| fputlsat.dll |
Contagio: Sept. 23 CVE-2011-1991 type (1) deskpan.dll Windows components DLL loading vulnerability
and
Contagio: Apr 13 CVE-2011-2100 PDF - Adobe DLL Loading Vulnerability - Agenda.7z
DLL search order hijacking exploits had and will have many new reincarnations because of the DLL loading preference order - Current Working Directory is preferred for most DLL files. You can read more about the root of these problems (not necessarily related to MS Office but in general) in M-unition: DLL Search Order Hijacking Revisited by Nick Harbour
As described in the Symantec article, fputlsat.dll must be present in the same directory as the Word document in order to be activated by the ActiveX control embedded in the Word document. The payload of this sample is a backdoor trojan Nflog.
Common Vulnerabilities and Exposures (CVE)number
CVE-2011-1980 Untrusted search path vulnerability in Microsoft Office 2003 SP3 and 2007 SP2 allows local users to gain privileges via a Trojan horse DLL in the current working directory, as demonstrated by a directory that contains a .doc, .ppt, or .xls file, aka "Office Component Insecure Library Loading Vulnerability."
Microsoft Security Bulletin MS11-073 - Important Vulnerabilities in Microsoft Office Could Allow Remote Code Execution (2587634)
- Symantec: New Targeted Attack Using Office Exploit Found In The Wild by Joji Hamada
General File Information
File: 275c5ac2067d17187a71b94ccfdc4608.doc
Size: 22016
MD5: 275C5AC2067D17187A71B94CCFDC4608
File: fputlsat.dll
Size: 126976
MD5: 60068812B59E58D6338AAEBD649F9020
Download
File Desription
File: 275c5ac2067d17187a71b94ccfdc4608.doc
Size: 22016
MD5: 275C5AC2067D17187A71B94CCFDC4608
 |
| Before the document is open - DLL file is present is the same directory |
The Word document has embedded macro - ActiveX List View Form Control, a very common ActiveX control, which calls fputlsat.dll "Microsoft Office FrontPage Client Utility Library". There is nothing unusual about this behavior, you can read more about this particular control here "Using the ListView ActiveX Control" and it is normal for it to call Frontpage libraries.
The vulnerability presents itself in the in the fact that a DLL located in
 |
| After the document is open. DLL file is renamed to Thumbs.db |
 |
| Activity after the exploit launch |
Examination of the ActiveX component shows the original path of the macro/control as it existed on the author's computer C:\Documents and Settings\Bandit\Local Settings\Temp\Word8.0\FPDTC.DLL (nice user name)
Office 8.0 is office 97 (yes, eons ago) and FPDTC.DLL is a Front Page Design Time Control that was used around 2000-2001. Considering this, I wonder if this vulnerability not only existed but also was used with minor tweaks through all versions of MS Office - starting with Office 97 and ending with Office 2010 we finally found it out. Perhaps, Microsoft Office/VB gurus will be able to answer and / or correct me.
 |
| List view control |
Upon launch, the user is presented with a choice to Run or not to run ActiveX controls. By that time the exploit already worked and the files were dropped/renamed. Anwering Yes will allow the dropped payload iede32.ocx to run.
 | ||
| ActiveX prompt. |
The picture below shows locations of the dropped file and the registry changes.
SVCHOST.EXE process injection
File: fputlsat.dll
Size: 126976
MD5: 60068812B59E58D6338AAEBD649F9020
fputlsat.dll (thumbs.db) strings
Unicode Strings:
---------------------------------------------------------------------------
Adobe Photoshop ---- ???
Adobe Photoshop 6.0 ----- ? Unknown if these artifacts mean anything. Photoshop is just as old. May be same DLL code was used for other products.
