Common Vulnerabilities and Exposures (CVE)number
CVE-2010-2883 Stack-based buffer overflow in CoolType.dll in Adobe Reader and Acrobat 9.x before 9.4, and 8.x before 8.2.5 on Windows and Mac OS X, allows remote attackers to execute arbitrary code or cause a denial of service (application crash) via a PDF document with a long field in a Smart INdependent Glyphlets (SING) table in a TTF font, as exploited in the wild in September 2010. NOTE: some of these details are obtained from third party information.
General File Information
File Event Invitation from Heritage.pdf
MD5 529AE8C6AC75E555402AA05F7960EB0D
SHA1 d793f0c3e051bc03b0cd5e2c2f87f3be33612d49
File size : 358996
Type: PDF
Distribution: Email attachment
Download
Original Message
From: Elizabeth XXXXXX [mailto:XXXXX@heritage.org]
Sent: Friday, November 19, 2010 3:53 AM
To: XXXXXXXXXXXXXX
Subject: Event Invitation from The Heritage Foundation: The Implications of Taiwan's Big City Elections
Dear Madam / Sir,
You are cordially invited to attend the Event of The Heritage Foundation on Dec 01, 2010: The Implications Of Taiwan's Big City Elections.
Please refer to the attached invitation and visit the Heritage site for event details.
Thanks,
________________________________________
Elizabeth XXXXXXX
Administrative Assistant
Asian Studies Center
The Heritage Foundation
214 Massachusetts Avenue, NE
Washington, DC 20002
XXXXXXXXXXXX
heritage.org
Message Headers
Received: (qmail 25793 invoked from network); 19 Nov 2010 08:53:27 -0000
Received: from msr19.hinet.net (HELO msr19.hinet.net) (168.95.4.119)
by XXXXXXXXXXXX with SMTP; 19 Nov 2010 08:53:27 -0000
Received: from elizabethhamrickpc (61-222-104-222.HINET-IP.hinet.net [61.222.104.222])
by msr19.hinet.net (8.9.3/8.9.3) with ESMTP id QAA04206
for ; Fri, 19 Nov 2010 16:53:09 +0800 (CST)
Reply-To: newscomeon@yahoo.com
From: "Elizabeth Hamrick"
To: XXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Subject: Event Invitation from The Heritage Foundation: The Implications of Taiwan's Big City Elections
Date: Fri, 19 Nov 2010 16:53:09 +0800
Message-ID:
MIME-Version: 1.0
Content-Type: multipart/mixed;
boundary="----=_NextPart_10111916482235810322685_000"
X-Priority: 3
X-Mailer: DreamMail 4.6.6.0
Sender
61.222.104.222
Hostname: 61-222-104-222.hinet-ip.hinet.net
ISP: CHTD, Chunghwa Telecom Co., Ltd.
Organization: Wei Kai Shi Ye Ltd.
Proxy: None detected
Type: Broadband
Assignment: Static IP
Country: Taiwan
Automated Scans
File name: Event Invitation from Heritage.pdf
Submission date: 2010-11-25 04:42:08 (UTC)
Current status: finished
Result: 16 /43 (37.2%)
AntiVir 7.10.14.99 2010.11.24 EXP/Pidief.ddi
Antiy-AVL 2.0.3.7 2010.11.25 Exploit/Win32.Pidief
AVG 9.0.0.851 2010.11.24 Exploit_c.MGG
BitDefender 7.2 2010.11.25 Exploit.PDF-TTF.Gen
eTrust-Vet 36.1.7998 2010.11.24 PDF/CVE-2010-1297.B!exploit
F-Prot 4.6.2.117 2010.11.24 File is damaged
F-Secure 9.0.16160.0 2010.11.25 Exploit.PDF-TTF.Gen
GData 21 2010.11.25 Exploit.PDF-TTF.Gen
Kaspersky 7.0.0.125 2010.11.25 Exploit.Win32.Pidief.ddi
Microsoft 1.6402 2010.11.24 Exploit:Win32/CVE-2010-2883.A
nProtect 2010-11-24.01 2010.11.25 Exploit.PDF-TTF.Gen
PCTools 7.0.3.5 2010.11.25 HeurEngine.MaliciousExploit
Sophos 4.60.0 2010.11.25 Troj/SWFExp-X
SUPERAntiSpyware 4.40.0.1006 2010.11.25 -
Symantec 20101.2.0.161 2010.11.25 Bloodhound.Exploit.357
TrendMicro 9.120.0.1004 2010.11.24 TROJ_PIDIEF.HKD
TrendMicro-HouseCall 9.120.0.1004 2010.11.25 TROJ_PIDIEF.HKD
MD5 : 529ae8c6ac75e555402aa05f7960eb0d
CVE ID
Let me know if you have any comments, additions or corrections here --
The file uses a pdf (1.pdf) embedded in the original "Event Invitation from Heritage.pdf"
FILE 1. Event Invitation from Heritage.pdf 529ae8c6ac75e555402aa05f7960eb0d
Screenshot from our PDF - note jit-egg.swf as in the PoC by Asintsev
Compressed Flash in Event Invitation from Heritage.pdf
-------------------------------------------------------------------------------------------
FILE 2 73E8F3BB63B16E5830528D226FBC9998
1.pdf - CVE-2010-2883 - this file did not create any files during my testing and I did not analyse it further. If you have any comments or additions, please send.
