan webmail address.
Original Message
From: 空白空白 [mailto:dogviceroy@yahoo.com.tw]Sent: Monday, January 24, 2011 9:58 PM
To: XXXXXXX
Subject: 百變廖了以——廖了以從政圖集
國民黨新任秘書長廖了以從政圖集,看看他的百變人生。
machine translation:
Variety Liao taking - taking political atlas Liao
KMT Secretary-General Liao a new political atlas ...
KMT Secretary-General Liao a new political atlas ...
about the general:
http://en.wikipedia.org/wiki/Liao_Xilong
Message Headers
Received: (qmail 19994 invoked from network); 25 Jan 2011 02:58:34 -0000Received: from omp1004.mail.tp2.yahoo.com (HELO omp1004.mail.tp2.yahoo.com) (203.188.200.63)
by XXXXXXXXXXXXXXXX with SMTP; 25 Jan 2011 02:58:34 -0000
Received: (qmail 89001 invoked by uid 1000); 25 Jan 2011 02:57:45 -0000
Received: (qmail 51287 invoked by uid 60001); 25 Jan 2011 02:57:44 -0000
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=yahoo.com.tw; s=s1024; t=1295924263; bh=Z0LAcyDUZ2z7IpHzTTg3KMfi8jZPRcfmWkcH4Qb+a5s=; h=Message-ID:X-YMail-OSG:Received:X-Mailer:Date:From:Subject:To:MIME-Version:Content-Type; b=p44FQx52jjZ1acEA3Blwqf42wkC6tdcpnct4q0uIT6mr01sDUstZnHQUMTlrxV6UAKdi3KQ2s8NAF1t/JXFYqSp5J8vNDvMtH/TyMnsapel70Y4JSYg2IR6KkA6lJFDdF+WOCTfNL2yqHVW8Woice1mofVlW89pbxbZxDQ8XxQw=
DomainKey-Signature: a=rsa-sha1; q=dns; c=nofws;
s=s1024; d=yahoo.com.tw;
h=Message-ID:X-YMail-OSG:Received:X-Mailer:Date:From:Subject:To:MIME-Version:Content-Type;
b=No4vaskPIc/u09tdZw0QClwv475jFzh0S62JrXMxwNJnN+Da+cSajWNhnP8I8yJYa5bCgPOwMqjG3m538texlZ8qQfsFHTuY1+PxCEgpvUba9Ydkd3z1/C6PlJXp/Uhz41r9pewM58iO4RAezSEuMA+pUYnQ/AdDbcaUw0pnUf8=;
Message-ID: <601085.46984.qm@web74220.mail.tp2.yahoo.com>
X-YMail-OSG: dL9.0vwVM1lBL6b9cdApJJGfAs7gOVzx._rBgfQPeeX9Ufb
nyW0YDzHAdlD7_BMwmEbs8k6b3eGkQDiIK8Zge2nvHZ_a_sjwREX_BY_A4rB
n4VxHvovE5gvmxHMydO2ucX17d.CGb0Yw5hFwMWstFPdbG1hkC.v0vOYbTnc
issBgj6yxpc2wv8PB4EqtVEdWKBttfERKBhIcNWoJtpQmdQmO3_eIs04eQ_2
flz.arIvspKrmCQu9W1SWsFwwx6ESsHP9ptTvuEN_Ikn_vffzlKl6kV7GFAn
FSgxte_9Omh0-
Received: from [110.45.138.144] by web74220.mail.tp2.yahoo.com via HTTP; Tue, 25 Jan 2011 10:57:43 CST
X-Mailer: YahooMailClassic/11.4.20 YahooMailWebService/0.8.107.285259
Date: Tue, 25 Jan 2011 10:57:43 +0800
From: =?big5?B?qsWl1arFpdU=?=
Subject: =?big5?B?psrF3Ln5pEalSKFYoVi5+aRGpUixcaxGuc+2sA==?=
To: XXXXXXXXXXXXXXX
MIME-Version: 1.0
Content-Type: multipart/mixed; boundary="0-28100207-1295924263=:46984"
Sender
110.45.138.144
Hostname: 110.45.138.144
ISP: LG DACOM KIDC
Organization: LG DACOM KIDC
Country: Korea
ISP: LG DACOM KIDC
Organization: LG DACOM KIDC
Country: Korea
This is a hosting company
Automated Scans
44.dochttp://www.virustotal.com/file-scan/report.html?id=3c93c476a5fdc7e62626dfc2587c4d75f5a2c12dfda8693184f0b6de2095fc30-1296875631
Submission date:2011-02-05 03:13:51 (UTC)
Result:11 /43 (25.6%)
AntiVir 7.11.2.80 2011.02.04 EXP/CVE-2010-3970
Avast 4.8.1351.0 2011.02.04 DIB:CVE_2010_3970
Avast5 5.0.677.0 2011.02.04 DIB:CVE_2010_3970
Commtouch 5.2.11.5 2011.02.05 CVE-2010-3970!Camelot
GData 21 2011.02.05 DIB:CVE_2010_3970
Kaspersky 7.0.0.125 2011.02.05 Exploit.Win32.CVE-2010-3970.a
McAfee 5.400.0.1158 2011.02.05 Exploit-CVE2010-3970
McAfee-GW-Edition 2010.1C 2011.02.05 Exploit-CVE2010-3970
NOD32 5847 2011.02.04 a variant of Win32/Exploit.CVE-2010-3970.A
PCTools 7.0.3.5 2011.02.04 Trojan.Generic
Symantec 20101.3.0.103 2011.02.05 Trojan Horse
MD5 : f51d3fb324d8f11b734ca63dbccbdc32








No comments:
Post a Comment