Download 50b9bee0213917e52d32d82907234aeb invitation.pdf as a password protected archive (please contact me if you need the password)
Details 50b9bee0213917e52d32d82907234aeb invitation.pdf
Please see a detailed analysis of this pdf by Villy on Bugix-security.blogspot.com:
CVE-2010-0188 - Adobe Pdf LibTiff Exploit (Remote Code Execution)
From: SABRENA [mailto:sabrena66@yahoo.com.tw]
Sent: 2010-03-09 5:28 PM
To: XXX@sais-jhu.edu
Subject: formal invitation letter
attached is the copy of the formal invitation letter and response card.
Meanwhile We have send you the formal invitation letter by post
according to your correspondence address. Please check your mailbox in the
next few days.
Sincerely yours
Wang Xiaoxue
========================
CVE-2010-0188 Exploit
Here are a few details from Villy who reversed the file (thanks, Villy)
"The sample contains an embeded tiff file (with vulnerability
CVE-2006-3459).
Possibly they used this code to generate the tiff file. The shellcode is in the tiff file.
http://downloads.securityfocus.com/vulnerabilities/exploits/19283.c
The following proof of concept video was created to show the exploit in action.
It was tested on Adobe Reader 9.0-9.3, on Windows XP, Vista, and Windows 7.
Windows XP with Adobe Reader 9.3.0 and below is vulnerable
Windows XP with Adobe Reader 9.3.1 is not vulnerable
Vista and Windows 7 are not vulnerable even with 9.3.0 - Adobe Reader just crashes but nothing else.
This exploit works with javascript disabled.For more details see his post at
http://bugix-security.blogspot.com CVE-2010-0188 - Adobe Pdf LibTiff Exploit (Remote Code Execution)
====================
Headers
Received: from [
60.216.233.216] by web72903.mail.tp2.yahoo.com via HTTP; Wed, 10 Mar 2010 06:27:34 CST
X-Mailer: YahooMailRC/300.3 YahooMailWebService/0.8.100.260964
Date: Wed, 10 Mar 2010 06:27:34 +0800
From: SABRENA
Reply-To: SABRENA
Subject: formal invitation letter
Hostname: 60.216.233.216
http://www.robtex.com/ip/60.216.233.216.html#whois
ISP: China Unicom Shandong province network
Organization: China Unicom Shandong province network
Country: China
State/Region: Shandong
City: Jinan
Virustotal result #1 - March 9, 2010
http://www.virustotal.com/analisis/feb8ee83587c61f4f53d2b0bcd39ca7c79666d1903c3dcdc53cbff94f0c90198-1268177735
File
invitation.pdf received on
2010.03.09 23:35:35 (UTC)
Result:
0/42 (0.00%)
Virustotal result #2 -March 11, 2010
File
invitation.pdf received on
2010.03.11 12:47:20 (UTC)
Current status:
finished
Result: 1/42 (2.38%)
Symantec 20091.2.0.41 2010.03.11 Trojan.Pidief.I
File size: 225787 bytes
MD5 : 50b9bee0213917e52d32d82907234aeb
=======================================================
This PDF appears to deliver Poison Ivy Remote Administration tool / backdoor type of malware
The following files get created on the exploited system
%System%\pe.dll
%System%\sens32.dll
%System%2\srvlic.dll
C:\data.bIN
C:\data.exe
%System%\pe.dll - injected in svchost process
Virustotal scans
%System%\pe.dll --5573689815aebfe7cbd2e3829054a5f0
%System%\sens32.dll --5573689815aebfe7cbd2e3829054a5f0
http://www.virustotal.com/analisis/25b0a8bb9c445e8ff2f93b37ad2792894ea1ef6b9dc5c89efd08a94cf9806bbb-1268343284
Result:
12/42 (28.58%)
AntiVir 8.2.1.180 2010.03.11
TR/Dldr.Agent.9216.5
BitDefender 7.2 2010.03.11
Trojan.Downloader.Agent.ZCR
eSafe 7.0.17.0 2010.03.11
Win32.Downloader.Age
F-Secure 9.0.15370.0 2010.03.11
Trojan.Downloader.Agent.ZCR
GData 19 2010.03.11
Trojan.Downloader.Agent.ZCR
McAfee 5917 2010.03.11
Generic BackDoor!cdn
McAfee+Artemis 5917 2010.03.11
Generic BackDoor!cdn
