The following article was written and published by Donato "ratsoul"
Ferrante (www.inreverse.net)
on April 13, 2010. His recent java analysis publications
attracted attention of the exploit kit owners who launched a heavy DDoS
attack on April 16, 2010 (this is their new blog - replacing www.inreverse.net) . DDoS is still in progress today, April
25, 2010. They sent their demands - remove the analysis articles
because it hurts their 'business'.
www.inreverse.net
is currently inaccessible, therefore, we are publishing the
InReverse java analysis here (this is Post #5) but this time together
with the malware samples provided by the InReverse crew. We
ask antivirus and security companies to download, analyze, and develop
protection (if you have not done yet). Thank you.
Donato "ratsoul"
Ferrante can be reached at ratsoul -at- inreverse-net
Download 9 files listed below as a password protected archive (please contact me for the password, if you need it)
All Virustotal scan results are from April 25, 2010. Compare to the initial scan results of some of the samples (1/42 a 0/42 - see post #5
- 8d499308df04932ed1b58a78417d6fb9.jar from JAVA Exploit Kit Malware #1 Post #1 Virustotal 26/40
- 7e92d280472ca426aff1c20fbeb8d2db.jar from JAVA Mobile Malware #1 Post #2 Virustotal 17/41
- 38f083169319d0141532db992d295448.jar from JAVA Sound malware Post #3 Virustotal 11/41
- 52586e8a85188a0ada59294650c91362.jar from JAVA Sound malware Post #3 Virustotal 19/41
- 3af7627af6348a76d1bf3b7bf31514e0.jar from JAVA malware family Post #4 Virustotal 20/38
- a022524cb52223a939ba50043d90ff94.jar from JAVA malware family Post #4 Virustotal 21/39
- d45a156c76f3c34bac0cf22cb586fdd1.jar from JAVA malware family Post #4 Virustotal 16/40
- 2138bfc0c92b726a13ff5095bd2f2b72.jar from JAVA Malware evading decompilation Post #5 Virustotal 11/39
- a0585edf638f5d1c556239d3bfaf08db.jar from JAVA Malware evading decompilation Post #5 Virustotal 10/40
----------------------------------------
Tuesday, April 13, 2010
Donato "ratsoul" Ferrante
JAVA Malware evading decompilation
Hello,
some days ago Param (thanks!) one of our blog readers sent me a couple of undetected JAVA malwares, which I'm going to analyze, the md5 are:
(Sample 1) 2138bfc0c92b726a13ff5095bd2f2b72
(Sample 2) a0585edf638f5d1c556239d3bfaf08db
At this time, both of this malware have a low detection, the first one 1/42 and the second one 0/42 from VirusTotal.
One of the interesting things is that if you try to decompile these samples by using jD you will get the following notice:So after a little investigation I figured out the reason. The reason is that jD is unable to handle methods with a large body.
Is it a problem ? No. To proceed with the analysis we can summon JAD. In fact by using JAD we can obtain the full code. Here are some snippets taken from the two samples.
(I will go fast on the analysis, at the end of the post you can find a couple of links with more details about these malwares.)
Sample 1:
([CVE-2009-3867])
Imports reveal a lot of information about what the malware is trying to "use"...
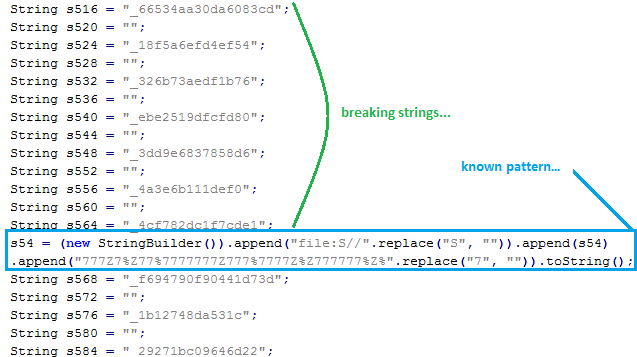
A lot of strings and a known pattern..Here is the shellcode...And the exploitation...Sample 2:
([CVE-2008-5353] )
Again the imports are telling us that the malware will try to load "untrusted" class..Here the malware gets data and cc fields...This is the strategy used to run the malware on the victim system:As we can see we have a long obfuscation that uses string replacements, scrambled names and base64 encoding.
In conclusion, both these malwares are using well known vulnerabilities being exploited since a while. These malwares still have no generic detections at all.
If you are interested you can read more in detail about these vulnerabilities in two of my previous posts here and here.