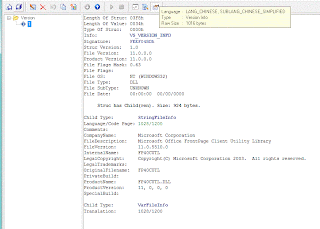
VS_VERSION_INFO
StringFileInfo
040404b0
Comments
CompanyName
Microsoft Corporation
FileDescription
Microsoft Office FrontPage Client Utility Library
FileVersion
11.0.5510.0
InternalName
FP40CUTL
LegalCopyright
Copyright(C) Microsoft Corporation 2003. All rights reserved.
LegalTrademarks
OriginalFilename
FP40CUTL
PrivateBuild
ProductName
FP40CUTL.DLL -- Frontpage 2000 file. Wonder if Word 2000 was affected too.
ProductVersion
11, 0, 0, 0
SpecialBuild
VarFileInfo
Translation
Created Files
File: iede32.ocxSize: 13824
MD5: D4859FC951652B3C9657F8621D4DB625
Virustotal
The trojan starts its activity POST /NfLog/Nfile.asp, this trojan is not new, for example there were Zero day CVE-2011-2462 files carrying the same trojan. The service modified is irmon (frequently abused by these types of attacks - here is a ThreatExpert report of a very common APT backdoor using the same service
List of strings
Key Name: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Irmon\Parameters
Class Name: <NO CLASS>
Last Write Time: 2/14/2012 - 1:40 AM
Value 0
Name: ServiceDll
Type: REG_EXPAND_SZ
Data: C:\WINDOWS\system32\iede32.ocx
Traffic
POST /IElog/TestURL.asp HTTP/1.0
User-Agent: www
Host: www.aviraco.com
Content-Length: 10
Pragma: no-cache
User-Agent: www
Host: www.aviraco.com
Content-Length: 10
Pragma: no-cache
1234567890HTTP/1.1 400 Bad Request
Content-Type: text/html
Date: Tue, 14 Feb 2012 05:39:57 GMT
Connection: close
Content-Length: 39
<h1>Bad Request (Invalid Hostname)</h1>
Domain Name : aviraco.com
PunnyCode : aviraco.com
Creation Date : 2011-03-30 10:31:10
Updated Date : 2011-03-30 10:31:10
Expiration Date : 2012-03-30 10:31:10
Registrant:
Organization : zhipengwang
Name : zhipengwang
Address : Zhongguancun Hailong Building, Room 1005
City : haidianqu
Province/State : beijingshi
Country : china
Postal Code : 100083
216.83.63.147
Host reachable, 408 ms. average
216.83.32.0 - 216.83.63.255
Ethr.Net LLC
7960B Soquel Dr. #417
Aptos
CA
95003
United States
SHA256: 429f206f2c68014c75f8a6ae09e68dd672401e461dd2fa72b9087bb5ee530d1e
SHA1: 7dbf130964cdc0110fd517a5d98188df3d56e850
MD5: 275c5ac2067d17187a71b94ccfdc4608
File size: 21.5 KB ( 22016 bytes )
File name: report.doc
File type: MS Word Document
Detection ratio: 17 / 43
Analysis date: 2012-02-15 04:10:05 UTC ( 46 minutes ago )
Antivirus Result Update
AhnLab-V3 Dropper/Ms11-073 20120213
AVG Exploit_c.UDK 20120213
ClamAV Exploit.Doc-2 20120214
Emsisoft Exploit.MSWord.CVE-2011!IK 20120214
eSafe - 20120213
eTrust-Vet - 20120213
Fortinet W97M/CVE_2011_1980.A!exploit 20120214
Ikarus Exploit.MSWord.CVE-2011 20120214
Kaspersky Exploit.MSWord.CVE-2011-1980.a 20120214
McAfee Exploit-CVE2011-1980 20120214
