Update:
Noticed an ineresting post by Nart Villeneuve (Internet Censorship
Explorer) regarding this malware and decided to update and resurrect the
post
 Download 4f681733fd9e473c09f967fa87c9faef EIDHR.xls and all the files described below as a password protected archive (contact me if you need the password)
Download 4f681733fd9e473c09f967fa87c9faef EIDHR.xls and all the files described below as a password protected archive (contact me if you need the password)From: david@humanright-watch.org [mailto:david@humanright-watch.org] On Behalf Of ??
Sent: Friday, May 28, 2010 2:31 AM
To: XXXXXX
Subject: 關於EIDHR項目
諸位
關於EIDHR歐洲人權項目我詳細咨詢了歐盟的朋友,爲了使申請能順利通過,還須補充一些資料,具體資料項目和内容概要都附在後面了,祝各位順利。
張英
From: SHARPE Simon (RELEX-BEIJING)
Sent: Monday, May 24, 2010 6:15 PM
Subject: FW: EIDHR 项目征求书
大家好:
欧盟现在有一个EIDHR的项目征求。项目的目的在于资助推动人权的项目,涵盖的领域很广泛。大家可以跟其他感兴趣的朋友分享这个信息。
项目活动的主题
具有以下主题的计划书会受到优先考虑:
1. 思考自由,宗教自由和信仰自由的权利
2. 言论和表达的自由,包括艺术和文化的表达,信息和沟通的权利,包括媒体自由,反对审查和网络自由
3. 和平集会和结社自由的权利,包括建立和参加工会的权利
4. 在一国境内自由行动的权利,离开任何国家(包括本国)和回到本国的权利
项目活动
项目活动可以包括从监督,倡导,公开信息,提高意识到能力建设,培训以及与利益攸关者对话等一系列形式。最终目标都是为了提高所在国的公民社会组织的自主权。
项目的资助总额最低为15万欧元,最高为120万欧元。项目的延续时间应不少于18个月,但不超过3年。比较重要的是附件中的项目指导,首先需要提交一个简短的项目概念书,申请的最后期限是6月15日。项目申请时要填写链接中的Annex A,B,C 等表格。
申请有两种方法:
1. 通过PADOR系统注册申请。http://ec.europa.eu/europeaid/onlineservices/pador/index_en.htm
2. 或将申请所需的项目概念书以及表格A,B,C寄往如下地址:
邮寄地址
European Commission
EuropeAid Co-operation Office
Unit F4 – Finances, Contracts and Audit for thematic budget lines
Call for Proposals Sector
Office: L-41 03/154
B - 1049 Brussels
BELGIUM
快递地址
European Commission
EuropeAid Cooperation Office
Unit F4 – Finances, Contracts and Audit for thematic budget lines
Call for Proposals Sector
Office: L-41 03/154
Central Mail Service
Avenue du Bourget 1
B-1140 Brussels (Evère)
BELGIUM
关于项目的具体内容在https://webgate.ec.europa.eu/europeaid/onlineservices/index.cfm?do=publi.welcome&nbPubliList=15&orderby=upd&orderbyad=Desc&searchtype=RS&aofr=126352
如果需要更多的信息,请随时与我们联系。谢谢!