See ya!comments:
- [...] This post was mentioned on Twitter by Chae Jong Bin, In Reverse. In Reverse said: JAVA Malware evading decompilation : http://www.inreverse.net/?p=1028 [...]
Virustotal results on April 25, 2010
http://www.virustotal.com/analisis/d00fa63f4202a980ab4d854172eed4fce57fcf1fd5cff32e846107982573a91b-1272218810
File a0585edf638f5d1c556239d3bfaf08db. received on 2010.04.25 18:06:50 (UTC)
Result: 11/41 (26.83%)
Avast 4.8.1351.0 2010.04.25 Java:Djewers-L
Avast5 5.0.332.0 2010.04.25 Java:Djewers-L
eSafe 7.0.17.0 2010.04.25 Win32.Horse
Ikarus T3.1.1.80.0 2010.04.25 Trojan-Downloader.Java.Agent
McAfee 5.400.0.1158 2010.04.25 Exploit-CVE2008-5353
Sophos 4.53.0 2010.04.25 Troj/JavaDL-L
Sunbelt 6221 2010.04.25 Trojan.Java.Agent.c (v)
Symantec 20091.2.0.41 2010.04.25 Trojan Horse
TrendMicro 9.120.0.1004 2010.04.25 JAVA_BYTEVER.DP
TrendMicro-HouseCall 9.120.0.1004 2010.04.25 JAVA_BYTEVER.DP
File size: 43253 bytes
MD5...: a0585edf638f5d1c556239d3bfaf08db
http://www.virustotal.com/analisis/f95aeffa63f809a419dddc32c5bd65e28a1e6d21c587aef4342ac95c07bd9e80-1272218387
File 2138bfc0c92b726a13ff5095bd2f2b72. received on 2010.04.25 17:59:47 (UTC)
Result: 12/40 (30%)
Antiy-AVL 2.0.3.7 2010.04.23 Exploit/Java.CVE-2009-3867
eSafe 7.0.17.0 2010.04.25 Win32.Horse
F-Secure 9.0.15370.0 2010.04.25 Trojan-Downloader:Java/Agent.DIVS
Ikarus T3.1.1.80.0 2010.04.25 Exploit.Java.Agent
Kaspersky 7.0.0.125 2010.04.25 Exploit.Java.Agent.a
Norman 6.04.11 2010.04.25 JAVA/Byteverify.O
Sophos 4.53.0 2010.04.25 Troj/Agent-NBP
Sunbelt 6221 2010.04.25 Trojan.Java.Byteverify.c (v)
Symantec 20091.2.0.41 2010.04.25 Trojan Horse
TrendMicro 9.120.0.1004 2010.04.25 JAVA_BYTEVER.DP
TrendMicro-HouseCall 9.120.0.1004 2010.04.25 JAVA_BYTEVER.DP
ViRobot 2010.4.24.2293 2010.04.25 JS.EX-Agent.2276
File size: 32260 bytes
MD5...: 2138bfc0c92b726a13ff5095bd2f2b72
http://www.virustotal.com/analisis/fba57ff8cfed809e8fdc1b6647515090933f4dd6f1c3cc0b02d80044c6c50f7b-1272216836 File 38f083169319d0141532db992d295448. received on 2010.04.25 17:33:56 (UTC)
Result: 20/41 (48.79%)
a-squared 4.5.0.50 2010.04.25 Exploit.OSX.Smid.c!A2
AntiVir 8.2.1.224 2010.04.23 JAVA/Dldr.Agen.NA.1
Antiy-AVL 2.0.3.7 2010.04.23 Exploit/OSX.Smid
BitDefender 7.2 2010.04.25 Java.Exploit.Smid.A
Comodo 4678 2010.04.25 Exploit.Java.Agent.~A
DrWeb 5.0.2.03300 2010.04.25 Exploit.Java.10
eTrust-Vet 35.2.7448 2010.04.24 Java/ByteVerify!exploit
F-Secure 9.0.15370.0 2010.04.25 Exploit:OSX/Smid.B
GData 21 2010.04.25 Java.Exploit.Smid.A
Kaspersky 7.0.0.125 2010.04.25 Exploit.OSX.Smid.c
McAfee-GW-Edition 6.8.5 2010.04.23 Java.Dldr.Agen.NA.1
Microsoft 1.5703 2010.04.25 Trojan:Java/Classloader.T
NOD32 5059 2010.04.25 OSX/Exploit.Smid.B
nProtect 2010-04-25.01 2010.04.25 Java.Exploit.Smid.A
PCTools 7.0.3.5 2010.04.25 Trojan.ByteVerify