McAfee-GW-Edition - 20120213
Microsoft Exploit:Win32/Actjack.A 20120213
NOD32 W97M/Exploit.CVE-2011-1980.A 20120214
nProtect Trojan-Exploit/W32.Agent.22016 20120213
PCTools Trojan.Generic 20120207
Sophos Troj/Hijack-H 20120214
SUPERAntiSpyware - 20120206
Symantec Trojan.Activehijack 20120214
TrendMicro TROJ_ACTIVEHIJ.A 20120213
TrendMicro-HouseCall TROJ_ACTIVEHIJ.A 20120214
ViRobot Doc.S.MS11-073.22016 20120213
Virustotal
SHA256: 48bc6c0df3302f7eaa6061c4f3b0357b4c512d5bd6f6088abc6fc274f2efc5aa
SHA1: 8f86b7fcaf0c1ee9b795fa8e559def47ef468128
MD5: 60068812b59e58d6338aaebd649f9020
File size: 124.0 KB ( 126976 bytes )
File name: fputlsat.dll
File type: Win32 DLL
Detection ratio: 28 / 43
Analysis date: 2012-02-15 04:10:02 UTC ( 23 minutes ago )
AhnLab-V3 Win-Trojan/Activehijack.126976 20120213
AntiVir TR/Drop.Kaliox.A 20120213
Avast Win32:Malware-gen 20120214
BitDefender Trojan.Generic.KD.529689 20120214
DrWeb Trojan.MulDrop3.34467 20120214
Emsisoft Trojan-Dropper.Win32.Agent!IK 20120214
F-Secure Trojan.Generic.KD.529689 20120214
Fortinet W32/Agent.PRG!tr 20120214
GData Trojan.Generic.KD.529689 20120214
Ikarus Trojan-Dropper.Win32.Agent 20120214
K7AntiVirus Riskware 20120213
Kaspersky Trojan-Dropper.Win32.Agent.gjnt 20120214
McAfee Generic Dropper.p 20120214
McAfee-GW-Edition Artemis!60068812B59E 20120213
Microsoft TrojanDropper:Win32/Kaliox.A 20120213
NOD32 Win32/TrojanDropper.Agent.PRG 20120214
Norman W32/Agent.XGSO 20120213
nProtect Trojan-Dropper/W32.Agent.126976.CS 20120213
PCTools Trojan.Dropper 20120207
Symantec Trojan.Dropper 20120214
TrendMicro TROJ_MULDROP.IC 20120213
TrendMicro-HouseCall TROJ_MULDROP.IC 20120214
VIPRE Trojan.Win32.Generic!BT 20120214
ViRobot Trojan.Win32.Activehijack.126976 20120213
VirusBuster Trojan.DR.Agent!ly6ZRARwo6A
Virustotal
SHA256: 27c87e7993c5661dd3b65e51df5884519fc0234bf36de72082644fa909ccb793
SHA1: d0c3e34bd97c4aa56fe9f176954d274595926a32
MD5: d4859fc951652b3c9657f8621d4db625
File size: 13.5 KB ( 13824 bytes )
File name: iede32.ocx
File type: Win32 DLL
Detection ratio: 28 / 42
Analysis date: 2012-02-14 04:13:46 UTC ( 1 day, 2 hours ago )
0
AhnLab-V3 Win-Trojan/Activehijack.13824 20120213
AntiVir TR/Spy.13824.71 20120214
Antiy-AVL Trojan/Win32.Genome.gen 20120213
BitDefender Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Comodo TrojWare.Win32.GameThief.Nilage.~CRSH 20120214
DrWeb Trojan.Click2.13847 20120214
Emsisoft Trojan.Win32.Spy!IK 20120214
eSafe Win32.GenHeur.LP.Aq@ 20120213
F-Secure Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Fortinet W32/Agent.OLJ 20120214
GData Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Ikarus Trojan.Win32.Spy 20120214
K7AntiVirus Riskware 20120213