The file uses a pdf (1.pdf) embedded in the original "Event Invitation from Heritage.pdf"
FILE 1. Event Invitation from Heritage.pdf 529ae8c6ac75e555402aa05f7960eb0d
obj 1 0
Type:
Referencing:
Contains stream
;9F7DF03346B2A4799ADF0EE158A1F80C>/CreationDate(D:20100920103657+08'00')/ModDate(D:20100923164332+08'00')/Size 1171>>/Subtype/application#2Fx-shockwave-flash
/DL 1171
/Length 1171
/Params /CheckSum<9F7DF03346B2A4799ADF0EE158A1F80C>
/CreationDate (D:20100920103657+08'00')
/ModDate (D:20100923164332+08'00')
/Size 1171
9F7DF03346B2A4799ADF0EE158A1F80C>/CreationDate(D:20100920103657+08'00')/ModDate(D:20100923164332+08'00')/Size 1171>>/Subtype/application#2Fx-shockwave-flash>>stream
CWS c xÚ•ÖYl U àûό玗Ävâ8[÷6]B œn@ÙÚ,„„ CJÚ
ñØ 'N ǵ'IÚ¦ BBHˆ $ÊŽ@PD%Ä ¼ $Ä. !±K ñD±ë3R9’Uá 3ž¹Ççž»Ìä„ÿI!Ž/ŠfˆÞ !„8 Úæ •O@tŠ£ø ¿âgX ë Æ7¿`å[ 6î
- Please read about the technique at JIT-SPRAY Attacks & Advanced Shellcode Security HITBSecConf2010, Amsterdam by Alexey Sintsov
- Alexey Sintsov's egg-hunter JIT shellcode generator for Flash 10.0.x is here --
- as pointed by Malware Tracker blog - he described a similar case: Hiding PDF Exploits by embedding PDF files in streams and Flash ROP heapsprays
- Also Symantec blog had an article about this kind of malicious pdf in October, 2010
Event Invitation from Heritage.pdfAccording to Symantec, "A more advanced technique is to use a PDF file embedded in a PDF file. The third object contains a stream indicating “application/pdf” as a sub-byte. With “FlateDecode”, this PDF file is compressed by using Zlib/deflates. To identify the PDF exploiting this vulnerability, it should be inflated and parsed by the PDF parser again.The PDF embedded in a PDF file is always the same one and it is just used to trigger the vulnerability. We detect PDF malware using this technique as Bloodhound.Exploit.357 as well." - Symantec, by Kazumasa Itabashi
Screenshot from our PDF - note jit-egg.swf as in the PoC by Asintsev
Compressed Flash in Event Invitation from Heritage.pdf
-------------------------------------------------------------------------------------------
FILE 2 73E8F3BB63B16E5830528D226FBC9998
1.pdf - CVE-2010-2883 - this file did not create any files during my testing and I did not analyse it further. If you have any comments or additions, please send.