Sophos 4.53.0 2010.04.25 Troj/Clsldr-U
Symantec 20091.2.0.41 2010.04.25 Trojan.ByteVerify
TrendMicro 9.120.0.1004 2010.04.25 JAVA_BYTEVER.Y
TrendMicro-HouseCall 9.120.0.1004 2010.04.25 JAVA_BYTEVER.Y
VBA32 3.12.12.4 2010.04.23 Exploit.OSX.Smid.c
Additional information
File size: 1955 bytes
MD5...: 38f083169319d0141532db992d295448
http://www.virustotal.com/analisis/ce21ea5e25fe92ef6fa182c7fe588b050021796ea880e277aa7acd6e547f0994-1272218599
File 52586e8a85188a0ada59294650c91362. received on 2010.04.25 18:03:19 (UTC)
Result: 19/41 (46.35%)
Antivirus Version Last Update Result
a-squared 4.5.0.50 2010.04.25 Exploit.OSX.Smid.b!A2
AntiVir 8.2.1.224 2010.04.23 EXP/Java.mo.232
Antiy-AVL 2.0.3.7 2010.04.23 Exploit/OSX.Smid
BitDefender 7.2 2010.04.25 Java.Exploit.Smid.A
Comodo 4678 2010.04.25 Exploit.Java.Agent.~B
eTrust-Vet 35.2.7448 2010.04.24 JAVA/Smid.A
F-Secure 9.0.15370.0 2010.04.25 Exploit:Java/Agent.NHV
GData 21 2010.04.25 Java.Exploit.Smid.A
Ikarus T3.1.1.80.0 2010.04.25 Exploit.OSX.Smid
Kaspersky 7.0.0.125 2010.04.25 Exploit.OSX.Smid.b
McAfee-GW-Edition 6.8.5 2010.04.23 Exploit.Java.mo.232
Microsoft 1.5703 2010.04.25 Trojan:Java/Classloader.T
NOD32 5059 2010.04.25 OSX/Exploit.Smid.B
nProtect 2010-04-25.01 2010.04.25 Java.Exploit.Smid.A
PCTools 7.0.3.5 2010.04.25 Exploit.OSX.Smid.b
Symantec 20091.2.0.41 2010.04.25 Trojan.ByteVerify
TrendMicro 9.120.0.1004 2010.04.25 TROJ_SMID.B
TrendMicro-HouseCall 9.120.0.1004 2010.04.25 TROJ_SMID.B
File size: 1847 bytes
MD5...: 52586e8a85188a0ada59294650c91362
http://www.virustotal.com/analisis/b69f0e77a89df3af21c4ad2bae57cdf19dc01edea3cf2958931ebbbe4e428e99-1272241193
File 7e92d280472ca426aff1c20fbeb8d2db. received on 2010.04.26 00:19:53 (UTC)
Result: 17/41 (41.47%)
Antiy-AVL 2.0.3.7 2010.04.23 Trojan/J2ME.Swapi
Avast 4.8.1351.0 2010.04.25 Other:Malware-gen
Avast5 5.0.332.0 2010.04.25 Other:Malware-gen
Comodo 4678 2010.04.25 UnclassifiedMalware
DrWeb 5.0.2.03300 2010.04.26 Java.SMSSend.4
F-Secure 9.0.15370.0 2010.04.26 Riskware:Java/SmsSend.Gen!A
Fortinet 4.0.14.0 2010.04.25 Java/Swapi.KS!tr
GData 21 2010.04.26 Other:Malware-gen
Ikarus T3.1.1.80.0 2010.04.25 Trojan-SMS
Kaspersky 7.0.0.125 2010.04.26 Trojan-SMS.J2ME.Swapi.k
McAfee 5.400.0.1158 2010.04.26 JS/Downloader-Class.b
NOD32 5059 2010.04.25 probably a variant of Win32/Agent
PCTools 7.0.3.5 2010.04.26 Trojan.Generic
Symantec 20091.2.0.41 2010.04.26 Trojan Horse
TrendMicro 9.120.0.1004 2010.04.25 TROJ_SWAPI.E
TrendMicro-HouseCall 9.120.0.1004 2010.04.26 TROJ_SWAPI.E
VBA32 3.12.12.4 2010.04.23 Trojan-SMS.J2ME.Swapi.k
Additional information
File size: 2903 bytes
MD5...: 7e92d280472ca426aff1c20fbeb8d2db
http://www.virustotal.com/analisis/c52137b3dc1d700ee0b094b995b0da6d3bf13da40bca00d567209ce3cdd1a7cb-1272241740