Kaspersky Trojan.Win32.Genome.aehtz 20120214
McAfee Generic Dropper.p 20120214
McAfee-GW-Edition Artemis!D4859FC95165 20120213
Microsoft TrojanDownloader:Win32/Kaliox.A 20120213
NOD32 Win32/Agent.OLJ 20120214
Norman W32/Troj_Generic.KIKX 20120213
nProtect Trojan/W32.Genome.13824.J 20120213
Sophos Troj/Spy-YL 20120214
Symantec Trojan.Gen.2 20120214
TheHacker Trojan/Agent.olj 20120213
TrendMicro BKDR_CONIP.A 20120214
TrendMicro-HouseCall BKDR_CONIP.A 20120214
ViRobot Trojan.Win32.Activehijack.13824 20120214
VirusBuster Trojan.Agent!KGIS/NcFcUc 20120213
Host reachable, 408 ms. average
216.83.32.0 - 216.83.63.255
Ethr.Net LLC
7960B Soquel Dr. #417
Aptos
CA
95003
United States
| IP Address History Event Date Action Pre-Action IP Post-Action IP 2009-12-28 New -none- 174.37.172.68 2010-09-13 Change 174.37.172.68 67.228.81.181 2010-09-24 Change 67.228.81.181 174.37.172.68 2011-02-02 Change 174.37.172.68 67.228.81.180 2011-02-13 Not Resolvable 67.228.81.180 -none- 2011-10-14 New -none- 98.126.113.28 2011-10-25 Change 98.126.113.28 216.83.63.14 Registrar History Date Registrar 2009-12-26 Name.com aka DomainSite 2011-03-29 Xin Net Name Server History Event Date Action Pre-Action Server Post-Action Server 2009-12-28 New -none- Name.com 2011-02-08 Delete Name.com -none- 2011-03-31 New Xinnet.cn Xinnetdns.com 2011-12-13 Transfer Xinnetdns.com Xincache.com RR www.comedns.com. A 216.83.63.147 www.creamofa.com. A 216.83.63.147 |
Automated Scans
VirustotalSHA256: 429f206f2c68014c75f8a6ae09e68dd672401e461dd2fa72b9087bb5ee530d1e
SHA1: 7dbf130964cdc0110fd517a5d98188df3d56e850
MD5: 275c5ac2067d17187a71b94ccfdc4608
File size: 21.5 KB ( 22016 bytes )
File name: report.doc
File type: MS Word Document
Detection ratio: 17 / 43
Analysis date: 2012-02-15 04:10:05 UTC ( 46 minutes ago )
Antivirus Result Update
AhnLab-V3 Dropper/Ms11-073 20120213
AVG Exploit_c.UDK 20120213
ClamAV Exploit.Doc-2 20120214
Emsisoft Exploit.MSWord.CVE-2011!IK 20120214
eSafe - 20120213
eTrust-Vet - 20120213
Fortinet W97M/CVE_2011_1980.A!exploit 20120214
Ikarus Exploit.MSWord.CVE-2011 20120214
Kaspersky Exploit.MSWord.CVE-2011-1980.a 20120214
McAfee Exploit-CVE2011-1980 20120214
McAfee-GW-Edition - 20120213
Microsoft Exploit:Win32/Actjack.A 20120213
NOD32 W97M/Exploit.CVE-2011-1980.A 20120214
nProtect Trojan-Exploit/W32.Agent.22016 20120213
PCTools Trojan.Generic 20120207
Sophos Troj/Hijack-H 20120214
SUPERAntiSpyware - 20120206
Symantec Trojan.Activehijack 20120214
TrendMicro TROJ_ACTIVEHIJ.A 20120213
TrendMicro-HouseCall TROJ_ACTIVEHIJ.A 20120214
ViRobot Doc.S.MS11-073.22016 20120213
Virustotal
SHA256: 48bc6c0df3302f7eaa6061c4f3b0357b4c512d5bd6f6088abc6fc274f2efc5aa
SHA1: 8f86b7fcaf0c1ee9b795fa8e559def47ef468128