欧盟驻华代表团夏明
See machine translation in the end
Headers
Received: (qmail 3230 invoked from network); 28 May 2010 06:31:58 -0000
Received: from static-ip-251-116-134-202.rev.dyxnet.com (HELO mx02.diaocha8.com) (202.134.116.251) by XXXXXXXXXXXXXXXXXXX with SMTP; 28 May 2010 06:31:58 -0000
Received: from sppfszwr (unknown [180.98.74.10])
by mx02.diaocha8.com (EMOS V1.5 (Postfix)) with ESMTPA id 37B71109A81
for
Reply-To:
Sender: david@humanright-watch.org
Message-ID:
From: =?utf-8?B?5by16Iux?=
To: XXXXXXXXXXXXXXX
Subject: =?utf-8?B?6Zec5pa8RUlESFLpoIXnm64=?=
Date: Fri, 28 May 2010 14:31:10 +0800
Received: from static-ip-251-116-134-202.rev.dyxnet.com (HELO mx02.diaocha8.com) (202.134.116.251) by XXXXXXXXXXXXXXXXXXX with SMTP; 28 May 2010 06:31:58 -0000
Received: from sppfszwr (unknown [180.98.74.10])
by mx02.diaocha8.com (EMOS V1.5 (Postfix)) with ESMTPA id 37B71109A81
for
Reply-To:
Sender: david@humanright-watch.org
Message-ID:
From: =?utf-8?B?5by16Iux?=
To: XXXXXXXXXXXXXXX
Subject: =?utf-8?B?6Zec5pa8RUlESFLpoIXnm64=?=
Date: Fri, 28 May 2010 14:31:10 +0800
Hostname: 180.98.74.10
ISP: CHINANET jiangsu province network
Organization: CHINANET jiangsu province network
State/Region: Jiangsu
City: Suzhou
-
File EIDHR.xls received on 2010.06.02 04:13:50 (UTC)
http://www.virustotal.com/analisis/8b8960a855603393190152439c64ac9fd16655b304d472ecb83422900369a266-1275452030
Result: 17/41 (41.47%)
a-squared 5.0.0.26 2010.06.02 Trojan-Dropper.MSExcel.Agent!IK
AntiVir 8.2.1.242 2010.06.01 TR/Drop.MSExcel.Agent.BC
Antiy-AVL 2.0.3.7 2010.06.01 Trojan/MSExcel.Agent
Authentium 5.2.0.5 2010.06.02 MSExcel/Dropper.B!Camelot
BitDefender 7.2 2010.06.02 Exploit.D-Encrypted.Gen
F-Secure 9.0.15370.0 2010.06.02 Exploit.D-Encrypted.Gen
GData 21 2010.06.02 Exploit.D-Encrypted.Gen
Ikarus T3.1.1.84.0 2010.06.02 Trojan-Dropper.MSExcel.Agent
Jiangmin 13.0.900 2010.05.31 Heur:Exploit.CVE-2009-3129
Kaspersky 7.0.0.125 2010.06.02 Trojan-Dropper.MSExcel.Agent.bc
McAfee-GW-Edition 2010.1 2010.06.02 Heuristic.BehavesLike.Exploit.X97.CodeExec.EBEB
Norman 6.04.12 2010.06.01 ShellCode.B
nProtect 2010-06-01.02 2010.06.01 Exploit.D-Encrypted.Gen
PCTools 7.0.3.5 2010.06.02 HeurEngine.MaliciousExploit
Symantec 20101.1.0.89 2010.06.02 Bloodhound.Exploit.306
TrendMicro 9.120.0.1004 2010.06.02 TROJ_MDROPR.MRV
TrendMicro-HouseCall 9.120.0.1004 2010.06.02 TROJ_MDROPR.MRV
Additional information
File size: 64166 bytes
MD5...: 4f681733fd9e473c09f967fa87c9faef
Excel successfully opens, displaying hello, and a Chinese font set as default. The properties show that it was created on a Lenovo (Beijing) Limited laptop.
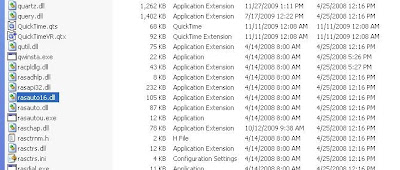
Files created
- D52EF63FDC5C5452D9DA23BD6D4BF0F5 %userprofile%\Local Settings\Temp\1001.tmp11kb 0/41 Virustotal
- D52EF63FDC5C5452D9DA23BD6D4BF0F5 C:\WINDOWS\ntshrui.dll 11kb 0/41 Virustotal
- A363ABE09A44176386C50EE887359270 %userprofile%\Local Settings\Temp\set.xls 17kb -clean spreadsheet
you see above