File 3af7627af6348a76d1bf3b7bf31514e0. received on 2010.04.26 00:29:00 (UTC)
Result: 21/39 (53.85%)
AntiVir 8.2.1.224 2010.04.25 EXP/Java.Bytverif.I
Antiy-AVL 2.0.3.7 2010.04.23 Trojan/Java.Agent
Avast 4.8.1351.0 2010.04.25 Java:Agent-B
Avast5 5.0.332.0 2010.04.25 Java:Agent-B
BitDefender 7.2 2010.04.25 Java.Trojan.Exploit.Bytverify.I
ClamAV 0.96.0.3-git 2010.04.26 Trojan.JS.Selace-1
Comodo 4678 2010.04.25 UnclassifiedMalware
DrWeb 5.0.2.03300 2010.04.26 Exploit.Java.5
F-Secure 9.0.15370.0 2010.04.26 Java.Trojan.Exploit.Bytverify.I
GData 21 2010.04.26 Java.Trojan.Exploit.Bytverify.I
Ikarus T3.1.1.80.0 2010.04.25 Exploit.Java.BytVerify
Kaspersky 7.0.0.125 2010.04.26 Trojan-Downloader.Java.Agent.as
McAfee-GW-Edition 6.8.5 2010.04.25 Exploit.Java.Bytverif.I
Microsoft 1.5703 2010.04.25 Exploit:Java/CVE-2008-5353.C
NOD32 5059 2010.04.25 Java/TrojanDownloader.Agent.NAG
Norman 6.04.11 2010.04.25 JAVA/ByteVerify.A
PCTools 7.0.3.5 2010.04.26 Trojan.ByteVerify
Sophos 4.53.0 2010.04.26 Troj/ClsLdr-V
Symantec 20091.2.0.41 2010.04.26 Trojan.ByteVerify
TrendMicro 9.120.0.1004 2010.04.25 JAVA_BYTEVER.BN
TrendMicro-HouseCall 9.120.0.1004 2010.04.26 JAVA_BYTEVER.BN
Additional information
File size: 8397 bytes
MD5...: 3af7627af6348a76d1bf3b7bf31514e0
http://www.virustotal.com/analisis/eb4f3bd460824c701f3a99463a16e4307f5a4c111f1dc610d26db82d6436f842-1272242166
File 8d499308df04932ed1b58a78417d6fb9. received on 2010.04.26 00:36:06 (UTC)
Result: 28/41 (68.3%)
a-squared 4.5.0.50 2010.04.25 Trojan-Downloader.Java.OpenStream!IK
AntiVir 8.2.1.224 2010.04.25 JAVA/OpenStream.AE
Antiy-AVL 2.0.3.7 2010.04.23 Trojan/Java.OpenStream
Avast 4.8.1351.0 2010.04.25 Java:Agent-B
Avast5 5.0.332.0 2010.04.25 Java:Agent-B
AVG 9.0.0.787 2010.04.25 Java/OpenStream
BitDefender 7.2 2010.04.26 Trojan.Generic.IS.614610
Comodo 4678 2010.04.25 TrojWare.Win32.Trojan.Agent.~318
DrWeb 5.0.2.03300 2010.04.26 Exploit.CVE2008.5353
eSafe 7.0.17.0 2010.04.25 Win32.TrojanHorse
eTrust-Vet 35.2.7448 2010.04.24 Java/ByteVerify!exploit
F-Secure 9.0.15370.0 2010.04.26 Trojan.Generic.IS.614610
Fortinet 4.0.14.0 2010.04.25 Java/OpenStream.AD!tr.dldr
GData 21 2010.04.26 Trojan.Generic.IS.614610
Ikarus T3.1.1.80.0 2010.04.25 Trojan-Downloader.Java.OpenStream
Kaspersky 7.0.0.125 2010.04.26 Trojan-Downloader.Java.OpenStream.ad
McAfee 5.400.0.1158 2010.04.26 Exploit-ByteVerify
McAfee-GW-Edition 6.8.5 2010.04.25 Java.OpenStream.AE
Microsoft 1.5703 2010.04.25 Exploit:Java/CVE-2008-5353.B
NOD32 5059 2010.04.25 probably a variant of Win32/Agent
Norman 6.04.11 2010.04.25 Exploit/ByteVerify.A
nProtect 2010-04-25.01 2010.04.25 Trojan.Generic.IS.616012
PCTools 7.0.3.5 2010.04.26 Trojan.Generic
Sophos 4.53.0 2010.04.26 Troj/BytVrfy-C
Symantec 20091.2.0.41 2010.04.26 Trojan Horse
TrendMicro 9.120.0.1004 2010.04.25 JAVA_BYTEVER.AT