MD5: 60068812b59e58d6338aaebd649f9020
File size: 124.0 KB ( 126976 bytes )
File name: fputlsat.dll
File type: Win32 DLL
Detection ratio: 28 / 43
Analysis date: 2012-02-15 04:10:02 UTC ( 23 minutes ago )
AhnLab-V3 Win-Trojan/Activehijack.126976 20120213
AntiVir TR/Drop.Kaliox.A 20120213
Avast Win32:Malware-gen 20120214
BitDefender Trojan.Generic.KD.529689 20120214
DrWeb Trojan.MulDrop3.34467 20120214
Emsisoft Trojan-Dropper.Win32.Agent!IK 20120214
F-Secure Trojan.Generic.KD.529689 20120214
Fortinet W32/Agent.PRG!tr 20120214
GData Trojan.Generic.KD.529689 20120214
Ikarus Trojan-Dropper.Win32.Agent 20120214
K7AntiVirus Riskware 20120213
Kaspersky Trojan-Dropper.Win32.Agent.gjnt 20120214
McAfee Generic Dropper.p 20120214
McAfee-GW-Edition Artemis!60068812B59E 20120213
Microsoft TrojanDropper:Win32/Kaliox.A 20120213
NOD32 Win32/TrojanDropper.Agent.PRG 20120214
Norman W32/Agent.XGSO 20120213
nProtect Trojan-Dropper/W32.Agent.126976.CS 20120213
PCTools Trojan.Dropper 20120207
Symantec Trojan.Dropper 20120214
TrendMicro TROJ_MULDROP.IC 20120213
TrendMicro-HouseCall TROJ_MULDROP.IC 20120214
VIPRE Trojan.Win32.Generic!BT 20120214
ViRobot Trojan.Win32.Activehijack.126976 20120213
VirusBuster Trojan.DR.Agent!ly6ZRARwo6A
Virustotal
SHA256: 27c87e7993c5661dd3b65e51df5884519fc0234bf36de72082644fa909ccb793
SHA1: d0c3e34bd97c4aa56fe9f176954d274595926a32
MD5: d4859fc951652b3c9657f8621d4db625
File size: 13.5 KB ( 13824 bytes )
File name: iede32.ocx
File type: Win32 DLL
Detection ratio: 28 / 42
Analysis date: 2012-02-14 04:13:46 UTC ( 1 day, 2 hours ago )
0
AhnLab-V3 Win-Trojan/Activehijack.13824 20120213
AntiVir TR/Spy.13824.71 20120214
Antiy-AVL Trojan/Win32.Genome.gen 20120213
BitDefender Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Comodo TrojWare.Win32.GameThief.Nilage.~CRSH 20120214
DrWeb Trojan.Click2.13847 20120214
Emsisoft Trojan.Win32.Spy!IK 20120214
eSafe Win32.GenHeur.LP.Aq@ 20120213
F-Secure Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Fortinet W32/Agent.OLJ 20120214
GData Gen:Trojan.Heur.LP.aq4@aqXBVhe 20120214
Ikarus Trojan.Win32.Spy 20120214
K7AntiVirus Riskware 20120213
Kaspersky Trojan.Win32.Genome.aehtz 20120214
McAfee Generic Dropper.p 20120214
McAfee-GW-Edition Artemis!D4859FC95165 20120213
Microsoft TrojanDownloader:Win32/Kaliox.A 20120213
NOD32 Win32/Agent.OLJ 20120214
Norman W32/Troj_Generic.KIKX 20120213
nProtect Trojan/W32.Genome.13824.J 20120213
Sophos Troj/Spy-YL 20120214
Symantec Trojan.Gen.2 20120214
TheHacker Trojan/Agent.olj 20120213
TrendMicro BKDR_CONIP.A 20120214
TrendMicro-HouseCall BKDR_CONIP.A 20120214
ViRobot Trojan.Win32.Activehijack.13824 20120214
VirusBuster Trojan.Agent!KGIS/NcFcUc 20120213











No comments:
Post a Comment