McAfee-GW-Edition 6.8.5 2010.03.11
Trojan.Dldr.Agent.9216.5
Microsoft 1.5502 2010.03.11
Backdoor:Win32/Poison.M
Panda 10.0.2.2 2010.03.11
Suspicious file
Rising 22.38.03.04 2010.03.11
Trojan.Win32.Generic.51FAA70A
Symantec 20091.2.0.41 2010.03.11
Suspicious.Insight
Additional information
File size: 9216 bytes
MD5...: 5573689815aebfe7cbd2e3829054a5f0
%System%2\srvlic.dll
http://www.virustotal.com/analisis/54962ca9c6c1815342d3bc47608ce5df997903aa53805f636361178f6b0a6c73-1268343232
Result:
1/42 (2.39%)
Symantec 20091.2.0.41 2010.03.11 Suspicious.Insight
File size: 3072 bytes
MD5...: 346754de64df87eb7709b168d04f8daf
C:\data.bIN
http://www.virustotal.com/analisis/d6c3a05e39ff7d48e77adec5a1fad0fca1b256a171b4d863bd34884345a087d3-1268343177
Result:
0/42 (0%)
File size: 91756 bytes
MD5...: 3c924ce0fc74b39d04822f4d26640311
C:\data.exe
http://www.virustotal.com/analisis/1b0d5103e2f621870f407bec6310069044f890a1f2a215468b09eb8182647016-1268342979
File data.EXE received on 2010.03.11 21:29:39 (UTC)
Result:
5/41 (12.2%)
McAfee+Artemis 5917 2010.03.11
Artemis!8557321BF6EC
McAfee-GW-Edition 6.8.5 2010.03.11
Heuristic.BehavesLike.Win32.CodeInjection.L
Rising 22.38.03.04 2010.03.11
Trojan.Win32.Generic.51FAA6DF
Sunbelt 5827 2010.03.11
Trojan.Win32.Generic!SB.0
Symantec 20091.2.0.41 2010.03.11
Suspicious.Insight
File size: 32768 bytes
MD5...: 8557321bf6ec39b0cb4ac9a9441d0487
TCP traffic - 202.59.152.123:443
Information from Robtex.com
202.59.152.123
Hostname: idc-123-152-59-202.hkt.cc
ISP: First Network Communications Limited, ISP at HK
Organization: First Network Communications Limited, ISP at HK
Country: Hong Kong
City: Central District
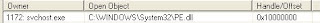
Some screenshots
Displayed PDF - note
data.bIN as the name
 Whois
http://www.robtex.com/ip/202.59.152.123.html#whois
inetnum: 202.59.152.0 - 202.59.159.255
Whois
http://www.robtex.com/ip/202.59.152.123.html#whois
inetnum: 202.59.152.0 - 202.59.159.255
netname: NET-FTG
descr: Forewin Telecom Group Limited
descr: ISP at HK
country: HK
admin-c: LC873-AP
tech-c: LC846-AP
status: ALLOCATED PORTABLE
mnt-by: APNIC-HM
mnt-lower: MAINT-HK-FTG
mnt-routes: MAINT-HK-FTG
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
remarks: This object can only be updated by APNIC hostmasters.
remarks: To update this object, please contact APNIC
remarks: hostmasters and include your organisation's account
remarks: name in the subject line.
remarks: -+-+-+-+-+-+-+-+-+-+-+-++-+-+-+-+-+-+-+-+-+-+-+-+-+-+
changed: hm-changed@apnic.net 20060712
changed: hm-changed@apnic.net 20060901
changed: hm-changed@apnic.net 20070222
changed: hm-changed@apnic.net 20091020
source: APNIC
route: 202.59.152.0/21
descr: Forewin Telecom Group Limited, ISP at HK
origin: AS38186
mnt-by: MAINT-HK-FTG
changed: hostmaster@hkt.cc 20090306
source: APNIC
person: Edward Poon
nic-hdl: LC873-AP
e-mail: edward@hkt.cc
address: RM 6A, 25/F, Cable TV Tower
address: 9 Hoi Shing RD, Tsuen Wan
address: N.T. Hong Kong
address:
address: + Please send spam and abuse reports to
address: + < abuse@hkt.cc >
address:
phone: +852-23631363
fax-no: +852-81673882
country: HK
changed: hostmaster@hkt.cc 20091012
mnt-by: MAINT-HK-FTG
source: APNIC
person: Larry Chan
nic-hdl: LC846-AP
e-mail: ckchan@hkt.cc
address: RM 6A, 25/F, Cable TV Tower
address: 9 Hoi Shing RD, Tsuen Wan
address: N.T. Hong Kong
address:
address: + Please send spam and abuse reports to
address: + < abuse@hkt.cc >
address:
phone: +852-23631363
fax-no: +852-81673882
country: HK
changed: hostmaster@hkt.cc 20091012
mnt-by: MAINT-HK-FTG
source: APNIC