TrendMicro-HouseCall 9.120.0.1004 2010.04.26 JAVA_BYTEVER.AT
ViRobot 2010.4.24.2293 2010.04.25 Java.S.OpenStream.2238
Additional information
File size: 4519 bytes
MD5...: 8d499308df04932ed1b58a78417d6fb9
http://www.virustotal.com/analisis/e5daafafa3eedcff7577a1545a1e45fbaa964547cc46846f8d6ae90d9674ea4f-1272242459
File a022524cb52223a939ba50043d90ff94. received on 2010.04.26 00:40:59 (UTC)
Result: 23/41 (56.1%)
AntiVir 8.2.1.224 2010.04.25 JAVA/OpenStrem.BN.2
Antiy-AVL 2.0.3.7 2010.04.23 Trojan/Java.Agent
Avast 4.8.1351.0 2010.04.25 Java:Agent-B
Avast5 5.0.332.0 2010.04.25 Java:Agent-B
AVG 9.0.0.787 2010.04.25 Generic2_c.TEA
BitDefender 7.2 2010.04.26 Java.Trojan.Exploit.Bytverify.I
ClamAV 0.96.0.3-git 2010.04.26 Trojan.JS.Selace-1
Comodo 4678 2010.04.25 UnclassifiedMalware
DrWeb 5.0.2.03300 2010.04.26 Java.Siggen.11
eSafe 7.0.17.0 2010.04.25 Win32.Horse
eTrust-Vet 35.2.7448 2010.04.24 Java/ByteVerify!exploit
F-Secure 9.0.15370.0 2010.04.26 Java.Trojan.Exploit.Bytverify.I
GData 21 2010.04.26 Java.Trojan.Exploit.Bytverify.I
Ikarus T3.1.1.80.0 2010.04.25 Exploit.Java.BytVerify
Kaspersky 7.0.0.125 2010.04.26 Trojan-Downloader.Java.Agent.ay
McAfee-GW-Edition 6.8.5 2010.04.25 Java.OpenStrem.BN.2
Microsoft 1.5703 2010.04.25 Trojan:Java/Bytverify
NOD32 5059 2010.04.25 probably a variant of Win32/Agent
Norman 6.04.11 2010.04.25 JAVA/ByteVerify.A
Sophos 4.53.0 2010.04.26 Troj/ClsLdr-Gen
Symantec 20091.2.0.41 2010.04.26 Trojan Horse
TrendMicro 9.120.0.1004 2010.04.25 JS_BYTEVER.AT
TrendMicro-HouseCall 9.120.0.1004 2010.04.26 JS_BYTEVER.AX
Additional information
File size: 9417 bytes
MD5...: a022524cb52223a939ba50043d90ff94
http://www.virustotal.com/analisis/a19089a18db356fb5ef5cfa78b94a1fd8538381930c5998061d5176c77e136a0-1272243385
File d45a156c76f3c34bac0cf22cb586fdd1. received on 2010.04.26 00:56:25 (UTC)
Result: 16/40 (40.00%)
AntiVir 8.2.1.224 2010.04.25 JAVA/ClassLoad.AD.2
Antiy-AVL 2.0.3.7 2010.04.23 Trojan/Java.Agent
Avast 4.8.1351.0 2010.04.25 Java:Agent-B
Avast5 5.0.332.0 2010.04.25 Java:Agent-B
Comodo 4678 2010.04.25 TrojWare.Java.TrojanDownloader.Agent.av
DrWeb 5.0.2.03300 2010.04.26 Exploit.Java.8
eSafe 7.0.17.0 2010.04.25 Win32.ByteVerify
F-Secure 9.0.15370.0 2010.04.26 Trojan-Downloader:Java/Agent.NWB
Ikarus T3.1.1.80.0 2010.04.26 Trojan-Downloader.Java.Agent
Kaspersky 7.0.0.125 2010.04.26 Trojan-Downloader.Java.Agent.av
McAfee-GW-Edition 6.8.5 2010.04.25 Java.ClassLoad.AD.2
NOD32 5059 2010.04.25 probably a variant of Java/TrojanDownloader.Agent.NAI
Sophos 4.53.0 2010.04.26 Troj/ByteVer-I
Symantec 20091.2.0.41 2010.04.26 Trojan.ByteVerify
TrendMicro 9.120.0.1004 2010.04.25 TROJ_BYTEVER.BO
Additional information
File size: 7291 bytes
MD5 : d45a156c76f3c34bac0cf22cb586fdd1










No comments:
Post a Comment