Files Created
%Temp%\A9R1AA.tmp\1.pdf
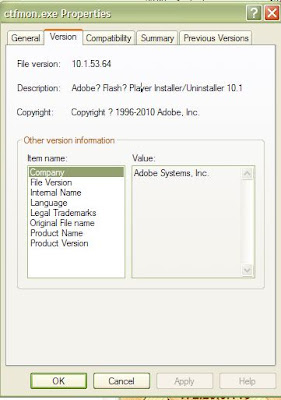
%Temp%\ctfmon.exe
File name:ctfmon.exe
http://www.virustotal.com/file-scan/report.html?id=fb0dc16f74061304d50f2404913ad836d59a92b9543c3a3aef91da4c2b8511aa-1291295776
Submission date:2010-12-02 13:16:16 (UTC)
Result:17 /43 (39.5%)
AhnLab-V3 2010.12.02.07 2010.12.02 Win-Trojan/Agent.32768.BUO
AVG 9.0.0.851 2010.12.02 Dropper.Generic2.BOYA
BitDefender 7.2 2010.12.02 Gen:Variant.Downloader.19
DrWeb 5.0.2.03300 2010.12.02 Win32.HLLW.Autoruner.27746
Emsisoft 5.0.0.50 2010.12.02 Trojan-Downloader.Win32.Small!IK
F-Secure 9.0.16160.0 2010.12.02 Gen:Variant.Downloader.19
GData 21 2010.12.02 Gen:Variant.Downloader.19
Ikarus T3.1.1.90.0 2010.12.02 Trojan-Downloader.Win32.Small
Jiangmin 13.0.900 2010.12.02 TrojanDownloader.Small.avnm
NOD32 5666 2010.12.02 a variant of Win32/Injector.DKT
Norman 6.06.10 2010.12.02 W32/Malware
nProtect 2010-12-02.01 2010.12.02 Trojan-Downloader/W32.Small.32768.GW
Panda 10.0.2.7 2010.12.01 Suspicious file
Sophos 4.60.0 2010.12.02 Troj/Buzus-EI
TrendMicro 9.120.0.1004 2010.12.02 TROJ_INJECTR.SMA
TrendMicro-HouseCall 9.120.0.1004 2010.12.02 TROJ_INJECTR.SMA
ViRobot 2010.12.2.4181 2010.12.02 Backdoor.Win32.Generic.32768
Additional information
MD5 : 818bcf2a6c0680e91f774de404a2ad99
http://anubis.iseclab.org/?action=result&task_id=1c849d6ba2acff7848d1db3986dd317ac&call=first
File: 1.pdf
http://www.virustotal.com/file-scan/report.html?id=18d3b53694cdd4674af02f336e939bc4a6f0dbae80f860a3266a74ba81a4f6a2-1291381162
Size: 36407
MD5: 73E8F3BB63B16E5830528D226FBC9998
Submission date:2010-12-03 12:59:22 (UTC)
Result:16/ 43 (37.2%)
Antiy-AVL 2.0.3.7 2010.12.03 Exploit/Win32.Pidief
AVG 9.0.0.851 2010.12.03 Exploit_c.NCO
BitDefender 7.2 2010.12.03 Exploit.PDF-TTF.Gen
Emsisoft 5.0.0.50 2010.12.03 Exploit.Win32.Pidief!IK
F-Secure 9.0.16160.0 2010.12.03 Exploit.PDF-TTF.Gen
Fortinet 4.2.254.0 2010.12.03 PDF/CoolType!exploit.CVE20102883
GData 21 2010.12.03 Exploit.PDF-TTF.Gen
Ikarus T3.1.1.90.0 2010.12.03 Exploit.Win32.Pidief
Kaspersky 7.0.0.125 2010.12.03 Exploit.Win32.Pidief.ddi
Microsoft 1.6402 2010.12.03 Exploit:Win32/CVE-2010-2883.A
nProtect 2010-12-03.01 2010.12.03 Exploit.PDF-TTF.Gen
PCTools 7.0.3.5 2010.12.03 HeurEngine.MaliciousExploit
Symantec 20101.2.0.161 2010.12.03 Bloodhound.Exploit.357
TrendMicro 9.120.0.1004 2010.12.03 TROJ_PIDIEF.HKD
TrendMicro-HouseCall 9.120.0.1004 2010.12.03 TROJ_PIDIEF.HKD
Additional information
MD5 : 73e8f3bb63b16e5830528d226fbc9998
Vicheck Scan
https://www.vicheck.ca/md5query.php?hash=73e8f3bb63b16e5830528d226fbc9998
Result: Suspicious file - PDF Exploit font SING table CVE-2010-2883
Network activity
202.3.167.6
Hostname: 202-3-167-6-static.unigate.net.twISP: Network topology of Unigate Telecom Inc.
Organization: Network topology of Unigate Telecom Inc.
Proxy: None detected
Type: Broadband
Assignment: Static IP
Country: Taiwan
202.60.203.229
Hostname: 202.60.203.229ISP: T.C.C Technology Co., Ltd.
Organization: T.C.C Technology Co., Ltd.
Proxy: None detected
Type: Broadband
Assignment: Static IP
Country: Thailand
State/Region: Krung Thep
City: Bangkok













Excellent .. I guess you *do* see the same sun no matter where you are in the world.
ReplyDeletePlease keep up the good work!